How to use the Whonix advanced security and privacy distribution
Tech Republic Security
JUNE 19, 2020
Find out how to use this unique take on the desktop operating system. Whonix is a Linux desktop dedicated to absolute security and privacy.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
JUNE 19, 2020
Find out how to use this unique take on the desktop operating system. Whonix is a Linux desktop dedicated to absolute security and privacy.

Tech Republic Security
DECEMBER 14, 2021
Qubes OS defines itself modestly as "a reasonably secure operating system." It might actually be one of the safest operating systems, often used by pros who are most concerned with computer security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
JULY 14, 2020
Find out how to use this unique take on the desktop operating system. Whonix is a Linux desktop dedicated to absolute security and privacy.

Network World
OCTOBER 15, 2024
How to assess the flexibility of a SASE solution Here are some key areas to understand and consider when assessing the flexibility of a SASE solution: SD-WAN : This one goes without saying, since SD-WAN is a key component of SASE. This will ensure you don’t run into any expensive or complicated snags down the road.

Advertisement
Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. In this eBook, explore how to tame the chaos, centralize automation efforts, and finally bring all those disparate tools together in harmony.

Network World
DECEMBER 16, 2024
Infrastructure: Learn how to install common peripheral devices to a laptop or a PC and how to secure a basic wireless network. Applications and software: Manage applications software, understand the components of operating systems, and explain the purpose of methods of application architecture.

Network World
NOVEMBER 21, 2024
Aviz Networks provides support and services to enable organizations to adopt the open source SONiC (Software for Open Networking in the Cloud) network operating system. Shukla said he wants Aviz to be a guiding force in the industry on how to really do AI for networking. “We
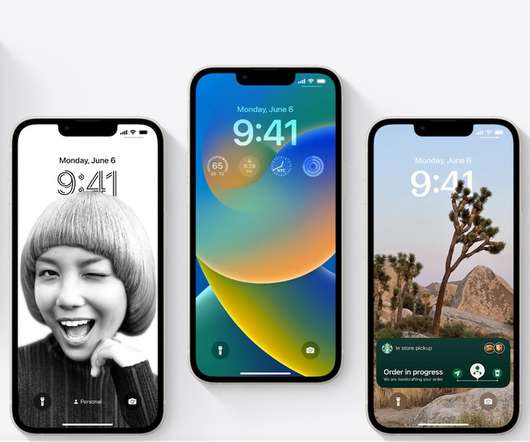
Tech Republic Security
JUNE 6, 2022
Learn about the new features available with iOS 16, and how to download and install the latest version of Apple’s mobile operating system. The post iOS 16 cheat sheet: Complete guide for 2022 appeared first on TechRepublic.

Network World
NOVEMBER 12, 2024
We have gone from choosing an operating system to being able to run any application anywhere and on any cloud by virtualizing storage.” I really work on the ground, directing my efforts to find out how to help clients evolve, get rid of their servers, improve processes, people and technology used.

SecureWorld News
JANUARY 13, 2025
Here's how to build yours. Compliance frameworks like NIST Cybersecurity Framework, ISO 27001, and SOC 2 help shape how businesses prioritize security. And don't overlook risk managementit's all about spotting potential threats and figuring out how to handle them before they become a problem. What is a talent stack?

CIO Business Intelligence
FEBRUARY 4, 2025
The question isnt just how to deploy AI in specific functions; its how to design a connected enterprise where AI enables a new way of workingone that is faster, more adaptive, and capable of driving strategic impact at every level. No matter your role, you can be multiple personas in any given scenario. Youre also an employee.

Anoop
MARCH 18, 2020
Let’s check how to create AppLocker Policies to Secure Windows Environments. Introduction Applocker is introduced with the Windows 7 operating system, Windows Server 2008 R2. The post How to Create AppLocker Policies to Secure Windows Environments Intune appeared first on SCCM|Intune|WVD|Azure| Windows by Jitesh Kumar.

CIO Business Intelligence
OCTOBER 24, 2024
But recent research by Ivanti reveals an important reason why many organizations fail to achieve those benefits: rank-and-file IT workers lack the funding and the operational know-how to get it done. They don’t prioritize DEX for others because the organization hasn’t prioritized improving DEX for the IT team.

Network World
APRIL 4, 2022
How to choose an edge gateway. FortiOS is the vendor’s operating system for the FortiGate family of hardware and virtual components. FortiOS 7.2, has 300 new features including AI support to help stop network threats more quickly, sandboxing to help fight ransomware threats, and improved SD-WAN , branch, and edge orchestration.

