5 Pillars of Sustainable Digital Transformation
Information Week
APRIL 1, 2022
C-suite execs need to move away from short-term thinking and instead consider the long-term impact and value of the decisions they are making.

Information Week
APRIL 1, 2022
C-suite execs need to move away from short-term thinking and instead consider the long-term impact and value of the decisions they are making.

Information Week
APRIL 14, 2022
The use of open-source software offers multiple benefits to organizations of all sizes, but open-source security is often undermanaged.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Anoop
APRIL 11, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Intune Vs SCCM and WSUS Vs WUfB Patching Method Differences appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Anoop C Nair.

Tech Republic Security
APRIL 1, 2022
A phishing technique called Browser in the Browser (BITB) has emerged, and it’s already aiming at government entities, including Ukraine. Find out how to protect against this new threat. The post “Browser in the Browser” attacks: A devastating new phishing technique arises appeared first on TechRepublic.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, CTO of Betterworks, will explore a practical framework to transform Generative AI prototypes into

Network World
APRIL 7, 2022
Picking just 10 Linux open source security tools isn’t easy, especially when network professionals and security experts have dozens if not several hundred tools available to them. There are different sets of tools for just about every task—network tunneling, sniffing, scanning, mapping. And for every environment— Wi-Fi networks , Web applications, database servers.
Tech Republic Cloud
APRIL 19, 2022
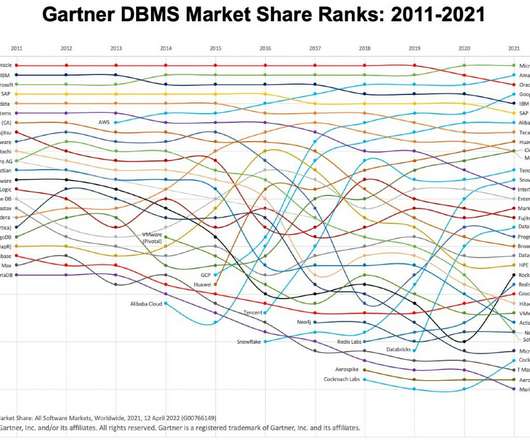
Databases are supposed to be the last thing an enterprise considers changing, but the cloud is upending all that, for several reasons. The post New Gartner report shows massive growth in the database market, fueled by cloud appeared first on TechRepublic.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Information Week
APRIL 6, 2022
Big tech and other companies are mandating employees return to the office, at least on a hybrid basis, after two years of pandemic-driven work-from-home. Will employees show up? Or will they quit?

Anoop
APRIL 29, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Install Microsoft Windows Defender Application Guard for Edge appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Jitesh Kumar.

Tech Republic Security
APRIL 1, 2022
A report from NCC Group profiles the industries plagued by ransomware as well as the most active hacking groups in February. The post Ransomware attacks are on the rise, who is being affected? appeared first on TechRepublic.

Network World
APRIL 4, 2022
Today’s announcement of IBM’s new z16 mainframes promises a system that caters to enterprise needs that include support for AI, security, hybrid cloud, and open source efforts well into the future. The new, more powerful and feature-rich Big Iron boasts an AI accelerator built onto its core Telum processor that can do 300 billion deep-learning inferences per day with one millisecond latency and includes what IBM calls a quantum-safe system to protect organizations from anticipated quantum-based

Speaker: Speakers:
They say a defense can be measured by its weakest link. In your cybersecurity posture, what––or who––is the weakest link? And how can you make them stronger? This webinar will equip you with the resources to search for quality training, implement it, and improve the cyber-behaviors of your workforce. By the end of the hour, you will feel empowered to improve the aspects of your security posture you control the least – the situational awareness and decision-making of your workforce.

The Verge
APRIL 21, 2022
CNN Plus, the news network’s dedicated streaming service, is shutting down before even turning a month old. Chris Licht, the new CEO of CNN, delivered the news to his new team at an all-hands meeting on Thursday, and the service will shut down entirely on April 30th. Licht congratulated the CNN Plus team in a memo to staff announcing the shutdown and said that the decision “is not a reflection of the quality of the talent and content at CNN+, some of which will migrate to CNN’s programming or so

CIO Business Intelligence
APRIL 25, 2022
An education in data science can help you land a job as a data analyst , data engineer , data architect , or data scientist. The data science path you ultimately choose will depend on your skillset and interests, but each career path will require some level of programming, data visualization, statistics, and machine learning knowledge and skills. Data engineers and data architects spend more time dealing with code, databases, and complex queries, whereas data analysts and data scientists typical

Information Week
APRIL 14, 2022
Although the adoption of this technology will be widespread, there is still time for workers to get ahead of the curve so that they do not become obsolete once the integration is complete.

Anoop
APRIL 4, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Create Custom XML File for Office 365 Intune Deployment appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Kannan CS.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

Tech Republic Security
APRIL 6, 2022
The Washington Post has revealed details of a contract with a software company that will allow the FBI to track social media posts. The post FBI investing millions in software to monitor social media platforms appeared first on TechRepublic.
Venture Beast
APRIL 5, 2022
The integration of BrainChip's Akida technology and SiFive's multi-core capable RISC-V processors is expected to provide an efficient solution for integrated edge AI computing. Read More.

