Data privacy is a growing concern for more consumers
Tech Republic Security
AUGUST 17, 2021
People surveyed by KPMG reported feeling increasingly uneasy about the data collection practices of corporations.
Tech Republic Security
AUGUST 17, 2021
People surveyed by KPMG reported feeling increasingly uneasy about the data collection practices of corporations.

Forrester IT
AUGUST 17, 2021
IBM's research found that when CEOs were asked to identify the most crucial members of the C-Suite, CMOs came in well behind their CFO and COO peers. But it doesn't have to be that way.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Association of Information Technology Professional
AUGUST 19, 2021
If you like numbers and digging deep into datasets, but also possess a need to be creative and satisfy your curiosity, then data analyst may be a good next step for you.
Anoop
AUGUST 19, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Microsoft Released Windows 11 ISO Ready to Download appeared first on HTMD Blog #1 by Anoop C Nair.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, CTO of Betterworks, will explore a practical framework to transform Generative AI prototypes into

Tech Republic Security
AUGUST 19, 2021
All departments of an organization need to be on the same page where cybersecurity is concerned, and that will only happen if the terminology used is understood by all.

Forrester IT
AUGUST 18, 2021
Forrester’s 2021 Global Marketing Survey revealed that three of the top five challenges regional teams face when implementing campaigns are the inability to develop campaigns based on customers’ needs, the lack of coordination across siloes, and a need for the right tools and technology to do the job well. As a result of these challenges, […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Anoop
AUGUST 18, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Windows 11 Intune Enrollment Process appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
AUGUST 19, 2021
As the predominantly pandemic-caused global chip shortage rolls on, businesses are now facing another challenge — component scams and bogus supply-chain claims.
Forrester IT
AUGUST 17, 2021
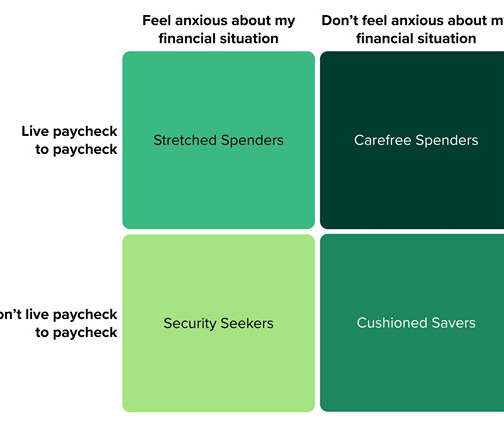
Forrester’s Financial Well-Being Segmentation helps firms better assess their customers’ level of financial resilience and attitude toward their financial situation.

Tech Republic Data Center
AUGUST 17, 2021
The top certification on the annual Skillsoft list has a salary of more than $171,000. Find out what certifications you should be working toward.

Speaker: Speakers:
They say a defense can be measured by its weakest link. In your cybersecurity posture, what––or who––is the weakest link? And how can you make them stronger? This webinar will equip you with the resources to search for quality training, implement it, and improve the cyber-behaviors of your workforce. By the end of the hour, you will feel empowered to improve the aspects of your security posture you control the least – the situational awareness and decision-making of your workforce.

Anoop
AUGUST 19, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Create Windows 11 Azure AD Device Group appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
AUGUST 20, 2021
To ensure business continuity amid high turnover, many CIOs are planning to alter their strategies to make the company "less dependent on employee institutional knowledge," says PwC.

Tech Republic Cloud
AUGUST 19, 2021
There aren't enough qualified AWS professionals to go around, so this affordable bundle can set you up a highly-paid tech career.

Tech Republic Data Center
AUGUST 18, 2021
Near-premises computing offers the robustness of a central data center at the edge. It's time to take a look at this option.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

Anoop
AUGUST 18, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Create SCCM Device Collection for Visual Studio Upgrade appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
AUGUST 16, 2021
Most organizations are still lacking talent, according to a new report, but experts think expanding the definition of a cybersecurity professional can help.
Tech Republic Cloud
AUGUST 20, 2021
Microsoft's Power BI helps professionals, including Apple users, better understand their data. Here's how users with an iPhone, iPad or Mac can take advantage of all Power BI offers.

Gizmodo
AUGUST 20, 2021
This week, a Swedish firm announced it had delivered carbon-free steel to a customer—a world-first. It’s a huge step in the race to clean up one of the most carbon-intensive activities on Earth. Read more.

Advertiser: GEP
Procurement and supply chain leaders are presented with their fair share of challenges, with a host of tools and strategies to resolve them. That said, what’s the best path forward to leverage this year’s trends? In this recap of a recent GEP-WBR webinar, 7 Leadership Themes for Procurement & Supply Chain Leaders in 2024, GEP’s Pramod Sethumadhavan explores seven vital leadership trends that will help guide procurement and supply chain decision-makers.

Anoop
AUGUST 17, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Create SCCM Report for Visual Studio appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
AUGUST 20, 2021
In response to a breach that compromised the personal data of millions of subscribers, T-Mobile customers should change their password and PIN and set up two-step verification.

Tech Republic Cloud
AUGUST 16, 2021
Complex systems need to be resilient, and we need to use tools like chaos engineering to ensure that resilience. Learn about Azure Chaos Studio.

The Verge
AUGUST 20, 2021
After a dense presentation about the undeniably impressive work Tesla is doing with AI, the company’s self-anointed Technoking, Elon Musk, capped the evening by bringing out a dancer in a spandex suit. Behold, said Musk: my Tesla Bot. The dancer in the suit, he said, was the model for a new humanoid robot Tesla will produce in the near future. After the dubstep and applause had faded, the vaguest of briefing slides promised that the Tesla Bot will stand five feet, eight inches (1.7m), weigh 125

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Anoop
AUGUST 16, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Easy Method to Deploy Visual Studio 2019 using SCCM appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
AUGUST 16, 2021
In recent months, a string of high-profile cyberattacks have targeted critical U.S. infrastructure. As students return to the classroom, could criminals look to focus their efforts on schools?

Tech Republic Cloud
AUGUST 18, 2021
Chrome OS has a hidden feature, inspired by the Linux desktop, that can make your work on the Chromebook a bit more efficient.

GeekWire
AUGUST 18, 2021
The International Space Station as seen from a departing Soyuz spacecraft. (NASA Photo). If your cell phone went out 17 times a day, for anywhere from 1 second to 20 minutes, you’d get a new wireless provider. That’s basically what astronauts on the International Space Station are dealing with, but they don’t have that option. That’s how Mark Fernandez of Hewlett-Packard Enterprise (HPE) explains the state of communications between the ISS and Earth — and it’s one r

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Anoop
AUGUST 17, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post SQL Query to Find Microsoft 365 Apps Details from SCCM appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
AUGUST 19, 2021
ThroughTek's Kalay is used to manage security cameras, baby monitors, DVRs and more. A newly discovered flaw lets attackers watch, listen and steal recordings from hardware sold by dozens of vendors.

Gizmodo
AUGUST 17, 2021
Back in July, cybersecurity researcher Bob Diachenko found what seemed to be a leaked FBI watchlist naming the personal details of close to 2 million suspected terrorists. Diachenko quickly filed a report to the Department of Homeland Security, hoping the agency would issue some sort of patch to keep this data from… Read more.

TechSpot
AUGUST 15, 2021
July is typically the hottest month each year, but this past July clocked in as the hottest July on record with a combined land and surface temperature of 1.67 degrees fahrenheit (0.93 degrees Celsius) above the 20th century average.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.
Let's personalize your content