Introducing Maintenance for Agile Applications
Information Week
MAY 3, 2024
At what point does continuous, iterative development for Agile applications turn into a maintenance exercise?
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Information Week
MAY 3, 2024
At what point does continuous, iterative development for Agile applications turn into a maintenance exercise?

Forrester IT
JULY 12, 2021
Once you’ve got Kubernetes in production, those predictable business continuity and disaster recovery (DR) exercises get a lot more interesting — and not necessarily in a good way. As Kubernetes makes its way into stateful applications […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CTOvision
FEBRUARY 4, 2014
Application Software Security. href="[link] Control 6: Application Software Security. Penetration Tests and Red Team Exercises. href="[link] Control 20: Penetration Tests and Red Team Exercises. Patching Applications: Patching of applications must be continuously maintained. Malware Defenses.

CTOvision
AUGUST 15, 2014
Messaging solutions are applications within portals; as such, they are as secure as the portals, networks, policies and protocols that support them. These broad areas of security must be addressed to protect patient-provider communication via secure messaging applications. Secure Messaging Requires Authentication and Secure Networks.
CIO Business Intelligence
OCTOBER 5, 2023
Consider both the upsides and downsides to every disruptive innovation and develop applications that are smart, secure, and sustainable, without losing your focus on solving real-world challenges,” says Low Jin Phang, President, Digital Systems, ST Engineering. To find out more about ST Engineering Digital Systems, visit [link].

CTOvision
APRIL 11, 2016
Kerberos for centralized authentication management across applications. Microsoft Band Screen: On or Off During Exercise? Processors for optimizing log analytics from the edge enabling efficient, cost-effective expansion of log analytics systems with intelligent content-based routing and data retention. Find more information on HDF 1.2

Network World
FEBRUARY 26, 2019
There's a new Linux security tool you should be aware of — Cmd (pronounced "see em dee") dramatically modifies the kind of control that can be exercised over Linux users. Provided by a company of the same name, Cmd focuses on cloud usage.

All Things Distributed
OCTOBER 2, 2017
The cloud-hosted version would need to be: Scalable – The service would need to support hundreds of thousands, or even millions of AWS customers, each supporting their own internet-scale applications. Today, DynamoDB powers the next wave of high-performance, internet-scale applications that would overburden traditional relational databases.

Network World
AUGUST 13, 2024
You can’t say you’ve tested unless you’ve exercised all these paths. Misjudging cloud’s impact on application reliability But what does this all mean with regard to things like cloud usage? Enterprises said they are looking at their use of the cloud as a means of improving application reliability.

CIO Musings
AUGUST 16, 2013
A recent strategic planning exercise I attended focused on a discussion of the "Balanced Scorecard" concept. I also credit Mr. I also credit Mr. Richard Billingsley for compiling the information presented in the recent planning exercise. I have adapted it for use in the CIO / Customer relationship space.

CIO Business Intelligence
JUNE 21, 2024
INE Security , a leading global cybersecurity training and cybersecurity certification provider, predicts large language model (LLM) applications like chatbots and AI-drive virtual assistants will be at particular risk. “AI This can help stimulate creative thinking and practical application of learned skills.

CTOvision
MARCH 15, 2015
“Congress could not have imagined… nearly 4 million Americans would exercise their right to comment on proposed rulemaking.” The report describes the FCC''s application of "a ''light-touch'' approach for the use of Title II" for the Internet.

Network World
SEPTEMBER 23, 2024
Programmable synthetic sensors for end-to-end visibility Rounding out the updates, Selector AI has introduced a feature called programmable synthetic sensors, which allows customers to generate synthetic network traffic to exercise specific paths and ensure application performance.

Kitaboo
MARCH 30, 2023
This post aims to explore 12 such interesting applications of AI and AR in education. Enhances Student Engagement and Interest Another application of augmented reality in education is in the form of interactive, gamified AR learning that can have a significant positive impact on learners. Let’s begin.

CTOvision
MARCH 29, 2017
Failing to protect sensitive customer information, for example, can put a company in breach of applicable privacy laws. Ultimately, the company may decide to pursue legal action against the former employee, a costly and unwanted exercise for everyone involved. Further, data theft can place a company at risk of regulatory violation.

GeekWire
JULY 5, 2023
Pioneer Square Labs in downtown Seattle hosted about 30 employees from Fortive for a week-long exercise to test out ideas for generative artificial intelligence businesses. The exercise lets employees explore the potential of generative AI, helping find ways to use it in their daily workflows, she said.

