5 Tips for Understanding and Maximizing Data
Information Week
JUNE 12, 2020
To harness the power of data analytics, companies need to create a culture in which all employees understand how to use data to advance business outcomes.

Information Week
JUNE 12, 2020
To harness the power of data analytics, companies need to create a culture in which all employees understand how to use data to advance business outcomes.

Tech Republic Security
JUNE 11, 2020
A password alone will not protect sensitive information from hackers--two-factor authentication is also necessary. Here's what security pros and users need to know about two-factor authentication.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
JUNE 8, 2020
The soft economy just gave cloud adoption a shove. Get ready for more autonomous IT resources.

Forrester IT
JUNE 10, 2020
Companies have short attention spans when it comes to data governance. Even for organizations with sustained programs, the continuous push and pull of new regulations, projects, or data and analytics investments create constant disruption. To address these expansions, data owners either search for the simple approach or re-educate on data governance 101.

Speaker: Speakers:
They say a defense can be measured by its weakest link. In your cybersecurity posture, what––or who––is the weakest link? And how can you make them stronger? This webinar will equip you with the resources to search for quality training, implement it, and improve the cyber-behaviors of your workforce. By the end of the hour, you will feel empowered to improve the aspects of your security posture you control the least – the situational awareness and decision-making of your workforce.
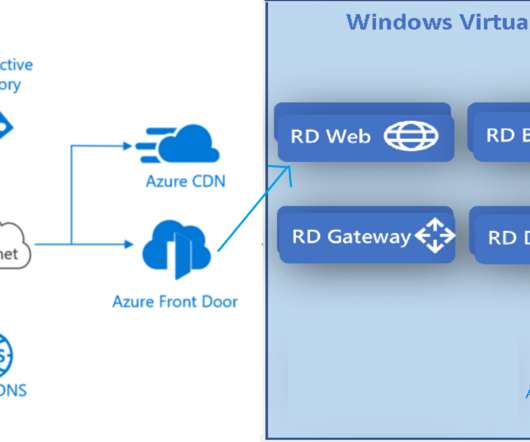
Anoop
JUNE 9, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Well, it’s not officially WVD v2, instead, it’s new Portal for WVD with new Admin Experience. However, the WVD architecture for the 2020 spring update is changed significantly with the WVD spring release. WVD New Arm Object Model The following are the main changes in the high-level architecture with Windows Virtual Desktop spring release (a.k.a […].

Tech Republic Security
JUNE 8, 2020
The CFO of a small company that was the victim of a ransomware attack and reveals why they paid the ransom (in Bitcoin) to gain back control of their systems.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Forrester IT
JUNE 10, 2020
We are currently at the beginning of Phase Three (Management) as regions and businesses reopen. This is a challenging transition for organizations. A global pandemic has no clear end. To help with your pandemic recovery plans, Forrester developed two sets of pandemic management protocols for bringing employees back. Government guidelines along with health and safety risks are undoubtedly top of mind, but there’s more.
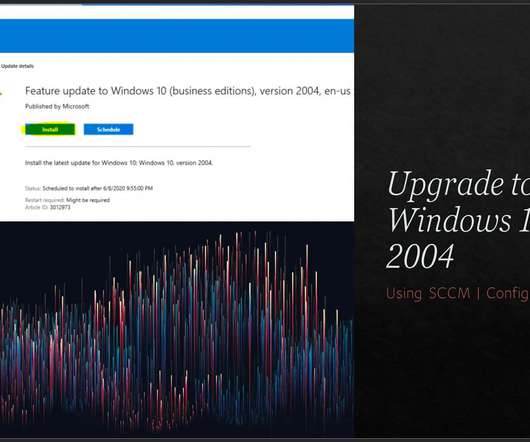
Anoop
JUNE 8, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s learn how to upgrade to Windows 10 2004 using SCCM. You can use Windows 10 servicing plans to keep Windows 10 up to date and secured. Windows 10 2004 is the latest version of Windows 10. You can manage Windows as a service using ConfigMgr (A.K.A Configuration Manager).

