Slouching Towards Ubiquity: Five Notable Fintech Companies
Forrester IT
FEBRUARY 23, 2024
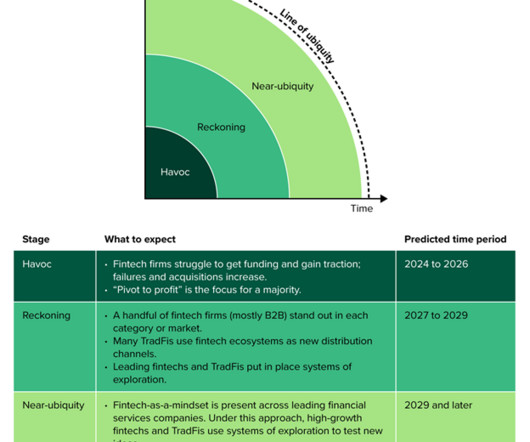
Fintech is slouching towards ubiquity (see image below). As it does, fintech will evolve into a broadly held mindset in contrast to being defined as a type of company, a specific set of startups, a category of product types, or a series of new business models.











































Let's personalize your content