IT Ethics: What It Means for Your Organization
Information Week
AUGUST 1, 2023
A growing number of IT departments have issued codes of ethics. Is it time for your IT organization to begin addressing and establishing its moral obligations?

Information Week
AUGUST 1, 2023
A growing number of IT departments have issued codes of ethics. Is it time for your IT organization to begin addressing and establishing its moral obligations?

IT Toolbox
AUGUST 2, 2023
Are your legacy IT systems impeding a simple lift-and-shift cloud migration? The post Cloud Migration with Legacy IT Systems: Overcoming Hurdles appeared first on Spiceworks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
AUGUST 1, 2023
Cybersecurity is a challenging field, but there is hope for a bright future, according to these leaders.

Forrester IT
JULY 31, 2023
In the recent Forrester Wave™ evaluation covering B2B intent data providers, we identified four primary business models among intent data providers. Understanding the differing focuses of these business models can help you build your shortlist of potential intent providers.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, CTO of Betterworks, will explore a practical framework to transform Generative AI prototypes into

Anoop
AUGUST 1, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Best way to Deploy Shell Scripts using Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Snehasis Pani.
IT Toolbox
AUGUST 3, 2023
How automated moving target defense can help tackle legacy security challenges. The post Bridging the Legacy Security Gap: 3 Challenges, 1 Solution appeared first on Spiceworks.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Forrester IT
AUGUST 1, 2023
Our newly published research, US Online Retail Forecast, 2023 To 2028, shows that both offline and online US sales will reach record levels this year. As we’ve said many times, the store is flourishing and far from “dead!

Anoop
AUGUST 4, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post New BitLocker Disk Encryption Policy for Intune Endpoint Security appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar.

IT Toolbox
AUGUST 3, 2023
Here’s how managers can improve team productivity and morale with the right meeting mindset. The post Meetings that Matter: Three Steps To Effective Meetings appeared first on Spiceworks.

Network World
AUGUST 1, 2023
Aiming to bolster its assessment of Internet traffic health Cisco said it would buy startup Border Gateway Protocol monitoring firm Code BGP for an undisclosed amount. Privately held Code BGP will slide into Cisco’s ThousandEyes network intelligence product portfolio and bring a cloud-based platform that among other features, maintains an inventory of IP address prefixes, peerings and outbound policies of an organization via configured sources, like BGP feeds.

Speaker: Speakers:
They say a defense can be measured by its weakest link. In your cybersecurity posture, what––or who––is the weakest link? And how can you make them stronger? This webinar will equip you with the resources to search for quality training, implement it, and improve the cyber-behaviors of your workforce. By the end of the hour, you will feel empowered to improve the aspects of your security posture you control the least – the situational awareness and decision-making of your workforce.

Forrester IT
AUGUST 1, 2023
A precarious economy has tempered business and technology leaders’ budget expectations. But now is not the time to retreat. Our 2024 Planning Guides advise on where to invest and experiment for success.

Anoop
AUGUST 2, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Free Entra Training Videos | Start Learning Entra ID appeared first on HTMD Community Blog #1 Modern Device Management Guides by Gopika S Nair.
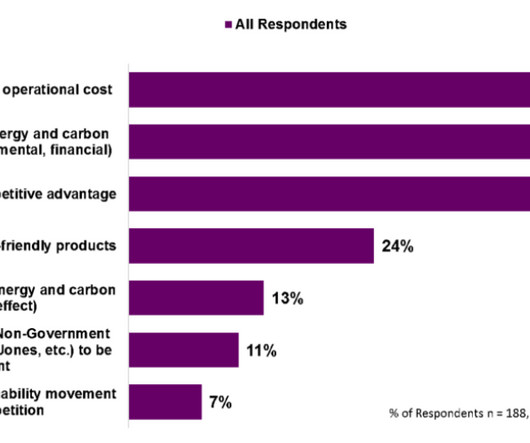
IT Toolbox
AUGUST 4, 2023
Hybrid cloud and IT-as-a-Service solutions are likely to be adopted by businesses that are pushing for sustainability in operations. The post 5 Keys to Attaining Sustainable IT appeared first on Spiceworks.

Network World
AUGUST 3, 2023
Fortinet has added new features to its SD-WAN software and a next-generation firewall series that promise to help customers better monitor and protect distributed enterprise resources. On the SD-WAN front, Fortinet is introducing two services – a network underlay and overlay option to let customers better manage WAN traffic to remote sites. The Underlay Performance Monitoring Service for SD-WAN utilizes the vendor’s core central management system FortiManager and FortiGuard’s database of hundre

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?
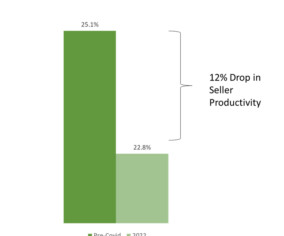
Forrester IT
JULY 31, 2023
This blog describes how conversation intelligence solutions can reverse the seller productivity decline and increase win rates.

