Meta Disrupts 8 Spyware Firms, 3 Fake News Networks
Information Week
FEBRUARY 22, 2024
While furiously trying to put out one fire -- fake news -- the social media giant is dealing with another growing threat: spies for hire.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Network World
JUNE 19, 2017
The latest example comes from Mexico, showing how powerful spyware was used to target journalists investigating high-level official corruption and human rights defenders investigating government-sponsored human rights abuses. Why target a kid? To spy on his mother. To read this article in full or to leave a comment, please click here
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Network World
APRIL 3, 2017
Security researchers have uncovered the Android version of an iOS spyware known as Pegasus in a case that shows how targeted electronic surveillance can be. Fortunately, the spyware never hit the mainstream. It was installed less than three dozen times on victim devices, most of which were located in Israel, according to Google.

Network World
MAY 16, 2019
WhatsApp’s recent spyware hack took advantage of a security vulnerability and allowed attackers to access private, digital communication. In this episode of TECH(feed), Juliet walks through the hack, who was affected and how you can secure your devices ASAP.

Network World
OCTOBER 18, 2024
Meanwhile, OT and cyber-physical systems, once air-gapped and isolated from the internet, have rapidly become integrated into enterprise networks, where threats can proliferate. Top Mobile and IoT/OT trends Rise in financially-motivated mobile threats, including a 111% rise in spyware and 29% growth in banking malware.

Network World
APRIL 21, 2017
Has your computer been infected with a suspected NSA spying implant? A security researcher has come up with a free tool that can tell. Luke Jennings of security firm Countercept wrote a script in response to last week’s high-profile leak of cyberweapons that some researchers believe are from the U.S. National Security Agency.

CTOvision
APRIL 28, 2014
They do what it takes to get in, including devising very sophisticated phishing schemes, creating spyware, placing code in RAM, leaving hacker tools, installing rootkits and continually adjusting/re-placing spyware. 92% of attacks studied in this research can be described and categorized by nine basic attack patterns of: Crimeware.

Network World
AUGUST 25, 2016
Apple is issuing patches for three iOS zero-day vulnerabilities known as Trident that have been exploited for years by an Israel-based spyware vendor against a human rights activist, an investigative journalist and others.

Network World
AUGUST 25, 2016
The claims -- from research at Toronto-based Citizen Lab and mobile security firm Lookout -- focus on spyware that targeted Ahmed Mansoor, an activist in the United Arab Emirates. However, inside the message was a link that, once clicked, can infect an iPhone with spyware, using three zero-day exploits of iOS, the research found.

Network World
MAY 30, 2016
Meet Stealth Falcon, a sophisticated and likely state-sponsored cyberespionage group, which is hell bent on conducting targeted spyware attacks “against Emriati journalists, activists and dissidents.” The digital attacks started in 2012 and are still being carried out against United Arab Emirates (UAE) dissidents.

SecureWorld News
SEPTEMBER 17, 2024
The sanctions target key players developing and distributing the "Predator" spyware, which the Treasury describes as a "significant threat to the national security of the United States." a British Virgin Islands-based company, has been sanctioned for enabling transactions within the network. Additionally, Aliada Group Inc.,

SecureWorld News
OCTOBER 31, 2024
Lurking behind your network's doors are some real digital monsters waiting for an opportunity to sneak in! Zombie botnets: the network's walking dead Picture this: you're going about your day, unaware that one of your devices is secretly under the control of a remote attacker. Spooky fact : Sophos says the average ransom in 2024 is $2.73

Network World
MARCH 15, 2017
Put aside the matter of Russian interference in our presidential election to instead consider this scenario: If Vladimir Putin ordered his government-employed hackers to plant spyware on your personal computer – stealing all your data and even recording your Skype calls – you would have no access to any legal remedy in the U.S. court system.

