Open source in 2020: The future looks bright
Tech Republic Cloud
DECEMBER 18, 2019
Jack Wallen offers up predictions on open source, Linux, docker engines, automation, and more for the coming year.

Tech Republic Cloud
DECEMBER 18, 2019
Jack Wallen offers up predictions on open source, Linux, docker engines, automation, and more for the coming year.

Future of CIO
DECEMBER 16, 2019
IT is the core of the business today and must, therefore, be visible and present all the time. IT needs to be considered a line of business, not a cost center. CIOs need to show the value of IT with Return on Investment and tell the business management how well an IT investment repays the company. To improve IT maturity, IT value-based management needs to be driven by concepts like collaborative value or collective advantage and multi-layer ROIs.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CTOvision
DECEMBER 19, 2019
Read Jay Chapel list six cloud computing trends of 2019 on DevOps : Cloud computing was one of the hottest topics in technology and business media throughout 2019. This is no surprise as the cloud sector has been growing rapidly for the last few years. Synergy Research Group recently reported a 37% overall growth year-over-year […].

Network World
DECEMBER 16, 2019
The internet of things encompasses connected devices on a massive scale, actionable data and innovative business models – and it also brings unprecedented security headaches.

Advertiser: ZoomInfo
Sales and marketing leaders have reached a tipping point when it comes to using intent data — and they’re not looking back. More than half of all B2B marketers are already using intent data to increase sales, and Gartner predicts this figure will grow to 70 percent. The reason is clear: intent can provide you with massive amounts of data that reveal sales opportunities earlier than ever before.

Tech Republic Data Center
DECEMBER 16, 2019
Big data is the backbone of modern business, but before it can be used, it has to be properly managed. Here's an overview of the ins and outs of data management.
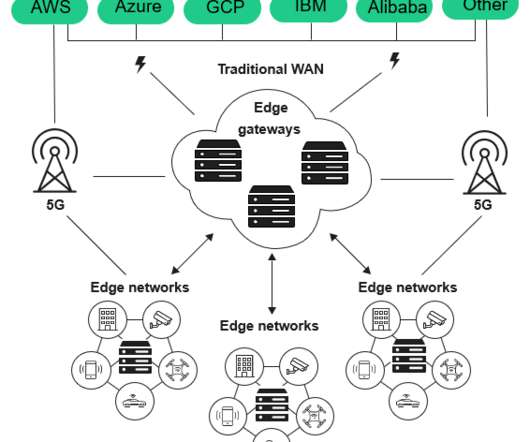
Forrester IT
DECEMBER 16, 2019
Traditional technologies are no longer addressing the growing needs of modern business, that’s why a massive quantity of tech and telecom vendors, and now a significant amount of enterprises & government agencies are all expanding their investments in Edge Computing for 2020. And why you should do the same. Verizon and Amazon Web Services announced a new partnership on December 3rd, 2019 – 5G […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.
Anoop
DECEMBER 16, 2019
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. In this post, we are going to discuss about a tool Microsoft Endpoint Configuration Manager “Task sequence debugger“ which helps with above challenges. I have presented this topic in “How To Manage Devices” event on 14th Dec. Related Post from Vishal – [link] Introduction Most of the Windows 10 admins who manage task sequence goes […].

Social, Agile and Transformation
DECEMBER 16, 2019
One of my 2019 new year resolutions was to read more books. I signed up for GoodReads and stated a reading challenge with a modest goal of finishing twelve books. I finished twenty-four, and many of these books are great reads for entrepreneurs, CIOs, and other digital transformation leaders. What makes a good book? My favorites have a strong focus, come from a unique perspective, are easy.

Forrester IT
DECEMBER 17, 2019
Business-to-business buying and selling is being disrupted the same way consumer models have fundamentally changed over the past decade due to digital transformation. New mobile apps, rich-media product experiences (think product spins or AR), and even kiosks are energizing direct-to-consumer models and causing waves up and down the value chain. Yet perhaps the biggest disruptor […].

CTOvision
DECEMBER 20, 2019
We have personally known the leadership of Verdant (Brian Dolan) for quite a while, so are totally biased, but rest assured that bias is based on years of interactions where whenever Brian says he will do something he does. Verdant is a startup studio that is focusing on speeding the time to market of enterprise […].

Advertiser: GEP
For years, you and your team have fought an uphill battle. Supply disruptions. Cost pressures. ESG compliance. You name it, and you’ve had to navigate it. In 2025, many challenges will persist, but procurement and supply chain teams have a powerful tool with rapidly advancing capabilities to tackle them — artificial intelligence (AI). The GEP Outlook 2025 report examines the disruptive transformation AI is driving in procurement and supply chains, alongside other key trends and the macroeconomic

Anoop
DECEMBER 18, 2019
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. In this post, you will get more details about Windows 10 Software Update Patching Options with Intune. How do you patch Windows 10 devices managed with Intune? Microsoft Software Update Patching process for Intune admins. Intune helps to configure Windows Update for Business (WUfB) policies to patch.

Information Week
DECEMBER 17, 2019
The new year promises big changes in Agile methodologies and applications. Here's a look at what to expect.

Forrester IT
DECEMBER 17, 2019
The Decade Cyber Went Mainstream Yes, technically, decades begin in years that end in one, but it’s easier to say the 2010s than the 2011s. Prior to 2010, cybersecurity was an insular domain. No one really cared, until something they were using didn’t work. Devices blew up due to malware or adware, and users got […].

