Getting ready for the end of Basic Authentication in Exchange Web Services
Tech Republic Security
DECEMBER 19, 2019
Prepare your applications and users for big changes on 13 October 2020.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
DECEMBER 19, 2019
Prepare your applications and users for big changes on 13 October 2020.

CIO Business Intelligence
JUNE 27, 2022
Multi-factor authentication, or MFA. Multi-factor authentication requires users to provide two or more pieces of evidence in order to gain access to a network, application, or system, and can dramatically decrease the likelihood of infiltration. One of the best ways to ensure security? million to $4.24
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CIO Business Intelligence
MAY 19, 2022
Customer demand for passwordless authentication has grown exponentially since smartphones first began offering built-in biometric readers. A staggering 93% of consumers preferred biometric authentication to passwords — and yet so many companies still force their customers to use risky, outdated login credentials. Your first clue?

Network World
FEBRUARY 10, 2025
By 2020, the existing wireless infrastructure was struggling to keep pace with the demands of modern fans who were on their phones talking, texting, shooting videos, taking selfies, posting content on social media, checking out other online sites, and generally consuming huge amounts of bandwidth. Why Wi-Fi 6E? Wi-Fi 6 runs in the 2.4

Advertiser: ZoomInfo
Marketing and sales teams are feeling pressured to deliver authentic messaging to buyers at every point of their customer journey. This report aims to highlight the current state of B2B database and contact acquisition strategies and organizations’ goals to leverage data to fuel their go-to-market strategies in 2020 and beyond.

Network World
SEPTEMBER 25, 2020
It demands that executive agencies take "immediate and emergency action" to patch CVE-2020-1472 , issued August 11. The vulnerability is in Microsoft Windows Netlogon Remote Protocol (MS-NRPC), a core authentication component of Active Directory from Windows Server 2008 to Server 2019.

Network World
FEBRUARY 10, 2025
In January, DE-CIX reported record high data traffic in 2024, reaching 68 exabytes a 15% increase compared to 2023 and more than double the volume since 2020. For example, earlier this year, the company added two-factor authentication for customer portals. Thats a big money saver for them.
Network World
FEBRUARY 13, 2025
Gartner is more bullish, predicting that the market will grow at a 36% CAGR between 2020 and 2025 to reach $14.7 The security features of SASE can include encryption, multifactor authentication, threat protection, data leak prevention (DLP), DNS, Firewall-as-a-Service ( FWaaS ), Secure Web Gateway (SWG), and Zero Trust Network Access (ZTNA).

CIO Business Intelligence
MARCH 14, 2025
Case in point , in 2020, Russian cybercriminals tried to bribe a Tesla employee with $1 million to install ransomware in the companys systems. Multi-factor authentication (MFA) should no longer be optional, especially as BYOD has become the norm. What do human firewalls bring to the company table?

The Verge
AUGUST 15, 2020
Tesla CEO Elon Musk tweeted Friday that two-factor authentication for its app is “embarrassingly late” but apparently is now on the way. Musk didn’t provide a timeline, but said on Twitter that two-factor authentication — which adds an additional step to verify a user’s identity at sign-in— is in “final validation.”.

SecureWorld News
FEBRUARY 3, 2025
The operation, which took place on January 29, 2025, comes after years of illicit activity dating back to at least 2020, during which victimsprimarily in the United Statessuffered losses exceeding $3 million. Implementing Privileged Access Management (PAM) allows organizations to monitor and secure their most sensitive, critical accounts."

CIO Business Intelligence
MAY 28, 2022
Authentication problems are the most frustrating obstacles a customer will face online, and businesses must solve them if they want to increase their revenue and competitive edge. You might already have competitive prices, great customer service and a robust selection — but those hardly matter if customers get hung up on authentication.

CIO Business Intelligence
MAY 31, 2022
The metaverse will require a digital foundation that enables trust and authenticity. billion in 2020 , is expected to reach $184.5 Unreal” qualities are becoming intrinsic to AI, but bad actors are using it, too—from deepfakes to bots and more—so authenticity will be crucial to integration. Building trust. billion by 2030.

Forrester IT
APRIL 9, 2020
It is a humbling to work with a team of talented individuals like the ones I work with on Forrester’s Security & Risk team. This week, I’m highlighting 5 reports some of these fine folks published in Q1 that I got a lot of value out of, and I think you will too. Optimize […].

Tech Republic Cloud
DECEMBER 14, 2020
A major outage took down multiple Google websites and services including Gmail, Youtube and Nest on Monday December 14, 2020.

CIO Business Intelligence
MAY 26, 2022
Authentication problems are the most frustrating obstacles a customer will face online, and businesses must solve them if they want to increase their revenue and competitive edge. You might already have competitive prices, great customer service and a robust selection — but those hardly matter if customers get hung up on authentication.