CIO Business Intelligence
JULY 5, 2024
“We developed an algorithm to measure our different applications based on these 12 categories so we can eliminate technical debt via a more strategic and standardized approach,” she says, noting that the goal was to do away with any guesswork and make decisions based on opportunities and potential revenue risks.

The Verge
MAY 4, 2021
The whole thing is very cool, to the point of almost seeming like a wire-assisted fake, and likely as much an ad for the Royal Navy and Gravity Industries as it is an actual test of the Gravity Jet Suit’s utility in a naval exercise.

CIO Business Intelligence
JULY 26, 2023
These assets must either be: 1) “modernized” to platforms that enable secure integration across the enterprise-wide data and application fabric; or 2) cocooned and then connected to the rest of the “cloud-native” hybrid infrastructure with APIs and/or containerized microservices. It was interesting to see how low-tech these exercises can be.

Network World
SEPTEMBER 18, 2024
Improving overall security posture: The insights gained from red team exercises can be used to enhance security policies, procedures, and technologies. Exploiting technical vulnerabilities: Red teams search for and exploit technical vulnerabilities in systems, applications, and networks.

CTOvision
OCTOBER 21, 2015
The rules being crafted for this environment are applicable across multiple domains and can generate best practices worth applying elsewhere. And the SEC investigations and in some cases fines associated with RIA's are also being seen as widely applicable outside of the RIA domain. Cybersecurity isn’t a “one size fits all” exercise.

GeekWire
OCTOBER 9, 2021
This is not a hypothetical exercise: LEO Technologies, a company “built for cops by cops,” already offers automated surveillance of incarcerated persons’ phone calls with their loved ones as a service. And, finally, we urge everyone concerned to remain highly skeptical of “AI” applications.

CIO Business Intelligence
NOVEMBER 29, 2023
Once enterprises commit to running business-critical applications in the cloud, they rarely move to another provider. But if you do your planning exercise properly, you shouldn’t have to move your applications around,” he says. In this case you have to re-architect the application before you can migrate it.

CIO Business Intelligence
DECEMBER 20, 2023
Albeit emerging recently, the potential applications of GenAI for businesses are significant and wide-ranging. Generative AI can help businesses achieve faster development in two main areas: low/no-code application development and mainframe modernisation. percent of the working hours in the US economy.

CIO Business Intelligence
NOVEMBER 9, 2023
In any case, he says, only 13% of Kyndryl’s revenue flowed through those legacy SAP systems in IBM, with the rest going through custom mainframe applications. The choice to expand on Workday was to double down and make that the platform, collapsing all of those 60-plus different applications and leveraging that platform,” he says.

CIO Business Intelligence
APRIL 16, 2024
If an application is critical to a business, it’s not something that can be treated as a one-and-done project. Teams don’t just deploy the application and move on. They need to continue to not just support but improve the application, and these enhancements will be integral in fueling ongoing business success.

Network World
FEBRUARY 26, 2019
There's a new Linux security tool you should be aware of — Cmd (pronounced "see em dee") dramatically modifies the kind of control that can be exercised over Linux users. Provided by a company of the same name, Cmd focuses on cloud usage.

CTOvision
JUNE 4, 2015
DigitalGlobe is one of the community's most exiting and capable firms, providing space-based imagery and then related services, solutions and applications around that. DigitalGlobe has partnered with the US Geospatial Intelligence Foundation ( USGIF ) to exercise this crowdsourcing capability by sponsoring a hackathon.

Network World
JUNE 13, 2024
In the cyber world, this translates to performing lateral propagation to gain access to crown-jewel applications. Stage 4: This is when the thieves make their getaway with large sums of money, which is just like how cybercriminals steal large volumes of data from these crown-jewel applications that they can then use to commit extortion.

CIO Business Intelligence
FEBRUARY 27, 2024
I begin the AI hysteria detox with a series of exercises trying to place the technology moment in which we find ourselves in historical context. Our next exercise is asking the executives to select the movie, TV show, work of literature, or work of art that comes closest to capturing the “State of AI” today.

SecureWorld News
DECEMBER 30, 2024
This may involve identifying compromised servers, web applications, databases, or user accounts. ISO 22398: Covers the principles of planning, conducting, and developing training programs to prepare teams for critical situations through practical exercises and simulations. ISO 22318: Dedicated to ensuring supply chain continuity.

