How to Retrieve and Generate Google 2FA Backup Codes
Tech Republic
AUGUST 17, 2023
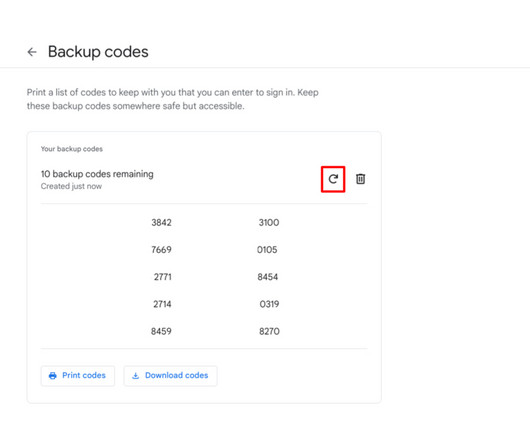
Learn how to retrieve and generate Google 2FA backup codes with this easy-to-follow, step-by-step tutorial.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
Tech Republic
AUGUST 17, 2023
Learn how to retrieve and generate Google 2FA backup codes with this easy-to-follow, step-by-step tutorial.

The Verge
SEPTEMBER 2, 2020
Two-factor authentication (2FA) is one of the best and easiest ways to keep your online accounts secure. They work by issuing an authentication code on your phone when somebody tries to access the account; if that person doesn’t have the code, they (or you) don’t get in. Different authentication apps handle this in different ways.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Generative AI Deep Dive: Advancing from Proof of Concept to Production
Reimagining Cybersecurity Training: Driving Real Impact on Security Culture
Don’t Get Left Behind: Leveraging Modern Product Management Across the Organization

Tech Republic
JUNE 17, 2022
In this step-by-step guide, learn how to enable the backup feature within the two-factor authentication application Authy. The post How to back up your Authy app appeared first on TechRepublic.

The Verge
JANUARY 7, 2021
But while those standards are still being adopted, the next best way to secure your accounts is two-factor authentication, or 2FA. This is how it works: when you log in to a service, you use your mobile phone to verify your identity by either clicking on a texted / emailed link or typing in a number sent by an authenticator app.

SecureWorld News
FEBRUARY 19, 2024
Fundamentally, across the site, strong password policies and multi-factor authentication (MFA) must be enabled. Backing this up with MFA—via a third-party authenticator app—will ensure all login attempts are valid and verified, which will help if multiple users are trying to access a WordPress back-end.

The Verge
OCTOBER 7, 2020
Tesla accounts can now be secured with two-factor authentication (2FA), giving owners an extra layer of security around their cars’ connected services, Electrek reports. A support page on Tesla’s website outlining how to set up the feature says any third-party authenticator apps can be used to provide the passcodes.

CIO Business Intelligence
FEBRUARY 1, 2024
In addition, what are the costs associated with incorporating the new software into the organization’s security infrastructure in areas such as access control, authentication, and zero trust. Backup: Application data doesn’t simply live in one place. Then there’s backups and disaster recovery.

Vox
NOVEMBER 12, 2023
Access to just about everything I wasn’t already logged into on my computer was dependent on access to my phone, with my mobile-device-only password manager and multifactor authentication apps and text messages. Didn’t I delete my backups to free up storage space? Backup of data in the digital reality we’re in now is paramount.

SecureWorld News
AUGUST 5, 2023
Multi-factor authentication (MFA) is a fundamental component of best practices for account security. Traditionally, this approach to authentication delivers a unique code to a user's email or phone, which is then inputted following the account password. SMS-based MFA MFA via SMS (i.e., However, MFA via SMS is not without its issues.

The Verge
JUNE 9, 2021
Two-factor authentication is a good way to add an extra layer of security to online accounts. Here’s how to set them up for your Google account, Facebook, and Twitter. They use a variety of authentication standards: FIDO2, U2F, smart card, OTP, and OpenPGP 3. Illustration by Maria Chimishkyan. They’re also not hard to install.
Vox
MAY 6, 2021
Authenticator apps like Google Authenticator might seem intimidating, but they’re easy to use and safer than texts. If you’re using texts for two-factor authentication, it’s time to change to an app. And you always use two-factor authentication, or 2FA. How to choose and use an authenticator app.

The Verge
FEBRUARY 23, 2021
What follows are instructions on how to download your LastPass data, and where to find instructions from several popular password managers that will help you upload that data to their services. Here’s how. Paid features start at $10 / year and include file storage, authenticator, two-step login, others. Free version? Zoho Vault.

