How to make AI more ethical
Venture Beast
AUGUST 29, 2021
My team came up with these 5 ethical AI principles while developing our own framework. Your team may find them helpful. Read More.

Venture Beast
AUGUST 29, 2021
My team came up with these 5 ethical AI principles while developing our own framework. Your team may find them helpful. Read More.

Forrester IT
SEPTEMBER 3, 2021
In my past 30 years in the contact center industry at organizations like RingCentral, Genesys, 8×8, and IBM, I’ve watched the same movie over and over and over again…too many contact centers are laboring under the tyranny of being a cost center with schizophrenic goals of making customers happy while “doing more with less”. This […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
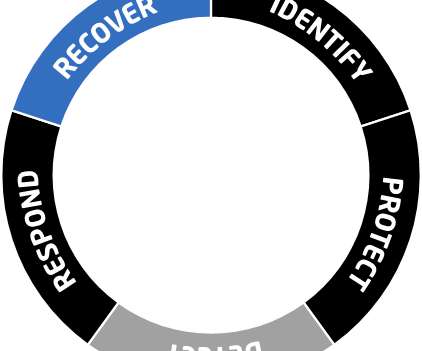
Association of Information Technology Professional
AUGUST 30, 2021
Dig into the five functions of the NIST Cybersecurity Framework and learn the types of tools IT pros can use to defend their organizations.

Anoop
SEPTEMBER 1, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Easiest Method to Create SCCM WQL Queries for Collection appeared first on HTMD Blog #1 by Anoop C Nair.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, CTO of Betterworks, will explore a practical framework to transform Generative AI prototypes into

Tech Republic Security
SEPTEMBER 3, 2021
Cybersecurity training is not the same across all companies; SMB training programs must be tailored according to size and security awareness. Here are an expert's cybersecurity training tips.

Forrester IT
SEPTEMBER 2, 2021
Will all of the digital urgency brought about by the pandemic disappear? Learn how AI can help drive creativity and innovation in your organization.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.
Anoop
AUGUST 30, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Translate SCCM Error Codes to Error Messages appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
AUGUST 31, 2021
Authentication sans password is already possible and solutions are on the market from companies like Ping Identity. With passwords passé, it's time to make the leap to better security.

Forrester IT
SEPTEMBER 2, 2021
Out of the 14 different spheres of influence that we track at Forrester, the channel industry trade press ranks near the top. Smart vendors and distributors know that the magic of finding, influencing, recruiting, enabling, and nourishing a top performing channel boils down to three simple questions about partners: What do they read? Where do […].

Tech Republic Cloud
AUGUST 30, 2021
If you frequently lose your tabs, Jack Wallen wants to remind you about pinned tabs and one behavior that can totally frustrate you with that feature.

Speaker: Speakers:
They say a defense can be measured by its weakest link. In your cybersecurity posture, what––or who––is the weakest link? And how can you make them stronger? This webinar will equip you with the resources to search for quality training, implement it, and improve the cyber-behaviors of your workforce. By the end of the hour, you will feel empowered to improve the aspects of your security posture you control the least – the situational awareness and decision-making of your workforce.

Anoop
SEPTEMBER 1, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Learn How to Resize Cloud PC Windows 365 appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
SEPTEMBER 3, 2021
Fail2ban should be on every one of your Linux servers. If you've yet to install it on either Rocky Linux or AlmaLinux, Jack Wallen is here to help you out with that.

Forrester IT
SEPTEMBER 2, 2021
Static annual plans often collect dust on a shelf. Leaning into the planning process can help you build a more dynamic and effective marketing plan that drives forward the objectives of the business.

Information Week
SEPTEMBER 2, 2021
Crunching sports data and making it presentable to tennis fans continues even with the return of live audience in the stands.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

Anoop
AUGUST 29, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post FIX: SCCM Task Sequence Failed to Run Command Line Error 0x8007010B appeared first on HTMD Blog #1 by Jitesh Kumar.

Tech Republic Security
AUGUST 31, 2021
Soft skills are just as important, if not more so, than technical skills in cybersecurity professionals. People with soft skills can be trained in tech skills, expert says.