Network World
SEPTEMBER 26, 2019
Cisco this week warned its IOS and IOS XE customers of 13 vulnerabilities in the operating system software they should patch as soon as possible. How to determine if Wi-Fi 6 is right for you". Two of the vulnerabilities affect both Cisco IOS Software and Cisco IOS XE Software.

Network World
MARCH 5, 2025
Price: $145-$260 Exam duration: 120 minutes How to prepare: Typical candidates for this certification are IT professionals with at least one to three yearsof experience in storage technologies. Organization: NetApp Skills acquired: Management and administration of NetApp storage systems, specifically with the ONTAP operating system.

Network World
MARCH 12, 2025
A new AI cluster performance and load balancing feature is now part of Aristas flagship Extensible Operating System (EOS) that runs across its networking portfolio. UNO eliminates the guesswork about what is actually going on there, and AI can spot issues and offer suggestions about how to fix them before they become a problem.

CIO Business Intelligence
MARCH 4, 2025
They might not like living in the Land of Zoom (or Teams, or Meet), but not only do they interact there, theyre expected to figure out how to live and work there all on their own. Take stock of your tech stack Ask yourself scratch that, ask your teams: How many operating systems are in use? How many languages are in use?

Tech Republic Security
AUGUST 4, 2016
A step-by-step guide on how to download, install, and start using Tails, the world's most secure platform.

Tech Republic Data Center
JULY 16, 2021
If you've already spent the time learning SELinux, but have to deploy Ubuntu as a server operating system, you can install SELinux and be on familiar ground. Jack Wallen shows you how.

Tech Republic Data Center
MAY 19, 2021
SSH keys can be used in Linux or operating systems that support OpenSSH to facilitate access to other hosts without having to enter a password. Here's how to do it.
CIO Business Intelligence
JULY 17, 2023
Companies that have embraced the cloud need to understand the Shared Responsibility Model: a security and compliance framework that explains what shared infrastructure and systems the cloud provider is responsible for maintaining and how a customer is responsible for operating systems, data, and applications utilizing the cloud.

Anoop
FEBRUARY 11, 2020
Its Time to Upgrade your Operating System to Windows 10 1909 Upgrade. Let’s learn how to create an upgrade Windows 10 Task Sequence. To successfully deploy the latest operating system and choosing among those options, […]. Running Out of update….??

Computerworld Vertical IT
AUGUST 18, 2021
Whether you think Microsoft's operating system crosses the privacy line or just want to make sure you protect as much of your personal life as possible, we're here to help. Here's how to protect your privacy in just a few minutes. There has been some concern that Windows 10 gathers too much private information from users.

CTOvision
APRIL 20, 2014
In coming posts we will provide more tips, including how to install new “packages” to R to expand its functionality. Analysis Big Data CTO CRAN Linux Microsoft Windows Open Source Operating Systems R Unix Windows' Related articles. is released! (r-bloggers.com). r-bloggers.com). QuantLib 1.4

Network World
MAY 16, 2024
Bridge has matured to the point where customers can think of it as a digital operating system that can be personalized, if you will, for each business to integrate our services, manage their data, and gather insights or patterns they need to operate at a highly efficient way,” Shagoury said. “A

Tech Republic
OCTOBER 10, 2022
Jack Wallen shows you how you can easily set up automatic updates for the Rocky Linux operating system. The post How to enable automatic updates for Rocky Linux appeared first on TechRepublic.

Anoop
JUNE 16, 2020
Let’s see how to Customize Windows Out of Box Experience using SCCM. In this post, I will explain to you the scenarios where you will able to display language and region settings for user’s inputs in Windows Out of Box Experience (OOBE) after operating system deployment using the configuration manager.

Network World
JUNE 8, 2016
Since it doesn’t run a traditional operating system and takes advantage of various Google-powered security measures, Chrome OS is well-guarded against all the miscreants lurking out there on the Web. A Chromebook is already an ultra-secure computer straight out of the box.

Anoop
DECEMBER 4, 2020
The SMSTS.log is one of the important log files which will help you to troubleshoot installation issues related to Operating System Deployment (OSD) and fix those. The post SCCM OSD SMSTS Log File Reading Tips | ConfigMgr | MEMCM appeared first on How to Manage Devices by Jitesh Kumar.

