9 Ways to Improve IT and Operational Efficiencies in 2020
Information Week
JANUARY 2, 2020
Facing economic uncertainty, many IT leaders are looking to become more efficient while also investing in the latest technology.

Information Week
JANUARY 2, 2020
Facing economic uncertainty, many IT leaders are looking to become more efficient while also investing in the latest technology.

CTOvision
JANUARY 2, 2020
Read Carlos Asuncion explain how you can prevent hackers from targeting your mobile payment apps on Dark Reading : Consumers love paying for goods and services with their smartphones. But as more retailers release their own mobile apps with in-store payment options, the threat of fraud must be carefully considered. Retailers offering in-store purchasing through […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
DECEMBER 31, 2019
Bias can result in undesirable AI outcomes. A recent DataRobot survey says organizations are most concerned about its impact on trust and their reputations.

Forrester IT
JANUARY 2, 2020
It’s that time of year. When folks make up their minds that things are going to change. The gym is full of new members who are eager to get into their journey towards some other semblance of better health, or a beach body, or some change that they desire. Others are in that annual state […].

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Social, Agile and Transformation
DECEMBER 30, 2019
Every once and a while, I draw inspiration from movies and actors/actresses. I have a post paying tribute to the great movie. What about Bob? Baby Steps - A Guide to Digital Transformation. I have another post comparing executive meetings with a classic Darth Vadar scene from The Empire Strike's Back. My two personal favorite movie posts are product management advice from the Tom Hanks movie.

CTOvision
JANUARY 1, 2020
The Dali Lama just posted some very wise thoughts for our consideration: Time never stands still, it’s always moving on. The past is beyond our control, but the future is still in our hands. To shape it we must use our intelligence and make an effort. We can change our circumstances. Becoming demoralized is of […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Forrester IT
JANUARY 3, 2020
The best New Year’s resolution? Become machine-learning-literate! It’s good for your organization, your career, and the sanity of your data scientists. See the new “Shatter The Seven Myths Of Machine Learning” report below for a mini course on machine-learning fundamentals and terminology.
Tech Republic Security
DECEMBER 30, 2019
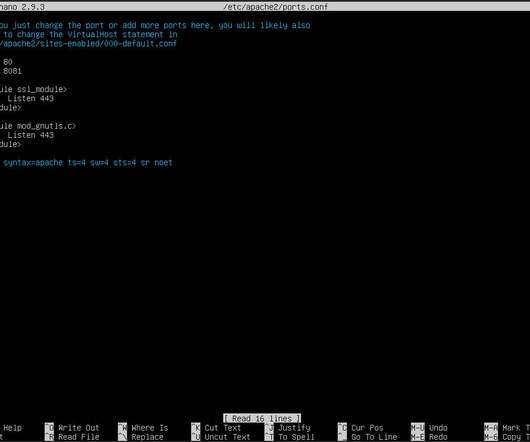
If you find port 80 is a security risk on your network, you can change the Apache listening port to something non-standard.

CTOvision
DECEMBER 30, 2019
The federal government’s leading tech media brand FedScoop has just published an insightful look inside Palantir’s support to some of the Army’s most critical mission needs. The report dives into a recent contract award that aims to bring together a wide range of disparate data from unique and often totally disjointed systems to provide decision-makers […].

Information Week
JANUARY 3, 2020
Here are five key techniques to support and encourage entrepreneurship in your employees -- while simultaneously keeping everyone moving in the right direction.

Advertiser: GEP
As early as next year, procurement and supply chain operations will begin to adopt AI agents, often called “agentic AI,” to work alongside employees to make and execute decisions with precision across procurement and even the most complex global supply chains. Unlike LLM-based generative AI tools such as ChatGPT, these AI agents do not require prompts from humans.

Forrester IT
DECEMBER 30, 2019
In October 2019, our team published its Predictions 2020: B2B Marketing And Sales, and in late December we recorded Webinar: B2B Marketing And Sales Predictions 2020: A Conversation With The Analysts Who Made Them. In the waning hours of 2019, Caroline Robertson and I took the opportunity to double-click into our sales enablement predictions. What […].

