Introducing Maintenance for Agile Applications
Information Week
MAY 3, 2024
At what point does continuous, iterative development for Agile applications turn into a maintenance exercise?
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Information Week
MAY 3, 2024
At what point does continuous, iterative development for Agile applications turn into a maintenance exercise?

CTOvision
FEBRUARY 4, 2014
Application Software Security. href="[link] Control 6: Application Software Security. Penetration Tests and Red Team Exercises. href="[link] Control 20: Penetration Tests and Red Team Exercises. Patching Applications: Patching of applications must be continuously maintained. Malware Defenses.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
CIO Business Intelligence
OCTOBER 5, 2023
Consider both the upsides and downsides to every disruptive innovation and develop applications that are smart, secure, and sustainable, without losing your focus on solving real-world challenges,” says Low Jin Phang, President, Digital Systems, ST Engineering. To find out more about ST Engineering Digital Systems, visit [link].

Network World
AUGUST 13, 2024
You can’t say you’ve tested unless you’ve exercised all these paths. Of 89 enterprise development managers who shared comments with me, all said they had to deal with this in their own testing, and they’d expect a software supplier to be even more careful than an end user. The same thing has to be considered in multi-cloud.

Social, Agile and Transformation
OCTOBER 6, 2009
I cover topics for Technologists from CIOs to Developers - agile development, agile portfolio management, leadership, business intelligence, big data, startups, social networking, SaaS, content management, media, enterprise 2.0 Ten Reasons Software Developers Need the Cloud. Developers need cloud development environments?

CIO Business Intelligence
JUNE 21, 2024
INE Security , a leading global cybersecurity training and cybersecurity certification provider, predicts large language model (LLM) applications like chatbots and AI-drive virtual assistants will be at particular risk. “AI As automated attacks increase, our defense strategies must also be automated and intelligent.

All Things Distributed
OCTOBER 2, 2017
Our straining database infrastructure on Oracle led us to evaluate if we could develop a purpose-built database that would support our business needs for the long term. Today, DynamoDB powers the next wave of high-performance, internet-scale applications that would overburden traditional relational databases.

GeekWire
JULY 5, 2023
Pioneer Square Labs in downtown Seattle hosted about 30 employees from Fortive for a week-long exercise to test out ideas for generative artificial intelligence businesses. The employees gathered customer feedback and developed a pitch by the end of the week. Fortive spun out of D.C.-based The Everett, Wash.-based

Network World
SEPTEMBER 18, 2024
By thinking and acting like attackers, red teams provide valuable insights into an organization’s security posture and help develop effective countermeasures. Improving overall security posture: The insights gained from red team exercises can be used to enhance security policies, procedures, and technologies.

CIO Business Intelligence
DECEMBER 20, 2023
Albeit emerging recently, the potential applications of GenAI for businesses are significant and wide-ranging. Generative AI can help businesses achieve faster development in two main areas: low/no-code application development and mainframe modernisation. percent of the working hours in the US economy.

Network World
JUNE 13, 2024
In the cyber world, this translates to performing lateral propagation to gain access to crown-jewel applications. Stage 4: This is when the thieves make their getaway with large sums of money, which is just like how cybercriminals steal large volumes of data from these crown-jewel applications that they can then use to commit extortion.

CTOvision
JUNE 4, 2015
DigitalGlobe is one of the community's most exiting and capable firms, providing space-based imagery and then related services, solutions and applications around that. They have also developed integrated solutions that bring in multiple sources of information into analyst workspaces for all source analysis.

CIO Business Intelligence
JULY 26, 2023
That said, many of the participants pointed out the need to develop a common enterprise-wide “cloud-native” approach to managing and securing their heterogeneous environments. This objective can be accomplished by inviting broader segments of the corporate community to security tabletop exercises.

Kitaboo
MARCH 30, 2023
This post aims to explore 12 such interesting applications of AI and AR in education. These AI tools are equipped to identify the various gaps in knowledge, followed by developing instructions, testing, and powerful feedback systems for students at every stage of their learning journey. Let’s begin.

CIO Business Intelligence
JULY 5, 2024
We developed an algorithm to measure our different applications based on these 12 categories so we can eliminate technical debt via a more strategic and standardized approach,” she says, noting that the goal was to do away with any guesswork and make decisions based on opportunities and potential revenue risks. “We

