Eating Our Own Zero Trust Dog Food
Forrester IT
FEBRUARY 1, 2019
It is high time for Forrester to demonstrate Zero Trust in a practical application scenario, our upcoming virtual reference architecture project aims to do just that.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Forrester IT
FEBRUARY 1, 2019
It is high time for Forrester to demonstrate Zero Trust in a practical application scenario, our upcoming virtual reference architecture project aims to do just that.

CTOvision
DECEMBER 15, 2014
An autonomic computing system would control the functioning of computer applications and systems without input from the user, in the same way that the autonomic nervous system regulates body systems without conscious input from the individual. Application Streaming / Virtualization. Pervasive Computing.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Forrester IT
MAY 18, 2016
Reference design for headset and controller. Google also announced a reference design for both a headset and a controller (see photo). Applications and Google Play distribution. Additionally, Android N will include a number of VR-specific performance optimization features.

CTOvision
DECEMBER 17, 2013
By Prayson Pate Openness is one of the most-cited advantages of cloud-based applications, Software-Defined Networking (SDN) and Network Functions Virtualization (NFV). For example, a proprietary application like an email program might have application programming interfaces (APIs) that allow another application to send an email.

Fountainhead
JANUARY 19, 2012
Insights into Data Center Infrastructure, Virtualization, and Cloud Computing. In the context of data, applications and cloud computing, this question takes on a new perspective - and the role of Mohammed and the Mountain may soon reverse. But theres no denying that the application is becoming more mobile. Fountainhead.

Data Center Knowledge
JULY 17, 2013
Paul Speciale is Chief Marketing Officer at Appcara , which is a provider of a model-based cloud application platform. Numerous IT management tools are available today for use with the cloud, but the rubber meets the road at the level of the application because this is what a user will actually “use.” Cloud Application Management.

Network World
OCTOBER 3, 2024
AI networking AI networking refers to the application of artificial intelligence (AI) technologies to network management and optimization. Network slicing Network slicing can make efficient use of carriers’ wireless capacity to enable 5G virtual networks that exactly fit customer needs.

CIO Business Intelligence
AUGUST 27, 2024
This is an ever-growing catalog of reference applications built for common use cases that encode the best practices from NVIDIA’s experiences with early adopters,” he added. You can think of these applications as a database wrapped in a web UI connecting multiple teams through a business process,” he said. “We

CTOvision
MAY 26, 2014
We are already seeing the use of the Internet as a reference to law, but consider it being delivered in a tailored way to inform. By 2030 we should expect to have virtual adjudication in many cases. And consider having more online adjudication of both civil and criminal cases online. This is just one domain.

Network World
SEPTEMBER 4, 2024
Cisco, HPE, Dell and others are looking to use Nvidia’s new AI microservice application-development blueprints to help enterprises streamline the deployment of generative AI applications. More applications are expected in the future. Developers can gain a head start on creating their own applications using NIM Agent Blueprints.

Fountainhead
OCTOBER 17, 2012
Insights into Data Center Infrastructure, Virtualization, and Cloud Computing. Consider the use case to deliver huge numbers of applications and desktops across hundreds, thousands, or tens-of-thousands of mobile clients – Challenging for IT due to configuration, set-up, monitoring, management, network optimization and scaling.

Kitaboo
SEPTEMBER 25, 2023
Thanks to the advent of virtual classrooms, virtual classrooms, learners are now tapping into the world of digital resources, interactive content, and personalized learning experiences. Educational publishers are increasingly harnessing virtual classrooms to create and deliver content that goes beyond traditional textbooks.

Data Center Knowledge
JULY 26, 2013
What we’re seeing from vendors: We can expect upstart vendors to produce commercial versions of open reference architectures, and hopefully, more standardization from established vendors as SDN matures. This is especially true if the majority of those addresses are assigned to virtual machines.
Network World
JULY 9, 2024
The layers help network pros visualize what is going on within their networks and can help network managers narrow down problems (is it a physical issue or something with the application?), as well as computer programmers (when developing an application, which other layers does it need to work with?).

Fountainhead
OCTOBER 15, 2013
New Entrant VMware Will Raise Awareness If you look at Gartner Research''s 2013 Hype Cycle for IT Infrastructure and Outsourcing Services , you''ll find Hosted Virtual Desktops (HVDs) at the very peak of hype this year, outdistancing all other technologies. Think: Cloud-hosted desktops. But the environment is changing and growing.

Network World
OCTOBER 21, 2024
AI, security, energy-efficient computing , robotics, and virtual computing interactions are among the research firm’s top 10 strategic technology trends, which were unveiled at Gartner’s annual IT Symposium/XPO in Orlando. Agentic AI offers the promise of a virtual workforce that can offload and augment human work, Alvarez stated.