Anoop
JANUARY 3, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Great to start the year 2020 by announcing that this blog (www.anoopcnair.com) is part of Feedspot Top 20 SCCM blogs to follow in the year 2020. 😍😍😍👌👌 Subscribe to this blog NOTE! – Feedspot published this list of blogs in SCCM category even though Microsoft changed the name of SCCM to MEMCM.

CTOvision
DECEMBER 30, 2019
A critical flaw has been discovered in two Citrix products, placing 80,000 companies in 158 countries at risk. The easily exploitable vulnerability could allow attackers to obtain direct access to a company’s local network and to access a company’s credentials. It could also be used to launch denial of service and phishing attacks and to implant malware […].

Tech Republic Security
JANUARY 2, 2020
E-commerce sites are trying to keep up with sophisticated skimming schemes, but chances are your credit card information will still be compromised. A security expert offers advice.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

Forrester IT
DECEMBER 31, 2019
Is your firm ready for the roaring twenties? Nigel Fenwick predicts the winners in the next decade will be the businesses that master digital product management.

Anoop
DECEMBER 30, 2019
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. This is the 3rd article of the Bitlocker series. Links to previous parts are mentioned below. Give them a read if you have not yet! Part 1 – Bitlocker Unlocked with Joy – Behind the Scenes Windows 10 Part 2 – Device Encryption – Bitlocker made Effortless Today in this post, we will be talking […].

CTOvision
JANUARY 2, 2020
As 2019 winds down, every news media and technology site is pausing to reflect on the biggest trends of the past year. Some aspects of robotics and artificial intelligence are advancing rapidly; others, not so much. What should AI and robotics developers recall as they prepare for a new year? Sudhir Jha, senior vice president […].

Mick's IT Blog
DECEMBER 31, 2019
I wanted to install the Configuration Manager PowerShell module on my admin machine. After investigating a little, the module does not exist in the Microsoft PowerShell gallery. The PowerShell script below will create the module directory under the WindowsPowerShellmodule directory within %PROGRAMFILES%. It will then copy over all of the necessary files.

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.

Forrester IT
DECEMBER 30, 2019
My colleagues Danny Mu, Guannan Lu and I attended Alibaba ONE Business Conference on December 18 in Hangzhou. The conference attracted 2,000 business leaders from brands across industries and focused on how Alibaba enables brands’ business growth with its digital ecosystem, data and technology capabilities, and business methodologies. Alibaba wrapped these tools, methods, and capabilities […].

Tech Republic Data Center
DECEMBER 31, 2019
Your best competitive asset might just be the one you already own. Walmart is using edge computing to compete against Amazon with data centers. Could your company use its assets to try something new?

CTOvision
DECEMBER 30, 2019
Read Rob Csernyik’s article about how to invest in the Industrial Internet of Things on Barrons : Smart home products like Google Nest, Ring, and smart refrigerators have kept consumers ahead of the curve of the Internet of Things (IoT), which refers to the interconnection of everyday objects via the internet. As household and commercial […].
Tech Republic Cloud
JANUARY 2, 2020
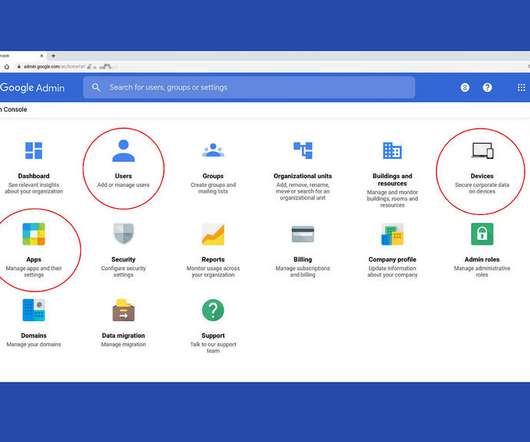
Review your organization's G Suite settings to ensure they reflect company user, device, and app needs.