The Verge
APRIL 14, 2022
Illustration by Kristen Radtke / The Verge; Getty Images. Tesla CEO Elon Musk is making his “best and final” offer to buy 100 percent of Twitter in an updated 13D filed Thursday with the SEC. He’s offering $54.20 per share in cash. Naturally, Musk had to sneak a “420” into the offer. Musk’s wealth hovers around $260 billion, according to Bloomberg. Twitter’s market valuation is about $37 billion.

CIO Business Intelligence
APRIL 11, 2022
More cities than ever before are investing in smart city technology and changing how cities operate. There are many benefits that come along with making a city “smart.” It gives the city more information and data to help drive decision making leading to tremendous benefits that positively influence the lives of everyone who lives, works, and visits, such as: .

Advertiser: GEP
Procurement and supply chain leaders are presented with their fair share of challenges, with a host of tools and strategies to resolve them. That said, what’s the best path forward to leverage this year’s trends? In this recap of a recent GEP-WBR webinar, 7 Leadership Themes for Procurement & Supply Chain Leaders in 2024, GEP’s Pramod Sethumadhavan explores seven vital leadership trends that will help guide procurement and supply chain decision-makers.

Information Week
APRIL 21, 2022
At its core, the value of a non-fungible token (NFT) today rests in how it is perceived by others. But an NFT's value over time remains to be seen.

Anoop
APRIL 20, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Manage Drivers Using PnPUnattend Command line Utility appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Jitesh Kumar.
Tech Republic Security
APRIL 13, 2022
The new vulnerabilities are being actively exploited, prompting CISA to advise federal agencies and organizations to patch them in a timely manner. The post CISA adds 8 known security vulnerabilities as priorities to patch appeared first on TechRepublic.

TechSpot
APRIL 20, 2022
Business Insider sources claim that Sony is working out ways to get ads into free-to-play PlayStation games. The goal would be to encourage the development of more free-to-play games by giving developers more possible revenue streams.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Gizmodo
APRIL 8, 2022
The first time that Patrick Comer tweeted about tabletop roleplaying games was in October 2021. He asked , “Who are hands down the best DND character illustrators out there?” He got one response. Read more.

CIO Business Intelligence
APRIL 12, 2022
Slowdowns caused by system disruption and complexities in your IT environment are more than an operational headache. They can have a direct impact on the bottom line. While it’s enormously important to make IT systems more efficient and give time back to the organization, it’s just as important to recognize the value of that time and understand the best ways to allocate it between workers, apps, and infrastructure.

Information Week
APRIL 1, 2022
Ensuring long-term data integrity has challenged researchers for decades. Here's a look at where data storage technology is heading next.
Anoop
APRIL 27, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post 3 Best Methods to Import SCCM PowerShell Module Cmdlets appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Dhanraj Barman.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Tech Republic Security
APRIL 8, 2022
A new malware has infiltrated AWS Lambda services, and investigators still aren’t sure how it happened. Here’s how it works and how to protect your organization. The post AWS Lambda sees its first malware attack with Denonia, and we don’t know how it got there appeared first on TechRepublic.
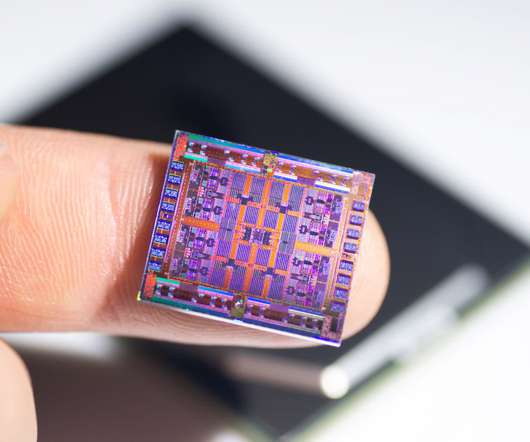
TechSpot
APRIL 17, 2022
Bruce Lee, an analyst for Goldman Sachs, put the first and second questions of the call to TSMC CEO C. C. Wei. His first question was about inflation and the economy at large, to which Wei responded that TSMC was well-positioned, as the leading global foundry, to weather fluctuations in.

Gizmodo
APRIL 11, 2022
New research continues to find evidence that psilocybin—the active ingredient in psychedelic mushrooms—can uniquely help people with depression. The study found that people undergoing psilocybin-assisted therapy experienced noticeable changes in brain patterns associated with depression, including when compared to a… Read more.

CIO Business Intelligence
APRIL 21, 2022
The world of marketing is awash in data. The solution? Embrace a customer data platform. Or at least some companies say. A customer data platform (CDP) is a software system that pulls together data from a wide array of sources — such as websites, ecommerce and ad platforms, social media applications, retail software, and more — to create a centralized customer database, as well as detailed profiles of each customer.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.
Let's personalize your content