Network World
NOVEMBER 12, 2024
When I joined VMware, we only had a hypervisor – referring to a single software [instance] that can be used to run multiple virtual machines on a physical one – we didn’t have storage or networking.” We have gone from choosing an operating system to being able to run any application anywhere and on any cloud by virtualizing storage.”

Fountainhead
JANUARY 24, 2011
Insights into Data Center Infrastructure, Virtualization, and Cloud Computing. The technology behind this was a combination of orchestrating physical and virtual devices, which automatically composed appropriate infrastructure stacks to keep the service SLA within pre-defined bounds. Enter Virtualization. Fountainhead.

Network World
JULY 8, 2024
However, as application ports became well known owing to traffic migrating to application ports such as HTTP and HTTPS, simply allowing traffic on these ports was no longer an effective defense as its Layer 7 filtering was not granular enough. This was a significant improvement over just connecting everything.

CTOvision
JANUARY 26, 2016
Their products include high speed random from a quantum source, powerful key and policy management with embedded secure key store, as well as flexible encryption modules for a range of applications. However approaches are not fail safe; furthermore, once zeroized the data is permanently lost.

Network World
JUNE 5, 2024
Hypershield support for AMD Pensando DPUs and Intel IPUs Cisco added support for AMD Pensando DPUs to its new AI-based HyperShield , a self-upgrading security fabric that’s designed to protect distributed applications, devices and data. of Firewall Threat Defense (FTD), is available for all of Cisco’s physical and virtual firewalls.

Scott Lowe
MAY 6, 2013
I’ve had a few conversations about network virtualization and software-defined networking (SDN) recently (see here and here ) and the amorphous use of the term “software-defined.” Hey, where’s the network virtualization support? Similar Posts: On Network Virtualization and SDN. My apologies Matt!

Kitaboo
MARCH 30, 2023
Although the education sector is vastly defined by legacy systems, new-age AI tools, VR (virtual reality), and augmented reality in education can bring phenomenal change in terms of automation and closing the widening knowledge gaps that exist across traditional grade systems. Let’s begin.

The Verge
OCTOBER 4, 2021
Neal Stephenson famously coined the term “metaverse” in his 1992 novel Snow Crash , where it referred to a 3D virtual world inhabited by avatars of real people. But Stephenson’s book remains one of the most common reference points for metaverse enthusiasts, along with Ernest Cline’s 2011 novel Ready Player One. (The

CIO Business Intelligence
DECEMBER 20, 2024
As enterprise IT environments continue to grow in complexity, organizations are modernizing legacy applications and workloads, amongst other strategic IT initiatives, to address various IT and business challengesincluding cost optimization, simplification, time to market, technical debt, scale and more.

Fountainhead
APRIL 24, 2011
Insights into Data Center Infrastructure, Virtualization, and Cloud Computing. IT Organizations: Referring again to Chucks blog (and excellent illustrations therein) the IT organization will shift from siloed / distinct organizations to a set of unified service organizations leveraging a common services infrastructure. Virtual Geek.

CIO Business Intelligence
JANUARY 7, 2025
Scott Bickley, advisory practice lead at Info-Tech Research, said a press release outlining the pending launch of RISE with SAP on IBM Power Virtual Server, scheduled for the second quarter of 2025, touts 10,000 customers over 50 years running SAP on IBM. Still, modernizing is crucial for businesses with ERP systems to stay competitive.

Cloud Musings
DECEMBER 20, 2012
20, 2012 — NJVC ® , an information technology solutions provider headquartered in northern Virginia and supplier of Cloudcuity™ AppDeployer , and Virtual Global , a provider of cloud-enabled enterprise IT solutions based in northern. ” The term “killer app” generally refers to the technology that’s so.

CIO Business Intelligence
APRIL 25, 2024
The zero-copy pattern helps customers map the data from external platforms into the Salesforce metadata model, providing a virtual object definition for that object. “It Zero-copy integration means teams access data where it lives, through queries or by virtually accessing the file. You can do flows and automations on it.

Cloud Musings
NOVEMBER 20, 2016
In cloud computing, interoperability generally refers to the ability of service models from different cloud service providers to work together. He believes that applications can be built to be interoperable across different infrastructure platform. He believes interoperability does not necessarily start at the IaaS layer.

Fountainhead
MAY 18, 2012
Insights into Data Center Infrastructure, Virtualization, and Cloud Computing. Other more sophisticated IT finance tools then allocate those costs to projects and/or organizations across the enterprise, and some even integrate that data into other finance applications (See this Blog by Paulo Prazeres on the topic). Fountainhead.

