Open source software: Ways for CISOs to quell the fear
CIO Business Intelligence
AUGUST 8, 2024
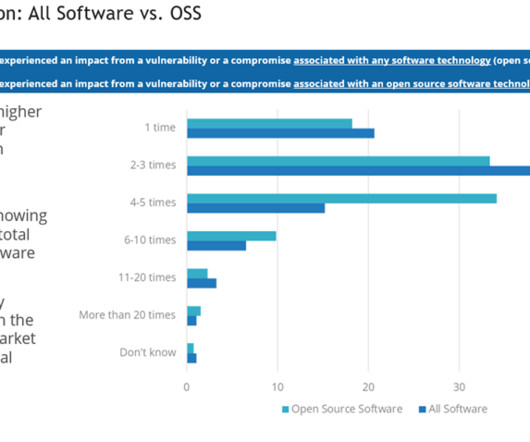
For many stakeholders, there is plenty to love about open source software. Developers tend to enjoy the ability to speed application development by borrowing open source code. CFOs like the fact that open source is often free or low in cost. The age-old question: How secure is open source software?




























Let's personalize your content