CIO Business Intelligence
MAY 31, 2022
Indeed, passwordless authentication is worth celebrating, but every EOL requires a strategic plan to ensure a graceful transition. With the convenience and ease of passwordless authentication, it’s now possible to smooth the transition for your customers enough to achieve 100% adoption. This article explains how. That’s lost revenue.

Galido
NOVEMBER 24, 2019
Information Technology Blog - - 6 Internet Security Tips For 2020 - Information Technology Blog. Let’s take a look at some popular internet security tips for 2020. If you receive a threatening email, contact the merchant directly by typing in their link to confirm the authenticity of the email. Using Anti Malware Software.

SecureWorld News
FEBRUARY 13, 2025
Real-world cases of deepfake attacks Financial fraud : In 2020, a Hong Kong-based multinational firm lost $25 million when an employee was tricked into making wire transfers. Attacks on identity verification systems Bypassing biometric security: Many organizations use facial and voice recognition for authentication.

SecureWorld News
NOVEMBER 6, 2024
Google moved away from VPNs, instead using device-based authentication and continuous access verification, ensuring that each access request is authenticated. To gain support, highlight how Zero Trust mitigates current threats like the SolarWinds supply chain attack in 2020, which exposed vulnerabilities in traditional defenses.

The Verge
DECEMBER 28, 2020
TikTok has exploded in popularity in 2020 to become one of the biggest social media networks on the planet, with everything from internet memes, comedy sketches, and even a full-fledged Ratatouille musical. Do you secure your internet accounts with two-factor authentication? If not, go set up two-factor authentication now!

GeekWire
JULY 24, 2020
Winners of the 2020 GeekWire Awards make their acceptance speeches on the live-streamed event. And now … the winners in all 12 categories of the 2020 GeekWire Awards. — Adam Selipsky (@aselipsky) July 24, 2020. ” “I’mmmmmmm sorrrrrryyyyyyy, I was on mute” is the opera lyric for our times.

SecureWorld News
NOVEMBER 12, 2024
CVE-2023-27350 (PaperCut MF/NG): Allows a malicious cyber actor to chain an authentication bypass vulnerability with the abuse of built-in scripting functionality to execute code. CVE-2020-1472 (Microsoft Netlogon): Allows privilege escalation.

GeekWire
JUNE 27, 2023
Launched in 2020, OwnTrail’s social platform lets users map their career trajectory, highlighting important milestones in their professional growth, personal relationships and well-being. Bastian dubs OwnTrail as “ authentech ,” blending the words authentic and tech to describe its community-focused business model.

The Verge
NOVEMBER 29, 2021
eBay has bought out sneaker authentication service Sneaker Con, a company that gives sneaker-lovers the peace of mind that the kicks they’re purchasing are real. The acquisition builds upon eBay’s existing relationship with the service, which began back in October 2020 when eBay first launched its sneaker vetting process. Image: eBay.

SecureWorld News
NOVEMBER 20, 2020
NordPass, a password manager company, recently released its list of the worst passwords of 2020. The list also compares the worst passwords from 2019 to 2020 and shows what has increased or decreased in popularity. The list also compares the worst passwords from 2019 to 2020 and shows what has increased or decreased in popularity.

CIO Business Intelligence
AUGUST 14, 2023
Cherokee Nation had run digital campaigns in the past, but the systems in place could not authenticate citizenship, leaving a significant amount of manual labor behind each interaction. COVID-19 expedited the need for a digital platform to handle authentication and meet the spike in demand for assistance in the wake of a global pandemic.

CIO Business Intelligence
NOVEMBER 29, 2022
Consider customer authentication: you must verify the identity of each person who contacts your organization, right? This could be through knowledge-based authentication (ex: “What’s the city you were born in?”) What if you used AI and automation to offer an even more effective form of customer authentication like a 3D photo scan?

Forrester IT
JULY 11, 2023
While the conversation and action around diversity, inclusivity, and belonging spiked in 2020, CMOs still struggle with inclusive advertising practices.

Network World
AUGUST 21, 2024
Aaron Weismann joined Main Line Health as CISO in the summer of 2020 at the height of the pandemic, and the organization faced an enormous challenge. To solve the password-typing problem, for example, Main Line Health expanded its footprint of tokenized authentication. Some health care organizations are already doing this, he says.

The Verge
FEBRUARY 8, 2022
That’s the top-line finding four months into Google’s initiative to enroll users in two-factor authentication by default, detailed in a blog post to coincide with Safer Internet Day on February 8th. Although the number of web services supporting two-factor authentication has grown steadily, consumer adoption still remains low.

CIO Business Intelligence
MAY 23, 2023
Experts predict the post-COVID contact center workforce will be 60-80% work-from-home as organizations look to modernize the agent experience and contain costs (keep in mind this has no bearing on customer satisfaction: research shows CSAT stayed the same or improved for 75% of contact centers in 2020 and 63% in 2021).