Network World
MARCH 22, 2017
percent of Android devices had installed a " potentially harmful application ," such as spyware, a Trojan, or other malicious software. The chances of you encountering malware on your Android phone is incredibly small, according to Google. By the end of last year, less than 0.71 That figure was even lower, at 0.05

The Verge
JULY 23, 2021
Throughout the past week, we’ve seen story after story about a company called NSO Group, and a piece of spyware called Pegasus. Amnesty International ran detailed forensics on 67 smartphones to look for evidence that they were targeted by Pegasus spyware — and 37 of those phones tested positive. Illustration by Alex Castro / The Verge.
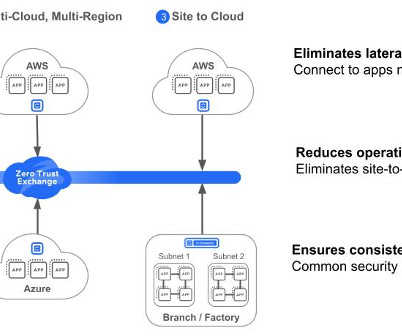
CIO Business Intelligence
NOVEMBER 8, 2023
Hence, it’s important to protect the cloud and its various connections across various cloud environments, not just those that directly tie back to the on-premise network. In many cases, organizations adopt legacy network security solutions and architectures to secure these cloud workloads that often fail to provide complete security coverage.

Gizmodo
FEBRUARY 1, 2022
A whistleblower alleges that the scandal-ridden spyware firm NSO Group once offered a telecom security company “bags of cash” to buy access to its cellular networks, ostensibly so its clients could track specific mobile users within the United States. Read more.

Network World
SEPTEMBER 1, 2016
If you thought your smartphone was safe(r) from the wild west of malware, spyware and other viruses compared with the PC space, think again. Taking the big hit are smartphone infections, which now account for 78% of all infections across the mobile network, says Nokia in its latest Nokia Threat Intelligence Report.

CTOvision
FEBRUARY 24, 2017
Network Security Management. Businesses may think they’re safer if they keep to their own network, but some of the greatest data breaches and corruptions have come from within. Detecting Cyber Intrusions.

SecureWorld News
JANUARY 9, 2025
Key cybersecurity provisions Securing communications networks Five billion dollars is allocated to help local telecommunications providers replace potentially insecure Chinese technology (e.g., Protecting military mobile devices Standards and policies will be implemented to secure Department of Defense mobile devices from foreign spyware.

Network World
MAY 19, 2017
Phishing emails from supposed family members, spyware piggybacking on legitimate apps, well-known sites hijacked with malicious code -- digital safety clearly needs new rules to meet today's evolving threatscape.

SecureWorld News
NOVEMBER 21, 2023
In a groundbreaking investigative report, the European Investigative Collaborations (EIC) media network, with technical assistance from Amnesty International's Security Lab, has exposed the shocking extent of the global surveillance crisis and the glaring inadequacies of EU regulation in curbing it. Chairman, Cedric Leighton Associates, LLC.

Network World
APRIL 12, 2017
A previously unknown Microsoft Office vulnerability was recently used to deliver spyware to Russian-speaking targets, in a possible case of cyberespionage. Security firm FireEye noticed the intrusion attempt, which taps a critical software flaw that hackers are using to craft malicious Microsoft Word documents.

Network World
MARCH 15, 2017
citizen from filing a civil suit against the African country, which allegedly infected his computer with spyware and monitored his communications. An appeals court has barred an Ethiopian-born U.S. Court of Appeals for the District of Columbia Circuit ruled Tuesday that foreign states are immune from suit in a U.S.

Network World
DECEMBER 6, 2016
Since October, millions of internet users have been exposed to malicious code served from the pixels in tainted banner ads meant to install Trojans and spyware, according to security firm ESET. The attack campaign, called Stegano, has been spreading from malicious ads in a “number of reputable news websites,” ESET said in a Tuesday blog post.

Network World
APRIL 6, 2017
It's particularly effective against ransomware, spyware, computer Trojans and other malicious programs that attempt to steal, encrypt or destroy files. Little Flocker can be used to enforce strict access controls to a Mac's files and directories as well as its webcam, microphone and other resources.

Network World
AUGUST 17, 2016
The maker of so-called spyware program WebWatcher can be sued for violating state and federal wiretap laws, a U.S. appeals court has ruled, in a case that may have broader implications for online monitoring software and software as a service.

SecureWorld News
NOVEMBER 30, 2023
Consequences of browser-focused cybercrime Hackers are able to utilize browser vulnerabilities to install malware and spyware on devices, steal login credentials for other services, extract sensitive user data, and maintain persistence inside systems. Employee training is essential to raise awareness about the dangers of outdated browsers.

SecureWorld News
JULY 10, 2023
The Google Play Store, a widely-trusted source for Android applications, has recently become a battleground for a concerning wave of spyware with ties to China. Pradeo, the mobile security company that discovered these malicious apps, has released a report discussing the spyware lurking on the Google Play Store. million users.

