Data Strategy: Synthetic Data and Other Tech for AI's Next Phase
Information Week
NOVEMBER 28, 2022
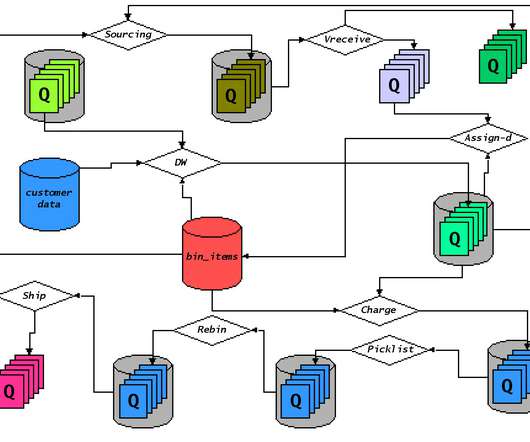
Forrester's Data Strategy & Insights event will offer insights to help you take your machine learning and artificial intelligence initiatives to the next phase.











































Let's personalize your content