Tech Republic Security
JUNE 11, 2020
COVID-19 has completely changed the work world, but many organizations have seemingly failed to realize that security risks are changing as well, a new report finds.

Information Week
JUNE 12, 2020
In the argot of today's technology world, transformation is about "People + Machine." The machine alone is, well, just a machine.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

Forrester IT
JUNE 11, 2020
It has been a year since Japan moved to a new era: “Reiwa” and quite a lot has happened during the past 12 months. As Japanese leading banks roll out initiatives to help consumers and SMEs cope with the fallout from the COVID-19 pandemic, they also face an urgent need for digital transformation to serve […].

Anoop
JUNE 12, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. HTMD Community along with Altaro giving an opportunity to the followers! Well, there is another option to Win some money for online purchases for Office 365 User. To receive a guaranteed $25 Amazon voucher, sign up to a free trial of Altaro Office 365 Backup and answer these two questions correctly!
Tech Republic Security
JUNE 12, 2020
Only 37% of "high performer" organizations monitor the risk of IoT devices used by third parties, and current IoT risk-management programs can't keep pace, study said.

Information Week
JUNE 8, 2020
5G networks and the substantial shift to remote operations are making edge computing a new frontier for digital transformation in the enterprise.

Advertiser: GEP
Procurement and supply chain leaders are presented with their fair share of challenges, with a host of tools and strategies to resolve them. That said, what’s the best path forward to leverage this year’s trends? In this recap of a recent GEP-WBR webinar, 7 Leadership Themes for Procurement & Supply Chain Leaders in 2024, GEP’s Pramod Sethumadhavan explores seven vital leadership trends that will help guide procurement and supply chain decision-makers.

Forrester IT
JUNE 11, 2020
By understanding what customer advocates value, you can invite them to participate in the ways that are most meaningful to them, and to you.

Anoop
JUNE 11, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. How many use PowerShell script to deploy some quick fixes. Let’s find out a solution to Fix SCCM Script Approve Deny Button is Disabled. More details about Fix SCCM Pre-Release Features are Grayed Out | Enable | ConfigMgr. Problem Statement I do have full admin access on Configuration Manager (a.k.a SCCM), but still, I don’t […].

Tech Republic Security
JUNE 11, 2020
The COVID-19 pandemic has affected many tech career fields. Learn how it has impacted cybersecurity professionals, and how to help.

The Verge
JUNE 12, 2020
Photo by Ethan Miller/Getty Images. Elon Musk’s Boring Company is already looking to dig more tunnels in Las Vegas, Nevada, after it finished excavating the first two under the city’s convention center last month. Clark County Commissioner Tick Segerblom tweeted a map last week that shows a proposed set of tunnels that would run west from the Las Vegas Convention Center (LVCC) to the Wynn and the Encore, hotel casinos owned by Wynn Resorts.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

GeekWire
JUNE 11, 2020
Queen guitarist (and astrophysicist) Brian May, a member of the New Horizons science team, uses his patented OWL viewer to check out the stereo images of Proxima Centauri that he created by combining pictures from Earth-based telescopes and the New Horizons spacecraft. (Photo courtesy of Brian May, via New Horizons / JHUAPL / SwRI / NASA). NASA’s New Horizons probe has measured the distance to nearby stars using a technique that’s as old as the ancient mariners, but from a vantage po

Anoop
JUNE 10, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s find out how to fix ConfigMgr Sites that don’t have a Proper HTTPS Configuration issue. I have noticed this error when I was going through management insights. I have seen this issue with SCCM 2004 version. ConfigMgr Management Insights will help you to gain valuable insights into the current state of the SCCM environment.

Tech Republic Security
JUNE 12, 2020
A honeypot created by Cybereason to lure cybercriminals and analyze their methods showed that ransomware attacks infiltrate their victims in multiple stages.

