Introducing The Forrester High Performance IT Capability Assessment
Forrester IT
JULY 28, 2024
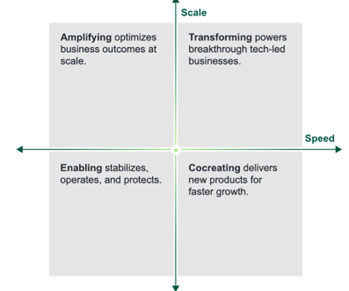
Forrester has introduced two major innovations this year for technology leaders and practitioners: High Performance IT, and the IT Reference Capability Map. Now, I am pleased to announce we have brought them together in a unique assessment tool, Forrester’s High-Performance IT Capability Assessment.




























Let's personalize your content