Forrester IT
AUGUST 30, 2021
Many B2B marketers find joy in campaign planning — but not so much in budgeting. It turns out the two are intimately connected.

Tech Republic Cloud
SEPTEMBER 1, 2021
If you're a Google Docs power user who works with a Chromebook, this is one handy tip you'll want to implement.

Advertiser: GEP
Procurement and supply chain leaders are presented with their fair share of challenges, with a host of tools and strategies to resolve them. That said, what’s the best path forward to leverage this year’s trends? In this recap of a recent GEP-WBR webinar, 7 Leadership Themes for Procurement & Supply Chain Leaders in 2024, GEP’s Pramod Sethumadhavan explores seven vital leadership trends that will help guide procurement and supply chain decision-makers.

Anoop
AUGUST 30, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Easily Add Apply Driver Package Step to SCCM Task Sequence appeared first on HTMD Blog #1 by Jitesh Kumar.

Tech Republic Security
AUGUST 30, 2021
Microsoft 365's "secure by default" stance removes some tools used by security teams. Here's how to work around the new restrictions.

TechSpot
SEPTEMBER 3, 2021
A court in Alexandria, Virginia, ruled that inventions can only be patented under the name of a "natural person." The decision was made against someone who tried to list two designs under the name of an AI as part of a broader project to gain worldwide recognition of AI-powered inventions.

Gizmodo
SEPTEMBER 3, 2021
After users threatened to boycott the internet domain service GoDaddy for hosting the newly-established tip line that allows Texans to anonymously snitch on private citizens they suspect of performing an abortion after six weeks or anyone who “aids or abets” such abortions in the state, the company abruptly announced… Read more.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Anoop
SEPTEMBER 2, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post How to Reprovision Cloud PC Windows 365 appeared first on HTMD Blog #1 by Anoop C Nair.

The Verge
SEPTEMBER 3, 2021
Photo by PATRICK T. FALLON/AFP via Getty Images. In case you haven’t heard, Texas now has a law that makes it illegal for anyone to help women get an abortion after six weeks of pregnancy — and to take advantage of that, the anti-abortion group Texas Right to Life is encouraging citizens to report those people at a dedicated “whistleblower” website, promising to “ensure that these lawbreakers are held accountable for their actions.”.

TechSpot
SEPTEMBER 1, 2021
The Surveillance Legislation Amendment (Identify and Disrupt) Bill 2020 gives the Australian Federal Police (AFP) and the Australian Criminal Intelligence Commission (ACIC) powers to modify, add to, copy, or delete data to "frustrate the commission of serious offenses online." To gather evidence of suspected criminal activity, they also have the.

GeekWire
SEPTEMBER 1, 2021
(Carbon Robotics Photos). Investors are putting more cash behind the self-driving weed-zapping machines made by Carbon Robotics that are attracting attention from farmers across the world. The Seattle-based startup just landed $27 million to help meet demand. Its AI-powered autonomous robot uses computer vision software to identify weeds growing in fields, and then zaps them with precision 150-watt thermal bursts from lasers.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Anoop
AUGUST 31, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post KB10503003 Hotfix Released for SCCM 2107 Early Ring appeared first on HTMD Blog #1 by Anoop C Nair.

Gizmodo
SEPTEMBER 1, 2021
Even if you don’t live in Texas, you’ve likely heard about the state’s draconian abortion restrictions that officially went into effect on Wednesday. The so-called “Heartbeat Bill,” aka Senate Bill 8 , makes it fully illegal for anyone—friends, family, doctors—across Texas to help women access an abortion in the state… Read more.

TechSpot
SEPTEMBER 1, 2021
Bleeping Computer writes that someone was offering to sell the PoC on a hacker forum recently. They didn't reveal too many details about the tool, though they did note that it works by allocating address space in the GPU memory buffer to store malicious code and executes it from there.

GeekWire
AUGUST 30, 2021
Solo team members, from left: Keith Ng (co-founder), Araceli Benitez (growth lead), Bryce Bennett (CEO & co-founder), Keith Ho (software engineer), and Thushara Wijeratna (founding & lead engineer). (Solo Photos). Gig economy companies such as Uber, Instacart, goPuff and others have given workers a new way to earn money on their own schedule.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.
Let's personalize your content