Here's how a new machine learning software can beef up cloud-based databases
Tech Republic Data Center
JUNE 5, 2020
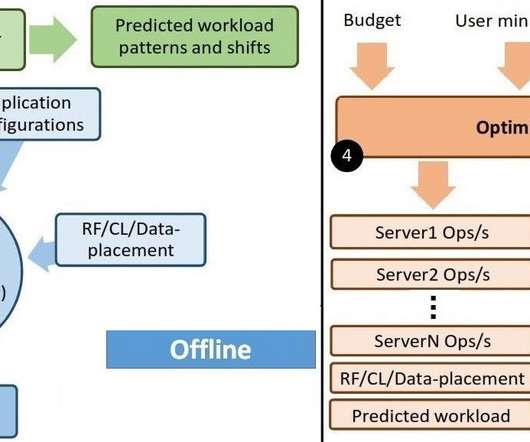
A Purdue data team just developed a way for organizations to improve performance and efficiency through cloud-hosted databases.
Tech Republic Data Center
JUNE 5, 2020
A Purdue data team just developed a way for organizations to improve performance and efficiency through cloud-hosted databases.

Forrester IT
JUNE 3, 2020
Virtual Care Blog Series – Part 2 The pandemic has pushed virtual care technologies to make the leap across the chasm of adoption as even the pragmatists and conservatives have started deploying these services. Forrester made the call that 2020 would be the tipping point in virtual care adoption and the pandemic accelerated this shift […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
JUNE 1, 2020
Artificial intelligence and ML can help us take DevOps to the next level through identifying problems more quickly and further automating our processes.

Tech Republic Security
JUNE 1, 2020
According to a Tessian survey, data protection concerns go out the window for remote employees.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Network World
JUNE 4, 2020
Cisco has unleashed an extensive new round of security warnings – three of them “critical” – mostly for users of its iOS XE software and industrial router family. In total, Cisco issued 23 Security Advisories that describe 25 exposures in its IOS and IOS XE systems. Network pros react to new Cisco certification curriculum. Beyond the three critical advisories, 20 have a “High” impact rating.

Forrester IT
JUNE 4, 2020
To our black employees, clients, friends, and the black community at large, we stand with you against the injustice and inequities brought down on you. It’s not right, it can’t persist, and we can do better. We see you, we hear you, and we stand with you.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Tech Republic Security
JUNE 3, 2020
Cybersecurity, remote IT troubleshooting and cloud support will be the most sought-after skills for businesses in the months following the COVID-19 pandemic, according to a survey of CIOs and tech executives.

CTOvision
JUNE 2, 2020
In January, Microsoft disclosed a data breach occurring through one of the tech giant’s internal customer support databases. Microsoft said anonymized user analytics, contained in roughly 250 million entries, were exposed. […].

Forrester IT
JUNE 1, 2020
The communications industry is facing a perfect storm of converging forces, from COVID-19 to the rise of influencer marketing and even AI. At Forrester, we research around 10,000 global technology vendors that utilize indirect sales and often get asked about the value of PR in the channel. A trend that is affecting many channel leaders […].

Information Week
JUNE 1, 2020
Data scientists, machine learning specialists and other data and analytics pros are seeing a changes to the job market in the wake of the COVID-19 crisis. What will the lasting impacts be?

Advertisement
Harness the True Power of your Contact Center In today’s fast-paced business environment, selecting the right contact center solution is critical for enhancing customer experience, improving operational efficiency, and optimizing costs. This comprehensive guide will walk you through the essential factors to consider when choosing a contact center software that aligns with your business needs.

Tech Republic Security
JUNE 3, 2020
A phishing email claims to send the recipient to a VPN configuration page for home access but instead leads them to a credential-stealing site, said Abnormal Security.

CTOvision
JUNE 2, 2020
There has been rapid growth in the Internet of Things (IoT) and big data technologies amongst organizations and individuals. According to Forbes, it’s predicted that the amount of data generated […].

Forrester IT
JUNE 4, 2020
In March 2020, as the implications of a global shutdown of physical offices became apparent, executives responsible for digital initiatives went into overdrive. If your firm is already digitally advanced, it’s likely to be faring far better than less advanced competitors by now. But no matter where your firm is today on it’s pandemic-induced digital […].

Information Week
JUNE 4, 2020
Almost overnight, companies pivoted to remote work, but long-term viability requires an all-in commitment to digital transformation across technology and culture.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Tech Republic Security
JUNE 4, 2020
Aimed at SMBs, educational facilities, and software companies, the ransomware leverages Java to encrypt server-based files, according to BlackBerry and KPMG.