CTOvision
DECEMBER 17, 2019
Read Ronald Schmelzer’s article in Forbes about the ways in which AI is making an impact on the back office: Artificial intelligence is making some of the most remarkable progress in back offices of enterprises of all types. The back office is where business operations that support the main customer-facing parts of the organization operate. […].

Speaker: Carolyn Clark and Miriam Connaughton
Forget predictions, let’s focus on priorities for the year and explore how to supercharge your employee experience. Join Miriam Connaughton and Carolyn Clark as they discuss key HR trends for 2025—and how to turn them into actionable strategies for your organization. In this dynamic webinar, our esteemed speakers will share expert insights and practical tips to help your employee experience adapt and thrive.

Tech Republic Data Center
DECEMBER 15, 2019
Jack Wallen shares his thoughts about data centers and edge computing, Kubernetes, 5G, containers security, and more for the coming year.

Tech Republic Security
DECEMBER 15, 2019
Jack Wallen runs through 10 of the most important cybersecurity threats, breaches, tools, and news of the year.

Forrester IT
DECEMBER 19, 2019
Every year in my personal life with my mother & sisters, we like to celebrate products, lessons learned and life hacks that we discovered throughout the year (yes, geek alert!). This year, I’m doing it with all of you in my professional life. What were some of your favourite (professional related) things in 2019? Feel […].

CTOvision
DECEMBER 16, 2019
OODA’s Future Proof conference will be held on March 19, 2020 at the Hyatt Regency Tysons Corner, Virginia. We want you to be there! Please mark your calendar now and register early. This event will be booked and sold out and we really hope that our our CTOvision readers to be there en mass so […].

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Anoop
DECEMBER 20, 2019
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Microsoft Endpoint Configuration Manager (MECM) 1910 is generally available now. Microsoft released the opt-in version of MECM 1910 in 30th Nov 2019. I have already explained and shown most of these new features in the video tutorial. Introduction I think SCCM 1910 production version will be available in all SCCM consoles if it satisfies the following […].

Tech Republic Security
DECEMBER 18, 2019
Jack Wallen shares cybersecurity predictions that might make your IT skin crawl. Find out what he thinks could be the silver lining to this security nightmare.

Forrester IT
DECEMBER 16, 2019
“Which CX improvement project should we do first?” Forrester’s CX research team gets that question a lot. The good news is that picking the right projects and doing them in the right order can be relatively easy – provided the customer experience team sets up their measurement program to populate a simple but effective prioritization […].

CTOvision
DECEMBER 19, 2019
Google’s seamless Chrome updates are one of its most appealing features thanks (unlike Windows 10) to their reliability. Until now. The latest version of Chrome has already automatically rolled out to hundreds of millions of users around the world is causing some serious problems for Android users. Picked up by 9to5Google and expanded upon by Android […].

Advertiser: ZoomInfo
In this exploration, we're diving into predictions about the future of sales. We're talking about a complete shake-up powered by automation and artificial intelligence (AI). These aren't just fancy tools — they're real game-changers. Automation and AI are here to redefine every interaction, making them smarter, faster, and more meaningful. From personalized customer journeys to streamlined sales processes, the goal is to make every moment count, enhancing both efficiency and connection.

Linux Academy
DECEMBER 19, 2019
From CEO, Sam Kroonenburg: Recently A Cloud Guru announced the acquisition of Linux Academy. I know this was a big surprise for everybody — our customers, and the staff of both companies! As part of the announcement we provided a high-level view of the vision for bringing the companies together, and naturally, that leads to a bunch of questions. Today, I want to give some more clarity & answer many of the customer questions we’ve seen out there.

Tech Republic Security
DECEMBER 20, 2019
Find out what Jack Wallen predicts for the cloud and cloud-adjacent technology in 2020 and why he encourages you to dream big.

Forrester IT
DECEMBER 18, 2019
What if I told you that less than half of design teams frequently work with analytics or data science employees during an iterative design process? It’s hard to be “dataful” without talking to people who have lots of data (to borrow a phrase from design author John Maeda). Earlier this year, I worked with my […].

CTOvision
DECEMBER 19, 2019
Read Tom Taulli list the breakthroughs that happened in artificial intelligence in 2019 on Forbes : When it comes to AI (Artificial Intelligence), VCs (venture capitalists) continue to be aggressive with their fundings. During the third quarter, 965 AI-related companies in the US raised a total of $13.5 billion. In fact, this year should see […].

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

Anoop
DECEMBER 17, 2019
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Humbled to have Great positive feedback for #HTMD (How To Manage Devices) Day conference 🥰 organised by Community for community😜 Thank you all for attending the conference. Highlights ?of HTMD 👉 120+ participants (from different parts of India – Chennai, Mumbai, Pune, Delhi, and Gujarat)?

Tech Republic Security
DECEMBER 19, 2019
Add terminal- and web-based Apache access.log view with GoAccess.

Forrester IT
DECEMBER 20, 2019
I hear this a lot lately: “My boss told me we need to get on marketplaces. What are the best practices?” After a few minutes unpacking the situation we get to the part about the day-in-the-life of the customer. That’s when I generally hear crickets. When marketplaces come up with vendors I hear […].

CTOvision
DECEMBER 19, 2019
Big data is one of the most diverse tools marketers can use when growing their business. Essentially, big data is the act of analyzing large quantities of data to make informed business decisions. Before machine programming allowed us to track everything from sales to user engagement, we had to put together the numbers one at a […].

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.
Let's personalize your content