Gizmodo
SEPTEMBER 16, 2021
Earlier this week, the Department of Justice revealed that three former U.S. intelligence operatives were facing federal charges in connection with their work for BlackMatter, a foreign cybersecurity company based in the United Arab Emirates. Read more.

CTOvision
AUGUST 16, 2016
Here is how they are treated in Wikipedia: Dell sells personal computers (PCs), servers , data storage devices , network switches , software , computer peripherals , HDTVs , cameras, printers, MP3 players, and electronics built by other manufacturers. 5 Free Tools to Prevent Viruses and Spyware from Crippling Your PC (pcrichard.com).

Dataconomy
OCTOBER 18, 2023
Spyware like SpyNote can cause real damage to you ( Image Credit ) Banking to camera access SpyNote’s varied set of dangers is particularly concerning. SpyNote is well-known for its overlay injection attacks, which are used to steal user credentials when attempting to access banking, cryptocurrency, and social networking sites.

Computerworld Vertical IT
FEBRUARY 3, 2022
The news follows the revelation that the FBI also obtained NSO’s Pegasus spyware , but claims it did not use it. That also follows another recent claim that NSO Group offered “bags of cash” in exchange for access to US cellular networks via the SS7 network. To read this article in full, please click here

The Accidental Successful CIO
MARCH 21, 2012
Thank goodness your company has taken care to secure every way that there is for outsiders to get into your company’s network. Over the last 30 years or so, corporations have spent untold billions of dollars to create secure corporate networks. Oh, wait a minute. Maybe there’s one way that hasn’t been secured – you!

Dataconomy
MARCH 21, 2025
Malware has become an omnipresent threat in todays digital landscape, affecting devices, networks, and even entire organizations. Malware encompasses a wide range of malicious software aimed at causing harm to computer systems and networks. As technology evolves, so do the tactics employed by cybercriminals. What is malware?

Galido
JUNE 20, 2016
33% of the world’s computers have been affected by malicious software: viruses, trojans, trojan downloaders and droppers, unwanted software, adware, exploits, worms, phishing and monitoring tools, backdoors, spyware Countries most affected: China, South Korea, Taiwan, Turkey. Billion in Damages; network/email worm.

SecureWorld News
JANUARY 23, 2021
Paul Moore, an information security consultant, says that this worm is a serious threat to any PC or network. This malware strain works by installing spyware, used to gather information about browsing habits and personal data. Department for Education has recommended that schools check their networks as an extra precaution.

SecureWorld News
JULY 11, 2022
The Cybersecurity and Infrastructure Security Agency (CISA) issued a warning in April that the group was targeting cryptocurrency and blockchain companies and that it was using social engineering schemes to gain access to the victim's network. The threat actors then proceeded to take over four out of nine validator nodes on the network.

Cloud Musings
DECEMBER 14, 2014
By leveraging social media, face-to-face contact, telecommunications and other communication mechanisms, attackers are able to obtain information and access, either piecemeal or holistically, that permits their access to data, networks and other infrastructure.

Galido
NOVEMBER 21, 2018
Advanced System Protector protects your PC from adware, spyware, phishing scams and other malware threats effectively. Its network threat prevention stops malware or cyber-attacks even before they even begin. Use this free Windows malware protection tool to clean adware, remove spyware and other malicious content effectively.

SecureWorld News
DECEMBER 23, 2020
Pegasus spyware is a phone surveillance solution that enables customers to remotely exploit and monitor devices. Here is what researchers discovered from the analysis: "We obtained logs from an iPhone 11 device inside Al Jazeera networks while it was infected. Spyware attacks becoming harder to detect.

Galido
MARCH 4, 2019
Types of malware include spyware, viruses, worms, and Trojans as well as more recently a new way of stealing money called, Ransomware. By following these simple steps, you can ensure that your network is secure and safe from any potential threats. Secure your network. What is Malware? Why should you be aware?

SecureWorld News
AUGUST 8, 2022
Cybercriminals often use malware to gain access to a computer or mobile device to deploy viruses, worms, Trojans, ransomware, spyware, and rootkits. For the top malware strains, the advisory provides six mitigations: Update software, including operating systems, applications, and firmware, on IT network assets. Enforce MFA.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?




Let's personalize your content