CIO Business Intelligence
JANUARY 16, 2023
There’s no doubt that DevOps has helped many IT organizations achieve their goal of delivering applications and services faster and better than traditional software development processes. It’s the CIOs responsibility to ensure that development teams aren’t intentionally or unintentionally straying off the DevOps path. “An
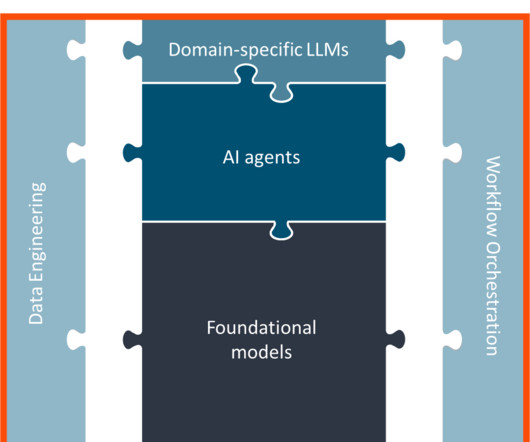
CIO Business Intelligence
DECEMBER 10, 2024
to GPT-o1, the list keeps growing, along with a legion of new tools and platforms used for developing and customizing these models for specific use cases. The rise of vertical AI To address that issue, many enterprise AI applications have started to incorporate vertical AI models. From Llama3.1 to Gemini to Claude3.5

Galido
JULY 17, 2018
Information Technology Blog - - What Are Top Reasons for Developers to Opt for Salesforce DX? Salesforce DX that is predominantly used by developers actually allows users total version control. We know that version control would be allowing developers to possess much more control over auditing, collaboration, and even disaster control.

Social, Agile and Transformation
FEBRUARY 6, 2013
I cover topics for Technologists from CIOs to Developers - agile development, agile portfolio management, leadership, business intelligence, big data, startups, social networking, SaaS, content management, media, enterprise 2.0 Are developers going to accept poorly defined stories and permit changes in scope during a sprint?

GeekWire
OCTOBER 9, 2021
This is not a hypothetical exercise: LEO Technologies, a company “built for cops by cops,” already offers automated surveillance of incarcerated persons’ phone calls with their loved ones as a service. And, finally, we urge everyone concerned to remain highly skeptical of “AI” applications.

CIO Business Intelligence
APRIL 16, 2024
For each of these efforts, teams would develop plans, get estimates, and ultimately obtain the budgetary approval needed to get started. If an application is critical to a business, it’s not something that can be treated as a one-and-done project. Teams don’t just deploy the application and move on.

Trends in the Living Networks
FEBRUARY 6, 2013
As I wrote in an article on Governance as opportunity , research by MIT’s Eric Brynjolfsson showed 5% higher productivity from organizations that do ‘data-driven decision making’ The key issue is the capabilities that organizations will need to get value from Big Data, and how to develop those capabilities. Adding metadata.

Kitaboo
DECEMBER 18, 2023
To create dynamic eLearning content for online learners, managing editors should implement innovative curriculum development strategies. In this blog post, we will discuss a few principles of curriculum development strategies in eLearning to help you globally design effective and engaging K12 educational content for learners.

CIO Business Intelligence
SEPTEMBER 17, 2024
On the one hand, enterprise architects play a key role in selecting platforms, developing technical capabilities, and driving standards. They also have a well-defined means for collaborating with agile development teams and can work with them to deliver a roadmap of improvements tied to technical debt remediations.

Trends in the Living Networks
JANUARY 4, 2024
Therea are situations where scenario planning is more and less applicable. It can be done as a structured process or used in strategic exercises or executive development programs to encourage effective scenario thinking in executives.

GeekWire
MAY 22, 2020
As research institutions and companies throughout Washington place a priority on the response to COVID-19, WRF has received a number of grant applications that run the full gamut of ideas and technologies related to the pandemic, including digital health apps, vaccines, diagnostics, and more.

SPF13
SEPTEMBER 22, 2013
This tutorial will introduce the features of MongoDB by building a simple location-based application using MongoDB. Deploying the sample application. Building your first MongoDB Application. spf13 Steve Francia AKA Chief Developer Advocate @ responsible for drivers, integrations, web & docs. TUTORIAL PREREQUISITES.

SPF13
SEPTEMBER 22, 2013
This tutorial will introduce the features of MongoDB by building a simple location-based application using MongoDB. Deploying the sample application. Building your first MongoDB Application. spf13 Steve Francia AKA Chief Developer Advocate @ responsible for drivers, integrations, web & docs. TUTORIAL PREREQUISITES.

CIO Business Intelligence
FEBRUARY 27, 2024
And AI poster child Sam Altman is lobbying for a $7 trillion investment in AI chip development. I begin the AI hysteria detox with a series of exercises trying to place the technology moment in which we find ourselves in historical context. I ask executives to recount their “most memorable experience with emerging technologies.”

GeekWire
MARCH 22, 2023
Students were almost evenly split between AR and VR, with three teams opting to develop for the Hololens 2, and four for the Oculus Quest 2. Development tools: Students developing in augmented reality used Microsoft’s MRTK toolkit on the Unity cross-platform game engine. Learn more about the AR/VR Capstone Course here.