Kitaboo
MAY 23, 2022
In the case of mobile learning, the course content is presented in a digital format using advanced media technologies such as video, Virtual Reality, Augmented Reality, Simulations, Animations, 3D infographics, and more. Simulation: Simulation in mobile learning refers to animating situations that resemble real-life settings.
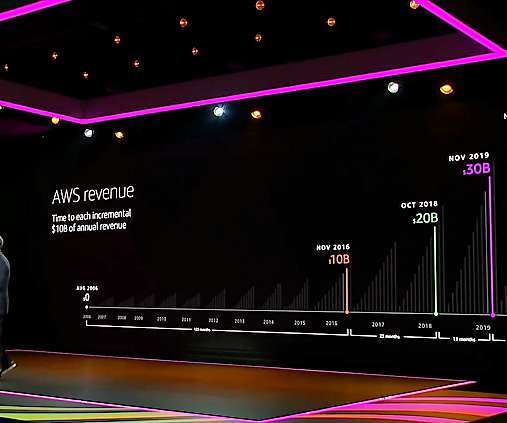
GeekWire
DECEMBER 3, 2020
Amazon Web Services CEO Andy Jassy with a chart showing AWS revenue growth at the company’s virtual re:Invent conference this week. But he sought to assure the virtual audience that AWS is not even close to its zenith, citing the 96% of the estimated $3.6 Screenshot via webcast).

CTOvision
JANUARY 25, 2016
As advanced applications are developed that leverage the capabilities that make Bitcoin possible, enterprise technologists will be able to tap into new capabilities for security and functionality. The design of this system operates without a central repository, making it a decentralized virtual currency.

Cloud Musings
OCTOBER 2, 2011
networks, servers, storage, applications and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.” ” NIST is implying the economies of scale that go with cloud computing when it refers to a pool of configurable computing resources. Lower Costs. Popular Pages.

Scott Lowe
MAY 3, 2013
I try to keep the information linked to data center technologies like networking, storage, virtualization, and the like, but occasionally other items slip through. Operating Systems/Applications. Virtualization. Looking for a good list of virtualization and cloud podcasts? I hope you find something useful. Networking.

Fountainhead
AUGUST 1, 2012
Insights into Data Center Infrastructure, Virtualization, and Cloud Computing. In other words, I dont just mean a product that offers an automated virtualization (server, storage, networking) layer. Virtualization. (31). Virtual Enthusiasm. Virtual Geek. skip to main | skip to sidebar. Fountainhead. Careful here.

Scott Lowe
FEBRUARY 4, 2013
Brad Hedlund (who will be my co-worker starting on 2/11) created a great explanation of network virtualization that clearly breaks down the components and explains their purpose and function. I also found references to running CFEngine on network apliances and running Chef on Arista switches. Operating Systems/Applications.
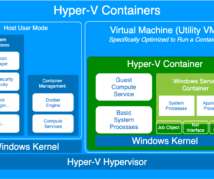
Linux Academy
MAY 15, 2020
To actually keep it to one windows container per Hyper-V VM, they had to make the VM as small as possible, referred to as a “Utility VM”. The contents of a Windows Server container are separated into two major parts: system processes and application processes. Nested Virtualization. It does NOT run Linux Containers.

CIO Business Intelligence
DECEMBER 4, 2024
We’ve all heard about how difficult the job market is on the applicant side, with candidates getting very little response from prospective employers. In fact, virtually everybody expects the pace to pick up. But the hiring side isn’t much easier. And there’s no end in sight. This has improved the morale and reduced burnout.

GeekWire
SEPTEMBER 16, 2024
Microsoft is aiming to address skepticism about the value of AI in its flagship productivity applications — and justify the premium price for business users — with a new wave of features for Microsoft 365 Copilot. Microsoft CEO Satya Nadella introduces the newest Microsoft 365 Copilot features in a video released Monday morning.

Network World
SEPTEMBER 25, 2024
DDI refers to the trio of core network services in IP networks: DNS, which turns domain names into IP addresses; DHCP, which assigns IP addresses to resources; and IPAM, which manages the network’s IP address infrastructure. “It NetOps teams lack visibility into cloud, which often results in wasted resources, Gupta said.

CIO Business Intelligence
JULY 14, 2022
Major trends around cloud technology, virtualization, and mobile you could see coming, but a novel distributed computing model based on public key cryptography? And that idea led to an unpredictable result: the possibility of decentralized, permissionless virtual machines. . Ethereum and the virtual machine.

CIO Business Intelligence
MAY 18, 2022
The list is growing and growing,” says Gordon Barnett, principal analyst at Forrester, “moving away from EA that just looks at applications and infrastructure to be truly enterprise. That may require, for example, an analysis of ERP systems to understand all the dependencies and functions that reference a bill of materials, he says.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content