Speaker: Miriam Connaughton and Donald Knight
As organizations scale, keeping employees connected, engaged, and productive can seem like a monumental task. But what if AI could help you do all of this and more? AI has the power to help, but the key is implementing it in a way that enhances, rather than replaces, human connection. Join us for an exploration into how industry trailblazers are using AI to transform employee experience at scale while addressing both the potential and the pitfalls.

Forrester IT
DECEMBER 30, 2019
I believe most people who own credit cards have experienced fraud or false positives (non-fraud transaction declined), so did I. Three months ago, I have experienced an overseas credit card fraud with amount around 3,000 USD and my bank is still investigating the case now. What gave me a deeper impression was the complicated procedures […].

Tech Republic Security
DECEMBER 29, 2019
If you find port 80 is a security risk on your network, you can change the Apache listening port to something non-standard.

CTOvision
DECEMBER 30, 2019
Despite the escalation of cybersecurity staffing and technology, enterprises continue to suffer data breaches and compromises at an alarming rate. How do these breaches occur? How are enterprises responding, and what is the impact of these compromises on the business? This report, one of three to come out of Dark Reading’s annual Strategic Security Survey, […].
Tech Republic Cloud
JANUARY 2, 2020
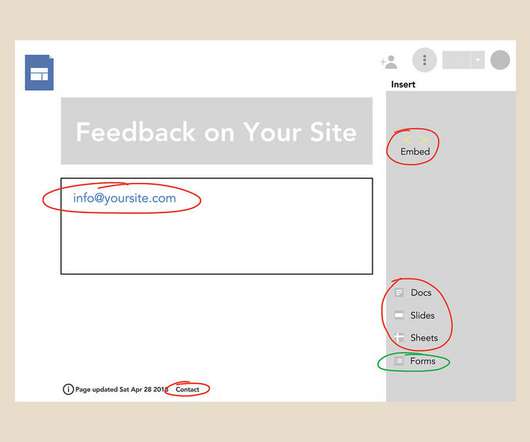
Learn five ways to assemble information via a Google Site in this tutorial.

Speaker: Christophe Louvion, Chief Product & Technology Officer of NRC Health and Tony Karrer, CTO at Aggregage
Christophe Louvion, Chief Product & Technology Officer of NRC Health, is here to take us through how he guided his company's recent experience of getting from concept to launch and sales of products within 90 days. In this exclusive webinar, Christophe will cover key aspects of his journey, including: LLM Development & Quick Wins 🤖 Understand how LLMs differ from traditional software, identifying opportunities for rapid development and deployment.

Forrester IT
DECEMBER 30, 2019
A week ago before Christmas, PayPal has officially finished its acquisition of a Chinese licensed payment company GoPay, a deal has started since the end of September. This deal signals PayPal’s official entry to China’s domestic payment market and made it the first foreign payment company to own the domestic payment license. I have followed […].

Information Week
JANUARY 2, 2020
Skills like communication, observation, empathy and logical thinking are key for developing the next-gen of leadership and equipping employees for the future.

Galido
JANUARY 2, 2020
Information Technology Blog - - 10 Tips for the Localization of Your Content in 2020 - Information Technology Blog. Modern business has the best chance of growing to a global level. Never before has it been so easy to connect people from all over the world with leading brands using online technologies, and never before has it been so easy to give them the experience they want – with the help of developed logistics and delivery systems.

Network World
JANUARY 3, 2020
Cisco this week issued software to address multiple critical authentication exposures in its Data Center Network Manager (DCNM) software for its Nexus data center switches. DCNM is a central management dashboard for data-center fabrics based on Cisco Nexus switches and handles a number of core duties such as automation, configuration control, flow policy management and real-time health details for fabric, devices, and network topology.

Advertisement
There’s no getting around it: selecting the right foundational data-layer components is crucial for long-term application success. That’s why we developed this white paper to give you insights into four key open-source technologies – Apache Cassandra®, Apache Kafka®, Apache Spark™, and OpenSearch® – and how to leverage them for lasting success. Discover everything you’ll want to know about scalable, data-layer technologies: Learn when to choose these technologies and when to avoid them Explore h
Let's personalize your content