Your AST Guide for the Disenchanted: Part 6
ForAllSecure
NOVEMBER 3, 2020
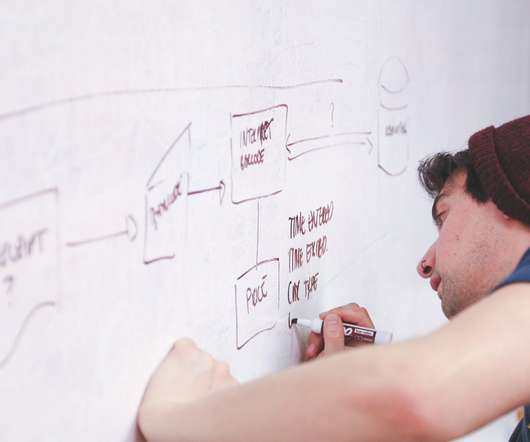
Generates a bill of materials for applications and the corresponding known vulnerabilities within them. Executes uncommon and unknown attack patterns against applications and monitors for anomalous behaviors. Application State During Testing. SDLC Phase. Request Demo Learn More. Software Composition Analysis (SCA).
























Let's personalize your content