SecureWorld News
AUGUST 22, 2022
Multi-factor authentication (MFA) is another strong and useful preventive tool that boosts your data safety. With the need for multiple devices to authenticate access, it makes it more difficult for hackers to gain entry into your social media accounts without being able to physically see the access code this authentication process requires.

Galido
NOVEMBER 7, 2018
Information Technology Blog - - How to Transfer Data from Android to Android in One Click - Information Technology Blog. Read on and learn how to transfer data from Android to Android without any hassle. Now, you can just connect both the Android devices to the system using authentic USB cables.

CIO Business Intelligence
SEPTEMBER 21, 2023
Educating end users on how to detect a phishing scam or social engineering tactics may be the most important element in mitigating most cybersecurity events. As learned from recent cyberattacks, user education has become a critical component to protecting against these threats as well.

SecureWorld News
MARCH 12, 2024
Let's explore the warning signs and discuss how to repair the damage. Signs of a security breach to observe While the CMS and its components might be prone to a variety of common technical issues over time, it is important to learn how to distinguish those from a security breach. But what happens if a hack has already occurred?

Dataconomy
FEBRUARY 7, 2024
For more insights : How to finance an acquisition? How virtual data rooms help Apart from the ability to explore alternative solutions on the platform and share insights with other parties, a data room offers various tools for discussions around innovative financing structures and partnerships without compromising confidentiality.

ForAllSecure
APRIL 26, 2023
How to Protect Against Social Engineering Attacks Organizations can protect themselves against social engineering attacks by educating employees about the risks, enabling multi-factor authentication, and implementing security policies that require verification of any requests for sensitive information or actions.

Galido
MAY 23, 2019
Information Technology Blog - - How to Protect Your WooCommerce Site from Hackers and Secure Your Customer Data? Automatic Backups. Without an SSL/TLS certificate: With an (EV) SSL/TLS certificate: Install Two-Factor Authentication (2FA). You can enable two-factor authentication on your WooCommerce store’s login page.

SecureWorld News
AUGUST 22, 2023
Multi-Factor Authentication (MFA): Implement MFA wherever possible, especially for systems and platforms containing PII. Regular Training and Awareness Programs: Regularly educate staff about the importance of data protection, safe online behaviors, and how to recognize potential security threats such as phishing.

GeekWire
FEBRUARY 25, 2022
RELATED: How to avoid propagating disinformation during the Russian invasion of Ukraine. The Cybersecurity and Infrastructure Security Agency has issued guidance to businesses and other organizations on how to avoid a digital breach. Make and verify backups. Use multi-factor authentication. ” A hack on U.S.

Dataconomy
MAY 21, 2024
Make sure that all data is encrypted both in transit and at rest, carry out regular employee training so that everyone understands the importance, and implement robust role-based access controls (RBAC) together with multi-factor authentication (MFA). It limits the risk of data leaks and minimizes access to private data.

CIO Business Intelligence
MARCH 15, 2023
Multifactor authentication fatigue and biometrics shortcomings Multifactor authentication (MFA) is a popular technique for strengthening the security around logins. And how do you tell? Getting ahead of the ransomware gangs Ransomware is big business for the criminal gangs who have figured out how to capitalize on it.

Linux Academy
MAY 31, 2019
For network devices, we should consider using RADIUS/TACACS+ for authentication purposes, not a shared user account. Ansible can help automate the backup, and you can learn more in this month’s how-to video that covers using Ansible to back up a Cisco ASA firewall. How do we do this kind of monitoring?

Dataconomy
NOVEMBER 21, 2023
We have over 1.5TB of documents leaked + 3 full backups of CRM for branches (eu, na and au),” boasts the ransomware group on their dark web data leak site. Additional details about the services that will be offered, and how to access them will be provided as soon as possible,” the announcement read on the official government page.

SecureWorld News
APRIL 9, 2024
Listen: "How to Really Make Sure that Cybersecurity Is Everyone's Job" [link] And, we need to get past this identity crisis: We're not just doctors; we're technologists who happen to know a lot about keeping people healthy. This isn’t just IT's problem to deal with.

Dataconomy
APRIL 25, 2023
Read on to find out: Why an MSP should care about cyber security Which threats you need to counter the most How to protect your and clients’ data and infrastructures from possible failures MSP Security: Why is it important? Here, every user and machine must authenticate before getting access to known resources and actions.

Vox
DECEMBER 8, 2022
How to encrypt most of your iCloud data — and why you should. Which means that almost everything you upload to Apple’s cloud — from backups to photos — can only be accessed by you. This update will add device and iMessage backups, iCloud Drive, Photos, and Notes to the list. A woman takes a photo of an iPhone.

