Open-Source Tools for Pen Testing: Putting Your Technique to Work
Association of Information Technology Professional
SEPTEMBER 29, 2021
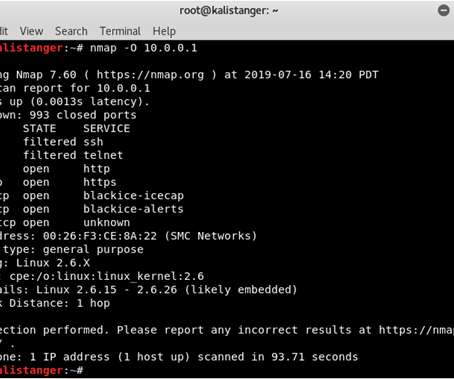
Tools and protocols go hand-in-hand. Take a look at what open-source tools work when you’re pen testing.
Association of Information Technology Professional
SEPTEMBER 29, 2021
Tools and protocols go hand-in-hand. Take a look at what open-source tools work when you’re pen testing.

Anoop
SEPTEMBER 30, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Learn How to Enable Microsoft Edge Sleeping Tabs using Intune appeared first on HTMD Blog #1 by Jitesh Kumar.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
SEPTEMBER 28, 2021
Many enterprises believe that their transformation is customer-centric, but Omdia research has found that customer-centric, customer-obsessed, customer-focused are obscure terms that, unless defined clearly, can derail the success of transformation agendas.

Tech Republic Security
SEPTEMBER 27, 2021
Commercially-available malware, with minimal modification, is behind attacks against the Indian government, says Cisco's Talos security research group.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, CTO of Betterworks, will explore a practical framework to transform Generative AI prototypes into

Tech Republic Data Center
SEPTEMBER 30, 2021
Microsoft has just released its most recent Windows Server platform. Check out the improved hybrid cloud features, beefed up security and improved support for large on-premises applications.

Anoop
OCTOBER 1, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Exclude OneDrive Shortcuts Sync using Intune appeared first on HTMD Blog #1 by Jitesh Kumar.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Tech Republic Security
OCTOBER 1, 2021
The study, from Cisco, comes with the announcement of its New Trust Standard, a benchmark for seeing how trustworthy businesses are as they embrace digital transformation.

Tech Republic Data Center
OCTOBER 1, 2021
Organizations can derive more value from their data if data scientists and IT data analysts work together. This includes sharing that data. Here are three ways to make it happen.

Anoop
SEPTEMBER 29, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Convert WQL Queries to SQL Queries using SCCM Trick appeared first on HTMD Blog #1 by Anoop C Nair.

Network World
OCTOBER 1, 2021
When National Cybersecurity Awareness Month (NCSAM) was launched in October 2004, it was a modest affair, offering anodyne advice to individual Americans and US businesses along the lines of making sure to update your antivirus software twice a year. Since then NCSAM has grown into an event-packed month with star-studded guest panels, annual launches in various cities (looking at you, Ypsilanti, Michigan!

Advertisement
While data platforms, artificial intelligence (AI), machine learning (ML), and programming platforms have evolved to leverage big data and streaming data, the front-end user experience has not kept up. Holding onto old BI technology while everything else moves forward is holding back organizations. Traditional Business Intelligence (BI) aren’t built for modern data platforms and don’t work on modern architectures.

Tech Republic Security
OCTOBER 1, 2021
The SOS program, run by the Linux Foundation, will reward developers with potentially more than $10,000 for enhancing the security of critical open source software.

Tech Republic Cloud
SEPTEMBER 29, 2021
If you're looking for yet another cloud storage provider, one that offers a Linux desktop app, Jack Wallen believes Megasync might be exactly what you need.

Anoop
SEPTEMBER 29, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post SCCM Task Sequence App Failure with Error 0x87d00267 after 2107 Update appeared first on HTMD Blog #1 by Anoop C Nair.

TechSpot
OCTOBER 1, 2021
The network security company said that in Q2 2021, 91.5% of malware arrived over an encrypted connection. It added that any company not examining encrypted HTTPS traffic at the perimeter will miss out on 9/10 of all malware. The data is derived from the firm’s own active WatchGuard Fireboxes.

Advertiser: GEP
Procurement and supply chain leaders are presented with their fair share of challenges, with a host of tools and strategies to resolve them. That said, what’s the best path forward to leverage this year’s trends? In this recap of a recent GEP-WBR webinar, 7 Leadership Themes for Procurement & Supply Chain Leaders in 2024, GEP’s Pramod Sethumadhavan explores seven vital leadership trends that will help guide procurement and supply chain decision-makers.