CIO Business Intelligence
AUGUST 8, 2024
The process would start with an overhaul of large on-premises or on-cloud applications and platforms, focused on migrating everything to the latest tech architecture. For the past 10-15 years, business transformation initiatives have been the sole mandate of the technology team. This is a massive change in conventional business practices.

SPF13
SEPTEMBER 22, 2013
This tutorial will introduce the features of MongoDB by building a simple location-based application using MongoDB. Deploying the sample application. Building your first MongoDB Application. Exercise 1: Model a business card. Exercise 2: Store a business card. TUTORIAL PREREQUISITES. Transcript. Business Card.

Computerworld Vertical IT
NOVEMBER 17, 2023
Sam Altman, a key figure in the creation of landmark generative AI application ChatGPT , has been fired by the OpenAI board of directors over an apparent lack of candor in his communications with the board. To read this article in full, please click here

GeekWire
MAY 22, 2020
As research institutions and companies throughout Washington place a priority on the response to COVID-19, WRF has received a number of grant applications that run the full gamut of ideas and technologies related to the pandemic, including digital health apps, vaccines, diagnostics, and more. Outdoor exercise. Help us out, we need it.)
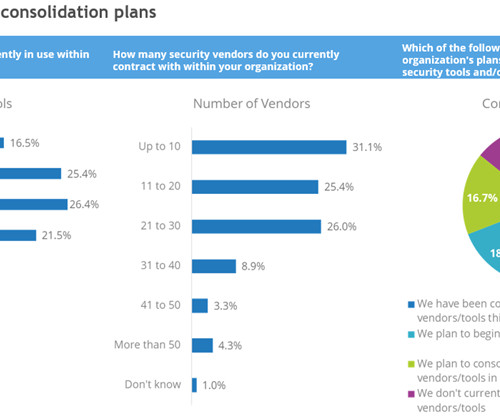
CIO Business Intelligence
AUGUST 29, 2024
SaaS application management tools, which identify all SaaS apps purchased and used by the organization. They can also identify redundant applications or licenses. This is where it pays to use the recommendations that resulted from the security tool rationalization exercise. Others hire an outside specialist.

Trends in the Living Networks
MAY 27, 2024
The primary application of my Humans + AI work over the last 18 months has been in strategic decision-making , working with boards and executive teams to augment their decision-making processes and outcomes using generative AI. The other major Humans + AI application I’ve been working on is in institutional investment decision-making.

CIO Business Intelligence
MARCH 16, 2023
Private 5G is the next evolution of networking for mission-critical applications used in factories, logistics centers and hospitals. It’s also a much simpler exercise to reconfigure connectivity between devices and improve the timing and synchronization of data feeds from sensors.

CIO Business Intelligence
SEPTEMBER 29, 2022
With organisations no longer having their applications in-house, being consumed as a service or apps running outside the traditional perimeter; many have simply looked at addressing the challenges by focusing on access and authorisation, but the need to inspect all traffic is paramount, says Palo Alto Networks’ Sean Duca.

The Accidental Successful CIO
JUNE 14, 2023
This way, if the applicant is rejected, the AI will present them with another list, showing where they didn’t meet the criteria or compared unfavorably to other applicants – basically the reasoning behind the decision. Which parts of the candidate’s application are processed by a machine and which are processed by a human?

CIO Business Intelligence
JANUARY 16, 2023
There’s no doubt that DevOps has helped many IT organizations achieve their goal of delivering applications and services faster and better than traditional software development processes. Ultimately, creativity is a muscle that must be exercised continuously to grow,” Kumar observes. DevOps should never be static.

Trends in the Living Networks
JANUARY 4, 2024
Therea are situations where scenario planning is more and less applicable. It can be done as a structured process or used in strategic exercises or executive development programs to encourage effective scenario thinking in executives.

Cloud Musings
APRIL 14, 2017
To avoid vendor lock-in, this service can also be exercised across multiple IT service providers. To do that you may also need to consider cloud brokerage capability. This tool can be used to plan, procure, govern and manage all IT services across all cloud models.

CIO Business Intelligence
SEPTEMBER 23, 2022
It’s about making sure there are regular test exercises that ensure that the data backup is going to be useful if worse comes to worst.”. As part of this exercise, organizations need to prepare adequate response plans and enforce the requisite best practices to bring the business back online. A Cyberresilience Road Map.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content