How to set up passwordless SSH authentication for Ubuntu Server
Tech Republic Security
JULY 30, 2020
Learn how to enable passwordless SSH authentication on both Linux and macOS.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
JULY 30, 2020
Learn how to enable passwordless SSH authentication on both Linux and macOS.

Tech Republic Security
JANUARY 3, 2025
Here's how to use the secure copy command, in conjunction with ssh key authentication, for an even more secure means of copying files to your remote Linux servers.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
JULY 7, 2021
If two-factor authentication logins on your Linux servers are giving you fits, Jack Wallen has the solution for you.

Network World
MARCH 24, 2025
Over the years, World Backup Day has gained recognition, and, as someone who spent over 30 years as a Unix/Linux sysadmin and data security professional, I can say that very few if any IT departments wait for March 31 to review and evaluate their system and data reliability.

Network World
MAY 16, 2024
DMARC stands for “Domain-based Message Authentication, Reporting and Conformance.” It’s an email authentication protocol designed to give email domain owners the ability to protect their domain from unauthorized use. It controls what happens when a message fails authentication tests. Valimail data shows more than 1.3

Network World
JANUARY 21, 2025
Red Hat Connectivity Link integrates several critical capabilities that traditionally required separate solutions: Advanced traffic management and routing Policy enforcement mechanisms Role-based access control (RBAC) Authentication and security policies Rate limiting controls DNS configuration management TLS certificate handling Red Hat Connectivity (..)

Tech Republic
JUNE 21, 2022
Jack Wallen shows you how to install and use the Authenticator 2FA desktop client on Linux. The post Linux has a new authenticator app, and it’s easy enough for anyone to use appeared first on TechRepublic.

CTOvision
JULY 3, 2019
Over 30 VMware products are affected by SACK Panic and SACK Slowness, two recently disclosed Linux kernel vulnerabilities that can be exploited remotely without authentication for denial-of-service (DoS) attacks.

Network World
JANUARY 30, 2025
Agent communication platform: This layer provides the fundamental protocols and standards for how AI agents discover, authenticate, and interact with each other. But like Linux, Kubernetes, SONiC and other open-source technologies, the Internet of Agents will feature open-source community development, Pandey said.
TechSpot
AUGUST 7, 2023
For the past few months, the Linux version of the Mozilla VPN client has been affected by a dangerous security issue within the software's authentication process. The bug could easily be exploited to do very nasty things with the system and users' accounts, but Mozilla still has to provide a. Read Entire Article

Scott Lowe
MAY 2, 2013
I had a reader contact me with a question on using Kerberos and LDAP for authentication into Active Directory, based on Active Directory integration work I did many years ago. The issue was that he was experiencing a problem using native Kerberos authentication against Active Directory with SSH. Thanks Tomas!

Network World
SEPTEMBER 11, 2024
The process for disabling all account access should be automated, O’Connor says, and, whenever possible, two-factor and certificate-based authentication should be used to help ensure that login credentials alone can’t provide access when it should no longer be available.

Scott Lowe
AUGUST 5, 2024
For those that aren’t aware, Talos Linux is a purpose-built Linux distribution designed for running Kubernetes. Bootstrapping a Talos Linux cluster is normally done via the Talos API, but this requires direct network access to the Talos Linux nodes. Congratulations!

Dataconomy
JANUARY 26, 2025
Install Ollama via terminal (macOS/Linux): curl -fsSL [link] | sh ollama -v #check Ollama version 2. Image: Analytics Vidha Step-by-step installation guide for DeepSeek-R1 (local) To install DeepSeek-R1 locally using Ollama and Open Web UI, follow these steps: 1.

Linux Academy
APRIL 8, 2019
It also provides a handy browser plugin to fill in credentials for me, once I’ve authenticated to the plugin. Multi-factor authentication (MFA). Now, on to our second point for today: multi-factor authentication (MFA). Now, on to our second point for today: multi-factor authentication (MFA). Where to use MFA.

SPF13
MARCH 14, 2012
Installing on linux. To download and extract the files, on a typical Unix/Linux command line, use. host => localhost, // Connection name/alias. // Omit USER:PASS@ if Mongo isnt configured to use authentication. Installing MongoDB. These are the very brief instructions and make some assumptions. Installing on windows.

CIO Business Intelligence
JULY 19, 2023
Its commitment to Linux turned what might have been a Windows Server-based cloud computing backwater into the Microsoft Azure powerhouse, the only public cloud to give the AWS juggernaut a serious run for its money. Since Satya Nadella took the helm in 2014, Microsoft has doubled down on its support for non-Microsoft technologies.