Tech Republic Security
SEPTEMBER 29, 2021
Not all organizations have a team or even staffers who can focus solely on vulnerability management, says Trustwave.

Tech Republic Cloud
SEPTEMBER 27, 2021
Microsoft Azure can provide a cloud-based file, folder and system backup recovery service at a reasonable price, if you can manage to work through a lengthy setup process.

Anoop
SEPTEMBER 28, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Easiest Method to Create SQL Queries for SCCM without Opening SQL Management Studio appeared first on HTMD Blog #1 by Anoop C Nair.

TechSpot
SEPTEMBER 30, 2021
At its Search On event this week, Google revealed details about how it plans to use a technology it calls Multitask Unified Model (MUM), which should intelligently figure out what a user is searching for based on images and text, as well as give users more ways to search for.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Tech Republic Security
SEPTEMBER 28, 2021
A new phishing campaign spotted by Armorblox tried to steal user credentials by spoofing a message notification from a company that provides email encryption.

Tech Republic Cloud
OCTOBER 1, 2021
The only way to get extended support for 2008 versions of Windows and SQL Server is in the cloud. Here's why you should be thinking about 2012 migrations now as well.

Anoop
SEPTEMBER 27, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Remove Recently Added Apps from Start Menu using Intune appeared first on HTMD Blog #1 by Jitesh Kumar.
The Verge
OCTOBER 1, 2021
“Google” is the most searched term on Bing “by far,” according to a lawyer working for Google’s parent company, Alphabet. According to Bloomberg , Google made the argument while trying to get its $5 billion antitrust fine from the EU overturned, using the statistic as evidence that people use Google by choice, not force. The fine Google faces is from the European Commission, which says that Google has abused its position as the maker of Android.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Tech Republic Security
SEPTEMBER 27, 2021
Dubbed TangleBot, the malware can overlay financial apps with its own screens in an attempt to steal your account credentials, says Cloudmark.

Tech Republic Cloud
OCTOBER 1, 2021
SMBs that rely on NAS hardware to store data will get a performance boost in the now available, and surprisingly affordable, WD Red SN700.

Anoop
SEPTEMBER 28, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post New Method to Install SCCM Console Extensions appeared first on HTMD Blog #1 by Anoop C Nair.

TechSpot
SEPTEMBER 29, 2021
Apple's been getting lazy in the iOS security department as of late, despite pouring fuel into the fiery iOS vs. Android debate by claiming the latter mobile OS has 47 times more malware due to being open to sideloading apps. That said, it's hard to argue against the fact that.

Advertisement
In the rapidly-evolving world of embedded analytics and business intelligence, one important question has emerged at the forefront: How can you leverage artificial intelligence (AI) to enhance your application’s analytics capabilities? Imagine having an AI tool that answers your user’s questions with a deep understanding of the context in their business and applications, nuances of their industry, and unique challenges they face.

GeekWire
SEPTEMBER 28, 2021
Trevor Bedford, infectious disease scientist at Fred Hutchinson Cancer Research Center. (Photo used with permission from the John D. and Catherine T. MacArthur Foundation). In the earliest days of the COVID-19 pandemic, as we desperately flailed for reliable information to comprehend what had previously been largely unimaginable, Seattle’s Trevor Bedford was a rare source of insight.

Gizmodo
SEPTEMBER 28, 2021
The Wall Street Journal on Tuesday published the latest in its investigative series “ The Facebook Files ,” diving even deeper into the ubiquitous platform’s efforts to target and recruit young children. Read more.

Anoop
SEPTEMBER 27, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post 3 Free SCCM Admin Tools for Advanced Troubleshooting appeared first on HTMD Blog #1 by Anoop C Nair.

TechSpot
OCTOBER 1, 2021
One area focused on within the report is the current state of Android malware. "It is an open source system with many vendors having their own Android versions (with their own vulnerabilities and patching problems)," Eset security awareness specialist Ondrej Kubovi? told The Register.

Advertiser: GEP
Generative AI goes beyond just automating tasks and providing real-time answers. Did you know that implementing generative AI reduces sourcing cycle times and allows for faster decision-making across procurement operations? In this whitepaper — Next-Gen Procurement: Transforming Processes With the Power of Generative AI — experts reveal how the strategic application of generative AI within procurement processes is paving the way for groundbreaking improvements.
Let's personalize your content