Anoop
AUGUST 4, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post How to Install and Use Microsoft Power BI Desktop appeared first on HTMD Community Blog #1 Modern Device Management Guides by Krishna R.

IT Toolbox
AUGUST 3, 2023
Green computing offers lower costs, boosts innovation, attracts talent and strengthens the brand. The post Top 5 Advantages of Green Computing Practices for Companies appeared first on Spiceworks.

Tech Republic Security
JULY 30, 2023
The Data Encryption Policy’s purpose is to define for employees, computer users and IT department staff the encryption requirements to be used on all computer, device, desktop, laptop, server, network storage and storage area network disks, and drives that access or store organization information to prevent unauthorized access to organization communications, email, records, files, databases,

Advertiser: GEP
Procurement and supply chain leaders are presented with their fair share of challenges, with a host of tools and strategies to resolve them. That said, what’s the best path forward to leverage this year’s trends? In this recap of a recent GEP-WBR webinar, 7 Leadership Themes for Procurement & Supply Chain Leaders in 2024, GEP’s Pramod Sethumadhavan explores seven vital leadership trends that will help guide procurement and supply chain decision-makers.

Network World
AUGUST 1, 2023
Aiming to bolster its assessment of Internet traffic health, Cisco has acquired Code BGP, a privately held BGP monitoring startup, for an undisclosed amount. Code BGP will slide into Cisco’s ThousandEyes network intelligence product portfolio and bring a cloud-based platform that, among other features, maintains an inventory of IP address prefixes, peerings and outbound policies of an organization via configured sources, like BGP feeds.

Tech Republic Cloud
AUGUST 2, 2023
Gartner predicts a 16% growth in conversational AI thanks to the booming contact center tech market, the advent of virtual assistants and as-a-service models. But are employees ready to work with generative AI?

IT Toolbox
AUGUST 3, 2023
Reinvigorate your tech workforce with Lean tools & techniques. Boost productivity & stay competitive. The post How to Leverage Lean Tools To Reinvigorate the Workforce appeared first on Spiceworks.

Tech Republic Security
AUGUST 3, 2023
Agents of the FBI and Homeland Security at the Northeast Cybersecurity Summit revealed how cyberintelligence collaboration works. Learn more with our article.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Network World
AUGUST 1, 2023
Cisco has added ransomware detection and recovery support to its recently unveiled Extended Detection and Response (XDR) system. The new features target recovery from ransomware attacks and come courtesy of integration with Cohesity’s DataProtect and DataHawk offerings which offer configurable ransomware recovery and rescue support for systems assigned to a protection plan.

Information Week
AUGUST 3, 2023
Research shows that AI frequently churns out biased results. Will it ever be possible to create fully objective algorithms?
IT Toolbox
AUGUST 3, 2023
Discover how integrating CDP with CX can deliver tailored marketing experiences. The post CDP Integration & Personalization: A New Standard of Marketing appeared first on Spiceworks.

Tech Republic Security
AUGUST 3, 2023
In alliance with Cohesity and others, Cisco is fueling near-zero latency between ransomware detection and remediation with its Extended Detection and Response platform.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

TechSpot
JULY 31, 2023
Today, we're comparing the GeForce RTX 4060 with its more upscale sibling from a different silicon wafer, the RTX 4060 Ti, to determine if the Ti variant is worth the extra $100.

Information Week
AUGUST 4, 2023
The SEC released new rules overseeing public companies’ disclosure of cybersecurity incidents and risk management.
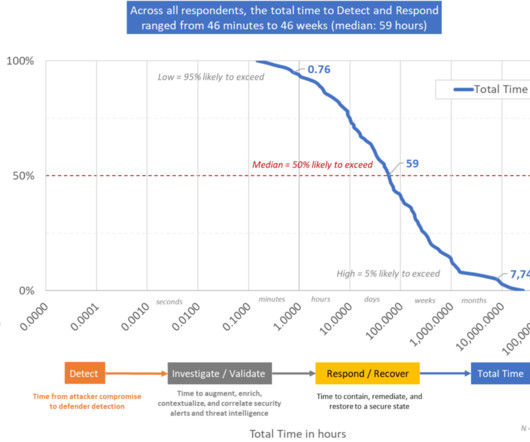
IT Toolbox
AUGUST 1, 2023
Key insights from an Aberdeen study on managed detection and response (MDR). The post Cybersecurity and AI/ML, Before the New Age of AI: Managed Detection and Response appeared first on Spiceworks.

Tech Republic Security
AUGUST 3, 2023
Discover the new models used to assign security budgets that succeed where traditional and outdated processes fail.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.
Let's personalize your content