Scott Lowe
MARCH 15, 2024
Ivan Pepelnjak dives deep on DHCP relaying on a Linux host. Rob McBryde shares his story of reviving a 2012 MacBook Pro with Linux. Security In early February a vulnerability was uncovered in a key component of the Linux boot process. Think Linux doesn’t have malware? Rory McCune explains Kubernetes authentication.
Linux Academy
APRIL 10, 2020
By now you’ve heard the stories that Microsoft loves Linux and fully embraces the open-source world. Windows Subsystem for Linux (WSL). Contact them via email: linux@microsoft.com. The only requirement is a Linux VM. Cloud sandboxes are included with your Linux Academy subscription. Visual Studio Code.

Scott Lowe
MAY 29, 2024
I recently had a need to get Barrier—an open source project aimed at enabling mouse/keyboard sharing across multiple computers, aka a “software KVM”—running between Arch Linux and Ubuntu 22.04. Below, I’ll share how I got Barrier working between an Arch Linux system and an Ubuntu system.

Scott Lowe
AUGUST 16, 2017
Since that time, I’ve been experimenting with ODrive, testing it to see how well it works, if at all, with my Fedora Linux environment. ODrive, if you’re reading this: put some effort into your Linux support and your docs, and you’ll probably get more paying customers.)
The Verge
NOVEMBER 17, 2020
That means features like BitLocker encryption or Windows Hello authentication will transition over to using Pluton in the future. You’ll still be able to build custom PCs with Pluton chips embedded inside, and there should even be support for Linux in the future, too. so you just get it.”

Dataconomy
MARCH 21, 2025
On March 14, 2025, a root certificate essential for verifying signed content and add-ons for Firefox and other Mozilla projects expired, necessitating an update to version 128 (or ESR 115.13+) to avoid disruptions across all platforms, including Linux, MacOS, Windows, Android, and iOS. Featured image credit: Growtika/Unsplash

The Verge
SEPTEMBER 9, 2020
But with the new YubiKey 5C NFC that’s being announced today, you no longer have to pick between being able to plug your key into a USB-C port or the convenience of NFC authentication, which lets you just tap your key on your device — you can now buy a key that offers both. Hardware-based keys offer extra layer of account security.

Scott Lowe
FEBRUARY 19, 2014
Let’s start with passing some JSON data to a REST API to authenticate. Example 1: Authenticating to OpenStack. Let’s say you’re working with an OpenStack-based cloud, and you need to authenticate to OpenStack using OpenStack Identity (“Keystone”). Example 2: Authenticating to VMware NSX.

CTOvision
JANUARY 31, 2017
Most of these devices are woefully insecure, never updated, and use default usernames and passwords or no authentication at all. Why waste time hacking one Linux server when you can walk through the door of a hundred connected web cameras? All of which would be fine if the Internet of Things was secure, but it isn’t.

Linux Academy
NOVEMBER 6, 2019
This November at Linux Academy, we have loads of new content coming your way! To all of our learners who may know someone who wants to learn more about the cloud or Linux, but they have been on the fence about signing up for a free community edition account, then tell them that right now is a great time for them to sign up!

GeekWire
MAY 17, 2023
Hinds is the project founder of Sigstore, a tool to verify and authenticate software artifacts. Hinds is also a founding board member of the Linux Foundation’s OpenSSF, a cross-industry effort to improve open-source software security, and was a distinguished engineer at Red Hat.

Linux Academy
MAY 31, 2019
For network devices, we should consider using RADIUS/TACACS+ for authentication purposes, not a shared user account. Red Hat offers OpenSCAP , can be used to scan Linux hosts for compliance but doesn’t scan Windows hosts. The post Using Secure Configurations | Standardize Your Security appeared first on Linux Academy Blog.

SecureWorld News
OCTOBER 12, 2021
Mozilla moves towards multi-factor authentication. In an article reported earlier by SecureWorld News, we covered Microsoft's new "passwordless" technology , which is actually multi-factor authentication (MFA). Now, we need to incorporate something called authentication that integrates with access on the other side.
Linux Academy
MARCH 2, 2020
These specific ports have been frequently used by unwanted and malicious users for abusive purposes, such as running crypto miners in clusters without authentication and authorization on the Kubernetes API. The post Beginner’s Basics of Kubernetes appeared first on Linux Academy. Control admin access to the nodes.

GeekWire
DECEMBER 30, 2023
But we also had Linux, which the open-source movement championed. So I hope that we will have a Linux of language models, a Linux of AI. … In addition, we do need watermarking, authentication, provenance, so we know where things come from. A great analogy here is what we’ve seen in operating systems.

Linux Academy
MAY 7, 2019
We Azure, just like Microsoft Linux! Linux Academy is the only way to get exam-like training for multiple Microsoft Azure certifications, check out this blog post if you’re wondering where to get started in Azure. Implement authentication. appeared first on Linux Academy Blog. Implement access control.

SecureWorld News
JULY 27, 2023
According to the new Uptycs whitepaper, Detecting the Silent Threat: 'Stealers are Organization Killers' (gated link), a variety of new info stealers have emerged this year, preying on Windows, Linux, and macOS systems. This demonstrates a focus on collecting data from multi-factor authentication tools.