Kitaboo
JUNE 25, 2020
Compatible with Multiple Operating Platforms: iOS, Windows and Android are some of the popular operating systems used by most users. If your content can be accessed on just one operating system, you lose out on the other readers. So, look for a software which will help you publish on multiple operating systems.

Network World
MARCH 9, 2017
Developers have embraced Docker containers on public clouds because they don’t need help from an IT operations team to spin them up. A software container is simply a thin package of an application and the libraries that support the application, making it easy to move a container from one operating system to another.

Anoop
NOVEMBER 19, 2020
Let’s try to understand how can we use conditions in the Task sequence to install operating systems via SCCM Task Sequence on a machine having dual drives. The post ConfigMgr Task Sequence OSD Multiple Physical Drives | SCCM appeared first on How to Manage Devices by Ankit Shukla.

TechSpot
OCTOBER 11, 2021
Microsoft has done an abysmal job of communicating the Windows 11 system requirements and the exact reasons behind them. Since unveiling the new operating system in June, it has only confused everyone by changing these details on the fly. Much of this confusion stems from the company’s insistence that PCs.

Network World
MARCH 29, 2017
How do they keep up with updated or new operating systems? But the diversity and innovation that excites many IoT fans is a big challenge not just for manufacturers and developers, but also (and most importantly) consumers. Which technology options should be used when designing or deploying IoT devices?

Tech Republic
JULY 14, 2024
It is a Linux kernel security model that provides a hardened set of access control security policies for the Linux operating system. SELinux stands for Security-Enhanced Linux. SELinux tends to get a bad rap, because it often seems to go out of its way to prevent legitimate applications from working. This guide, created by Jack.

Network World
OCTOBER 15, 2024
So, you may have an edge node with two NICs, VLANs , SR-IOV , and Edge Image Builder understands how to do that.” An organization could build out a single Kubernetes image for its edge deployments and shoot it out to 10,000 systems, for example.

CIO Business Intelligence
OCTOBER 26, 2023
While this is an essential role IT must play as a key driver of GenAI within an organization , there is another part that is no less important: ensuring users know how to use GenAI tools once they are built and readily available. Some have compared it to how the internet fundamentally changed the workplace.

Tech Republic
DECEMBER 26, 2022
Activating and establishing a stable remote network connection between Windows 11 computers requires preparation and a specific version of the operating system. The post How to activate Remote Desktop Connection in Windows 11 Pro appeared first on TechRepublic.

Computerworld Vertical IT
JANUARY 17, 2022
As a result, there have been lots of misperceptions about how Windows Update currently works, and how to best use it. Stop Windows updates entirely To read this article in full, please click here (Insider Story)
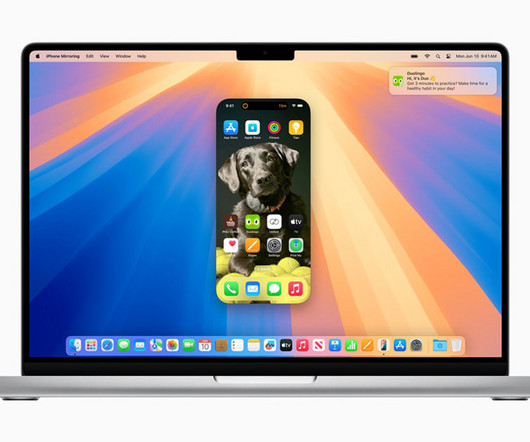
Tech Republic
JUNE 14, 2024
Learn about the new features available with macOS 15, as well as how to download and install the latest version of Apple’s flagship operating system.

SecureWorld News
OCTOBER 31, 2024
Here's a look at five terrifying threats that could be haunting your systems—and how to keep them from becoming a nightmare. How to keep the ghosts away : Conduct routine audits of connected devices, disconnect unused devices, and enforce strong password policies across all endpoints.

GeekWire
DECEMBER 18, 2024
A lot has changed since Windows debuted in 1985 as a graphical operating environment which runs on the Microsoft MS-DOS operating system. They noted that more than 500 software developers were planning to build applications for the fledgling operating system. I feel like we are close to that real breakthrough.

CTOvision
MAY 6, 2014
The vulnerability presents a particular threat to PC owners who still use Windows XP, as Microsoft stopped providing technical support for the old operating system in April. How to beat hackers exploiting the latest IE zero-day bug (networkworld.com). How to Beat Hackers Exploiting the Latest IE Zero-Day Bug (cio.com).
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content