Network World
DECEMBER 19, 2016
READ MORE ON NETWORK WORLD: 5 enterprise technologies that will shake things up in 2017 + Just take a look at some recent Gartner assessments of the security situation: By 2020, 60% of digital businesses will suffer major service failures, due to the inability of IT security teams to manage digital risk.

CIO Business Intelligence
JUNE 10, 2022
Phase one started around March 2020, when Covid forced massive changes to the workforce and, critically, demanded that those changes happen in far too little time. Remember that back in March 2020, many executives were operating on the belief that the disaster would blow over in a few weeks,” Ramezanian said. PHASE THREE.

CIO Business Intelligence
DECEMBER 20, 2023
After leaving Equinix in 2019, he hiked the Camino de Santiago in Spain, became a life coach through UC Davis Extension, and in 2020, took a Stanford philosophy course on the meaning of life. The importance of knowing who you are is at the very core of authentic leadership.” CIO, Innovation, IT Leadership, IT Strategy

CIO Business Intelligence
AUGUST 28, 2024
That’s part of a push to improve adoption of existing standards for email reputation, which rely on certificates for authentication, that the majority of organizations have simply ignored, even as email threats have increased. “It Building your machine identity strategy Enterprises are starting to pay attention, Wahlstrom says.

The Verge
JUNE 20, 2020
There are rumors of improvements to iCloud Keychain , Apple’s built-in password management tool, which could be getting 1Password-like features to remind users to regularly change their passwords and support for two-factor authentication. They’ve shown up plenty in previous iOS builds , but will they finally make an appearance at WWDC 2020?

The Verge
OCTOBER 14, 2020
Here’s a couple examples: Not only did sony break every ps4 due to how bad the update was, they're even recording us #PS4 pic.twitter.com/006eQznRdf — Mini (@_Minii17) October 14, 2020. pic.twitter.com/T0VIbwIpZe — TSN | Ittarra BooOda : Still recovering (@IttarraOda) October 14, 2020.

CIO Business Intelligence
MAY 17, 2022
The company launched its own migration to Amazon’s cloud in March 2020. Ciena is also exploring the possibility of using voice authentication and hopes to leverage Amazon Quick Sight’s interactive business intelligence dashboards to spot patterns and outliers powered by AWS machine learning capabilities.

The Verge
MAY 14, 2020
Epic Games Store (@EpicGames) May 14, 2020. According to the leaked tweet , Grand Theft Auto V will be available as a free download through May 21st: Tweet ad is deleted, so here you go pic.twitter.com/3oja0C3418 — Wario64 (@Wario64) May 14, 2020. pic.twitter.com/YlFUP3vQEy — Fortnite Status (@FortniteStatus) May 14, 2020.

TechSpot
JULY 8, 2020
On July 25, 2020, people from all walks of life are encouraged to film their day for the sequel. Whether it’s an ordinary day or a special day, it doesn’t matter – the team, comprised of executive producers Ridley Scott and Kai Hsuing along with director Kevin Macdonald – simply want authenticity.
Spearline Testing
MAY 10, 2021
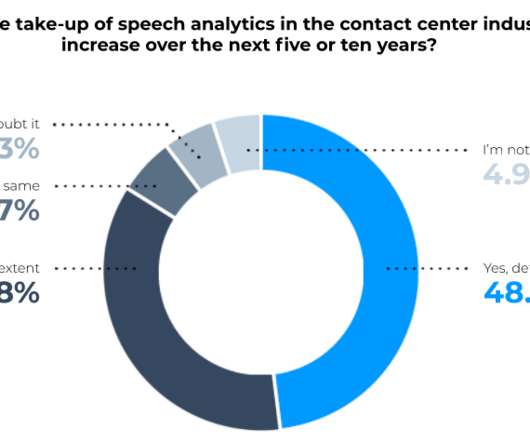
* This article is an excerpt taken from Spearline's Whitepaper ' 2020 Global Telecom's Report ' Businesses continue expanding their contact channels, and inbound voice is sometimes seen as outdated in this omnichannel world. Yet the inbound voice is far from obsolete.

CTOvision
JANUARY 6, 2016
Gartner predicts that number of IoT devices in use worldwide will grow from an estimated 5 billion in 2015 to some 25 billion connected devices by 2020. In 2016 there will be a growing number of authentic success stories where the IoT provides real value to consumers and enterprises. Trevor Daughney.

CIO Business Intelligence
OCTOBER 27, 2022
While at the NFL, she drove digital transformation, launched new businesses, and, among other feats, pulled off the virtual 2020 NFL Draft at the height of the COVID pandemic — in just three weeks. Authentic real leadership is what I hope we take out of COVID. And this generation just won’t accept anything less than that.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content