The Verge
JUNE 11, 2020
Sony is finally revealing what the PlayStation 5 looks like. After nearly an hour of PS5 game announcements, Sony revealed the hardware design after teasing it for the duration of its PS5 live event today. The PS5 console includes a white-and-black design to match the new controller that will be included in the box. The PS5 stands vertically, like the Xbox Series X is primarily designed to be placed, and will include two versions: one with a 4K Blu-ray drive and a pure Digital Edition.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
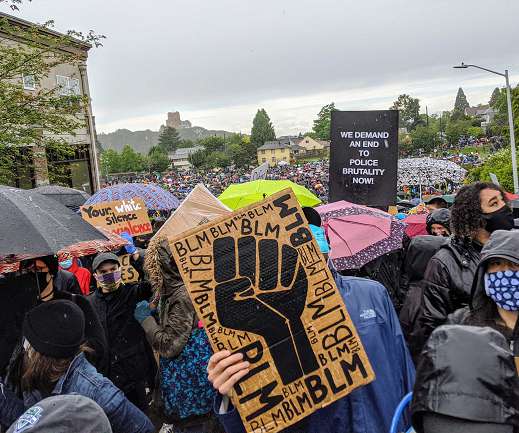
GeekWire
JUNE 12, 2020
Thousands of protesters take part in a “March of Silence” in Seattle on Friday afternoon, the vast majority wearing masks. (GeekWire Photo / Monica Nickelsburg). Seattle Mayor Jenny Durkan’s office says it’s seeing no evidence so far that protesters are testing positive for COVID-19 at higher rates than normal after attending protests.

TechSpot
JUNE 11, 2020
Back in 2018, Apple’s stock price got a boost after its revenue grew 17 percent year-over-year. The increase led to its value reaching an amazing $1 trillion. One month later, Amazon became the next US tech giant to join the trillion-dollar club. Since then, both Microsoft and Alphabet have also.

Tech Republic Security
JUNE 10, 2020
The automaker's customer service and financial services are unavailable as it deals with an attack that experts believe is ransomware.
Gizmodo
JUNE 9, 2020
White supremacy is baked into science and academia, from racist language in textbooks to a culture that excludes Black scientists from innovating and advancing at the same pace as their colleagues. But rather than more milquetoast statements and diversity initiatives, researchers want action. Organizers are asking… Read more.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.

GeekWire
JUNE 10, 2020
(Instacart Photo). Instacart said it may not be able to continue operating in Seattle if a law requiring hazard pay for delivery workers passes next week. The grocery delivery company warned customers about the “unconstitutional legislation” in an email urging them to write to the Seattle City Council in opposition to the bill. “Your access to same-day grocery delivery is at risk,” Instacart said.

The Verge
JUNE 8, 2020
Illustration by Alex Castro / The Verge. IBM will no longer offer general purpose facial recognition or analysis software, IBM CEO Arvind Krishna said in a letter to Congress today. The company will also no longer develop or research the technology, IBM tells The Verge. Krishna addressed the letter to Sens. Cory Booker (D-NJ) and Kamala Harris (D-CA) and Reps.

Tech Republic Security
JUNE 11, 2020
With increased use, phony apps and banking trojans will try to steal account credentials, according to the FBI.

Gizmodo
JUNE 6, 2020
Today, Black families are most likely to live surrounded by toxic air pollutants extractive industries discharge into their backyards. Black people face a more immediate threat whenever they leave their homes: the police. To disconnect the two is irresponsible. Polluting industries don’t wind up in Black communities… Read more.

Advertiser: GEP
Generative AI goes beyond just automating tasks and providing real-time answers. Did you know that implementing generative AI reduces sourcing cycle times and allows for faster decision-making across procurement operations? In this whitepaper — Next-Gen Procurement: Transforming Processes With the Power of Generative AI — experts reveal how the strategic application of generative AI within procurement processes is paving the way for groundbreaking improvements.
Let's personalize your content