SecureWorld News
OCTOBER 20, 2021
BlackMatter actors use a separate encryption binary for Linux-based machines and routinely encrypt ESXI virtual machines. Go a step further by regularly updating your passwords and enabling multi-factor authentication (MFA). BlackMatter then remotely encrypts the hosts and shared drives as they are found,” reads the statement.

Linux Academy
MAY 7, 2019
Linux Academy is the only way to get exam-like training for multiple Microsoft Azure certifications, check out this blog post if you’re wondering where to get started in Azure. As always, remember that you have a range of content available here at Linux Academy if you have any gaps in prerequisite knowledge.

Scott Lowe
OCTOBER 5, 2012
I came across this post on CloudFoundry’s User Account and Authentication Service (the UAA). Only a true geek would be interested in this, but here’s some information on running OpenBSD in KVM on Linux. Networking Security Storage Virtualization Automation KVM Linux OpenStack OSS OVS vCloud VMware'
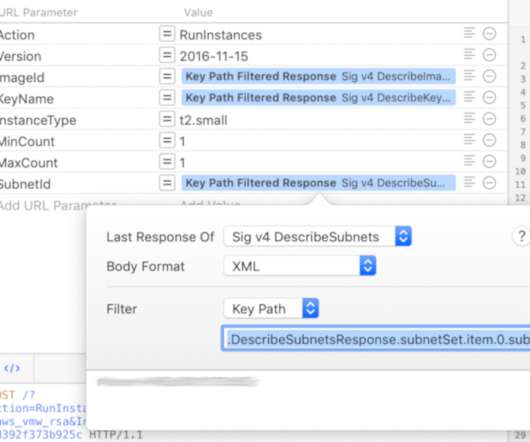
Scott Lowe
APRIL 12, 2020
Postman is a cross-platform application, so while my post was centered around Postman on Linux ( Ubuntu , specifically) the steps should be very similar—if not exactly the same—when using Postman on other platforms. This extension is necessary in order to have the API requests sent by Paw properly authenticated to AWS.

Scott Lowe
MARCH 20, 2020
This blending of “traditional” network engineering with containers, Linux, and DevOps tooling is how Matt is setting new trends and directions for the networking industry. Chris Wahl touches on the topic of using GitHub personal tokens to authenticate to HashiCorp Vault. Servers/Hardware. Nothing this time around.

Linux Academy
FEBRUARY 13, 2019
This user will be used to authenticate to the other cluster nodes and to perform actions on the cluster: sudo passwd hacluster. On node1 , authenticate as the hacluster user: sudo pcs cluster auth NODE1 NODE2. The post Configure a Failover Cluster with Pacemaker appeared first on Linux Academy Blog.

Linux Academy
JUNE 26, 2019
The Linux Audit system is a great solution. Finally, use the Pluggable Authentication Module (PAM) to set password requirements and lock out users with too many failed logins. Your security team can use the Linux Unified Key Setup (LUKS) to encrypt and decrypt physical disks to keep data secure when not in use. Disk Encryption.

Linux Academy
JUNE 10, 2019
Shortly after, the WiFi Alliance released WPA3, which includes many security improvements over WPA2, including: Protection against dictionary attacks via the Simultaneous Authentication of Equals (SAE), which replaces the WPA2 pre-shared key mechanism. or another enterprise-based wireless authentication setup.
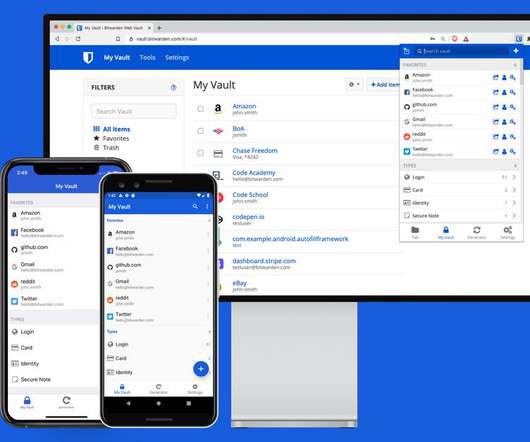
The Verge
MARCH 5, 2021
It’s available across iOS and Android; it has native desktop applications on Windows, macOS, and Linux; and it also integrates with every major browser including Chrome, Safari, Firefox, and Edge. You also have the option of protecting your Bitwarden account with two-factor authentication to provide an extra layer of security.

Galido
JUNE 2, 2016
Outstanding authentication through facial biometrics, including liveness detection. KeePass Password Safe is a free, Open Source, lightweight, and easy-to-use password manager for Windows, Linux, Mac OS X, and Android mobile devices. Get automatic alerts when websites get breached. 1U Password Manager. Secure password sharing.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content