CTOvision
JUNE 2, 2020
Read Gordon Feller take a look at the security aspects of the Internet of Things on Technology Networks : Just a few years ago, Samsung’s first push into providing smart […].

Forrester IT
JUNE 2, 2020
It’s been more than two months since corporate America’s unexpected leap into the deep end of the remote work pool. Behind the backdrops of our endless video calls, we’ve been juggling unexpected incursions from children, pets, and other household activities. Despite the occasional drama, we’ve been largely successful at adapting to this new paradigm, answering […].

Information Week
JUNE 5, 2020
A study on federal early technology adoption offers intriguing insights for all government and commercial IT leaders.

Advertisement
With IT budgets projected to grow 9.8% in 2025, leaders must invest wisely—not just cut blindly. This whitepaper introduces The Future-Proof IT Cost Optimization Model, a framework to reduce costs while maintaining service quality. Learn how Cloud Efficiency, AI-Powered Workforce Automation, Vendor Optimization, Cybersecurity Resilience, and Unified Communications can drive savings and improve efficiency.

Tech Republic Security
JUNE 3, 2020
Unauthorized access was the most common type of attack in 2019, and it was responsible for 40% of all data breaches, says ForgeRock.

CIO Business Intelligence
JUNE 2, 2020
Data visualization platform Tableau is one of the most widely used tools in the rapidly growing business intelligence (BI) space and individuals with skills in Tableau are in high demand. Market intelligence and advisory firm Mordor Intelligence forecasts the global data visualization market to achieve a compound annual growth rate of more than 9 percent between 2020 and 2025 as businesses seek to become more analytically driven.

Forrester IT
JUNE 1, 2020
Let’s just say that one measure of the hype that surrounds any emerging technology is the amount of new (and largely superfluous) jargon that it generates. Enterprise automation market needs pragmatic advice The market for Robotic Process Automation (RPA) has been in hypergrowth for a while now. RPA, and its extension into intelligent automation (IA), […].

Information Week
JUNE 5, 2020
The effort is relatively low compared to the immense personal and business benefits of keeping customers pleased and even delighted during this turbulent time.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Tech Republic Security
JUNE 4, 2020
Malicious files masquerading as curriculum vitae are being sent to businesses to install malware that can capture passwords and other sensitive information, says Check Point Research.

CTOvision
JUNE 3, 2020
Read Dr. Raul V. Rodriguez explain how artificial intelligence will impact the lives of ordinary people on DataQuest: Mechanization and automation of processes have brought about important social changes throughout […].

Forrester IT
JUNE 4, 2020
Virtual Care Blog Series — Part 3 Forrester made the call that 2020 would be the tipping point for virtual care adoption. The pandemic accelerated digital transformation for many healthcare organizations (HCOs) from a matter of years to a matter of months. Previous barriers to virtual care for consumers have been removed, such as lack […].

Information Week
JUNE 3, 2020
During this time of uncertainty, businesses are trying to adapt to the new normal. Here's why the Agile philosophy is suitable for unforeseen business obstacles.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Tech Republic Security
JUNE 2, 2020
A Lookout study found that organizations could lose millions through the growing number of unmitigated mobile phishing attacks.

CTOvision
JUNE 3, 2020
This news is going to fuel the Artificial Intelligence debate again as Microsoft fires 27 journalists for artificial intelligence. Microsoft is replacing its journalists with artificial intelligence to select, curate […].

Forrester IT
JUNE 5, 2020
As B2B analysts, we’ve been asking ourselves whether organizations have been responding to this health crisis in a way that is truly helpful to their customers. Our upcoming report, “Messaging In The Time Of COVID-19,” which details our findings after reviewing 60 B2B websites and social accounts across 12 industries, seeks to answer that question. […].

Information Week
JUNE 4, 2020
Responses show increased adoption of the methodology across more tiers of their organizations and closer ties between business and IT.
Advertiser: GEP
Procurement leaders are at a pivotal moment. With CPOs playing an increasingly strategic role, it’s time to leverage innovation and technology to drive resilience and efficiency. Download The 2025 Annual ProcureCon CPO Report to uncover key insights to thrive in a dynamic procurement landscape. What’s Inside: How CPOs are driving strategic decision-making and technology adoption The top priorities and challenges for procurement in 2025 Why AI, sustainability, and data analytics are essential for
Let's personalize your content