Galido
AUGUST 30, 2019
Passwords & Authentication. Additionally, you can add another layer of protection with two-factor authentication. Backup Data. It is for this reason why you need to teach staff on how they can use their devices safely and protect important data. Antivirus Software. Specialists like sonicwallonline.co.uk

Galido
NOVEMBER 24, 2019
If you have important data on your system, then you should always have an up to date backup of all these contents on a flash drive or external hard drive. If you receive a threatening email, contact the merchant directly by typing in their link to confirm the authenticity of the email. Backing Up Data.

Sean Daniel
FEBRUARY 19, 2014
I can’t stress how important backing up is, I even have a special tag just for tips and tricks with backup, across various technology. learn how to set it up here ) You could get hacked, be that @Matt or @N style, or simply by a script kiddy (you’ve enabled 2-factor authentication for your account already right ?

SecureWorld News
OCTOBER 8, 2023
So, how to defend against targeted cyberattacks when employees' personal devices, even those not used for work, are under threat? Use the 3-2-1 backup rule. Additionally, be cautious when adding new friends; verify their authenticity through known offline connections. Below are some simple tips everyone can follow.

Linux Academy
APRIL 1, 2019
On the flip side of that, I’ve run into those who are so paranoid, they use multi-factor authentication for everything, and each password is ridiculously long and complex. If you missed the last few blogs in this series on how to secure your infrastructure, check them out below: Security Awareness Training. Vulnerability Scanning.

Linux Academy
APRIL 15, 2019
Welcome back to our weekly blog post as we look at how to better secure your infrastructure. Last week, we discussed the use of password managers and multi-factor authentication (MFA). The importance of local and cloud backups. Those tools were meant to help with the problem of password reuse and password weaknesses.

Sean Daniel
JANUARY 3, 2012
How to use your Home Server as an AirPrint server for only $10. Hi Dave, My guess is you've somehow managed to add some authentication to who can print. How To Install Windows Home Server 2011 on your MediaSmart or DataVault Hardware. Online Backup. (5). Online Backup. How to List your Small Business Server.

SecureWorld News
SEPTEMBER 15, 2023
How to secure your digital media assets effectively Given the sensitivities around digital media security, robust cyber defense strategies are required. Institute stringent password policies across all media management platforms , including mandated password complexity, frequent rotation, and multi-factor authentication (MFA).

Sean Daniel
FEBRUARY 1, 2011
How to set the Default Printer for All Users in your Small Business Server 2011 Standard or Essentials Network. Here is how to create the default policy: Click Start , Administrative Tools , and then Group Policy Management. Select Authenticated Users , and click Remove. This is a useful instruction on how to set the default.

CIO Business Intelligence
MAY 30, 2023
Recent and ongoing initiatives include designing and delivering a more robust backup system to boost resiliency and ensure that the organization could continue operations — whether hit by a tornado or a ransomware attack. But they’re all figuring out how to get access to the data in a way that helps them the most,” he says.

Linux Academy
MAY 7, 2019
Implement authentication. Course Description: Learn how to discover, assess, plan, and implement a migration of on-premises resources and infrastructure to Azure. Course Description: Learn how to manage and maintain the infrastructure for the core web apps and services developers build and deploy. Implement access control.

SecureWorld News
OCTOBER 29, 2020
Here is how to mitigate your risk: [link] — Cybersecurity and Infrastructure Security Agency (@CISAgov). Use multi-factor authentication where possible. There is an imminent and increased cybercrime threat to U.S. hospitals and healthcare providers. October 29, 2020. Ryuk attacks on hospitals: 'unprecedented'.

CIO Business Intelligence
MAY 18, 2022
EA can help, for example, by describing which cloud providers share the same network connections, or which shippers rely on the same ports to ensure that a “backup” provider won’t suffer the same outage as a primary provider, he says. Planning for supply chain disruption.

Linux Academy
MAY 7, 2019
Implement authentication. Course Description: Learn how to discover, assess, plan, and implement a migration of on-premises resources and infrastructure to Azure. Course Description: Learn how to manage and maintain the infrastructure for the core web apps and services developers build and deploy. Implement access control.

Galido
JULY 30, 2018
If you have important data on your system, then you should always have an up to date backup of all these contents on a flash drive or external hard drive. If you receive a threatening email, contact the merchant directly by typing in their link to confirm the authenticity of the email. Backing Up Data.

ForAllSecure
NOVEMBER 18, 2021
Vamosi: How do we know who’s on the other end of a connection, who it is that is logging into a computer or an account online? So we include other telemetry that seeks to authenticate that the entity logging in is who they say they are. So that’s why you need multi factor authentication. Think about it.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content