Microsoft Pluton is a new processor with Xbox-like security for Windows PCs
The Verge
NOVEMBER 17, 2020
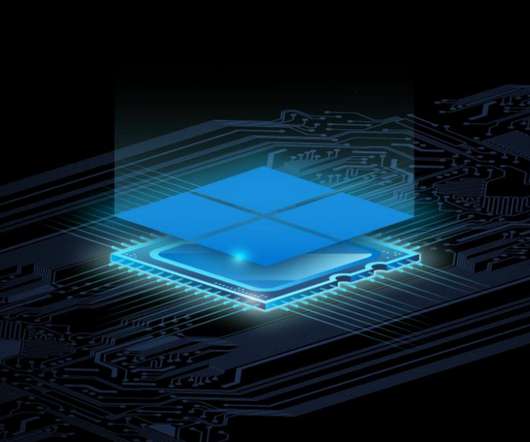
Microsoft Pluton is a security processor that is built directly into future CPUs and will replace the existing Trusted Platform Module (TPM), a chip that’s currently used to secure hardware and cryptographic keys. That means features like BitLocker encryption or Windows Hello authentication will transition over to using Pluton in the future.




















Let's personalize your content