Trends in the Living Networks
MARCH 18, 2022
If we don’t exercise our voice, the only things that get built are the things that are immediately profitable,” he says, reedy voice rising and falling as he fidgets his hands and sticks his toes between the cushions of a lumpy gray couch. And so he has reluctantly begun to take on a bigger public role in shaping its future. “If

CIO Business Intelligence
NOVEMBER 9, 2023
In any case, he says, only 13% of Kyndryl’s revenue flowed through those legacy SAP systems in IBM, with the rest going through custom mainframe applications. The choice to expand on Workday was to double down and make that the platform, collapsing all of those 60-plus different applications and leveraging that platform,” he says.

ForAllSecure
NOVEMBER 2, 2022
With the rise of a “shift left” approach to security, more and more of the burden of delivering secure applications has been put on the developer. Whether running vulnerability scans or kicking off dynamic testing during the CI/CD process, the new normal is to find and fix errors before applications ever reach production.

CIO Business Intelligence
AUGUST 8, 2024
The process would start with an overhaul of large on-premises or on-cloud applications and platforms, focused on migrating everything to the latest tech architecture. For the past 10-15 years, business transformation initiatives have been the sole mandate of the technology team. This is a massive change in conventional business practices.

CIO Business Intelligence
NOVEMBER 29, 2023
Once enterprises commit to running business-critical applications in the cloud, they rarely move to another provider. But if you do your planning exercise properly, you shouldn’t have to move your applications around,” he says. In this case you have to re-architect the application before you can migrate it.

GeekWire
OCTOBER 21, 2024
.” The TEC 4 project makes use of resources including Berkeley Lab’s Perlmutter supercomputer , Microsoft’s cloud-based Azure Quantum Elements platform and NWChem , a computational chemistry software package developed at PNNL. “We are building a family of codes,” Kowalski said.

CIO Business Intelligence
SEPTEMBER 14, 2023
This isn’t a trivial exercise. However, total or widely used anonymization may make the data less or even non-useful for some AI applications. And this doesn’t even consider tasks such as merging databases, developing up with APIs to support the integration of transactional data, or myriad other potential issues.

CIO Business Intelligence
DECEMBER 6, 2024
Develop an AI platform and write a gen AI playbook to allow it to move quickly without shortchanging on security and governance measures. Muthukrishnan and his team developed three simple guiding principles: Experiment with intern-facing use cases first, always have a human in the middle, and never expose any Ally data externally to LLMs.

SecureWorld News
JULY 31, 2023
Web applications have become an integral part of our daily lives, facilitating everything from online banking to social networking. However, as these applications handle sensitive user data, they have also become attractive targets for cybercriminals seeking unauthorized access or manipulation of personal information.

CIO Business Intelligence
MARCH 8, 2023
It’s about making sure there are regular test exercises that ensure that the data backup is going to be useful if worse comes to worst.” As part of this exercise, organizations need to prepare adequate response plans and enforce the requisite best practices to bring the business back online. Shore up a data protection strategy.
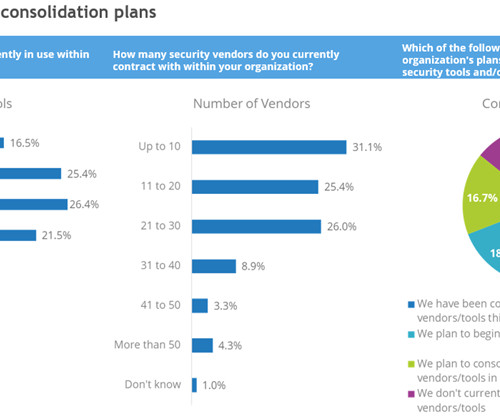
CIO Business Intelligence
AUGUST 29, 2024
SaaS application management tools, which identify all SaaS apps purchased and used by the organization. They can also identify redundant applications or licenses. This is where it pays to use the recommendations that resulted from the security tool rationalization exercise. Others hire an outside specialist.

CIO Business Intelligence
NOVEMBER 19, 2024
Microsoft is describing AI agents as the new applications for an AI-powered world. While that is true, your development teams may not be ready to implement yet. Development teams starting small and building up, learning, testing and figuring out the realities from the hype will be the ones to succeed.

The Verge
NOVEMBER 23, 2020
Apple cited the coronavirus pandemic, writing in a developer update posted to its website, “As the world fights COVID-19, we recognize that adapting experiences from in-person to digital continues to be a top priority.”. This deadline extension means developers have more time to temporarily reap the full profits of their sales.

CIO Business Intelligence
MARCH 16, 2023
Private 5G is the next evolution of networking for mission-critical applications used in factories, logistics centers and hospitals. It’s also a much simpler exercise to reconfigure connectivity between devices and improve the timing and synchronization of data feeds from sensors.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content