Here's how a new machine learning software can beef up cloud-based databases
Tech Republic Data Center
JUNE 5, 2020
A Purdue data team just developed a way for organizations to improve performance and efficiency through cloud-hosted databases.
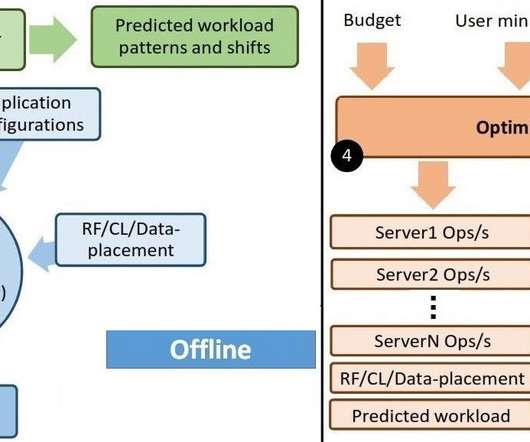
Tech Republic Data Center
JUNE 5, 2020
A Purdue data team just developed a way for organizations to improve performance and efficiency through cloud-hosted databases.

Forrester IT
JUNE 1, 2020
The communications industry is facing a perfect storm of converging forces, from COVID-19 to the rise of influencer marketing and even AI. At Forrester, we research around 10,000 global technology vendors that utilize indirect sales and often get asked about the value of PR in the channel. A trend that is affecting many channel leaders […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Anoop
JUNE 1, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. In this post, You will learn about bare metal deployment using the configuration manager (Windows 10 2004 Using SCCM). The bare metal scenario occurs when you have a blank machine you need to deploy or an existing machine you want to wipe and redeploy without needing to preserve any existing data.

Tech Republic Security
JUNE 3, 2020
Cybersecurity, remote IT troubleshooting and cloud support will be the most sought-after skills for businesses in the months following the COVID-19 pandemic, according to a survey of CIOs and tech executives.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, CTO of Betterworks, will explore a practical framework to transform Generative AI prototypes into

Information Week
JUNE 1, 2020
Artificial intelligence and ML can help us take DevOps to the next level through identifying problems more quickly and further automating our processes.

Forrester IT
JUNE 4, 2020
In March 2020, as the implications of a global shutdown of physical offices became apparent, executives responsible for digital initiatives went into overdrive. If your firm is already digitally advanced, it’s likely to be faring far better than less advanced competitors by now. But no matter where your firm is today on it’s pandemic-induced digital […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Tech Republic Security
JUNE 4, 2020
Aimed at SMBs, educational facilities, and software companies, the ransomware leverages Java to encrypt server-based files, according to BlackBerry and KPMG.

Tech Republic Cloud
JUNE 1, 2020
The sudden shift to remote work has accelerated digital transformation strategies for many organizations, Citrix study finds.

Forrester IT
JUNE 2, 2020
It’s been more than two months since corporate America’s unexpected leap into the deep end of the remote work pool. Behind the backdrops of our endless video calls, we’ve been juggling unexpected incursions from children, pets, and other household activities. Despite the occasional drama, we’ve been largely successful at adapting to this new paradigm, answering […].

Anoop
JUNE 4, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s learn who modified App Deployment from ConfigMgr. You can find out who created, modified, deleted the configuration manager Applications. Related Post – Who Deleted Updated Modified SCCM Collection & Who Deleted ConfigMgr Task Sequence & Learn Who Modified ConfigMgr Task Sequence Deployment Who Created Deployment of Application Use SQL Management studio to understand who […].

Speaker: Speakers:
They say a defense can be measured by its weakest link. In your cybersecurity posture, what––or who––is the weakest link? And how can you make them stronger? This webinar will equip you with the resources to search for quality training, implement it, and improve the cyber-behaviors of your workforce. By the end of the hour, you will feel empowered to improve the aspects of your security posture you control the least – the situational awareness and decision-making of your workforce.

Tech Republic Security
JUNE 3, 2020
A phishing email claims to send the recipient to a VPN configuration page for home access but instead leads them to a credential-stealing site, said Abnormal Security.

Information Week
JUNE 1, 2020
Data scientists, machine learning specialists and other data and analytics pros are seeing a changes to the job market in the wake of the COVID-19 crisis. What will the lasting impacts be?

Forrester IT
JUNE 1, 2020
Let’s just say that one measure of the hype that surrounds any emerging technology is the amount of new (and largely superfluous) jargon that it generates. Enterprise automation market needs pragmatic advice The market for Robotic Process Automation (RPA) has been in hypergrowth for a while now. RPA, and its extension into intelligent automation (IA), […].

Anoop
JUNE 3, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s learn who Modified ConfigMgr Modified ConfigMgr Client Settings. You can find who created, modified, deleted the configuration manager client settings from this post. Related Post – Who Deleted Updated Modified SCCM Collection & Who Deleted ConfigMgr Task Sequence & Learn Who Modified ConfigMgr Task Sequence Deployment Who Created ConfigMgr Client Settings Use SQL Management […].

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

Tech Republic Security
JUNE 4, 2020
Malicious files masquerading as curriculum vitae are being sent to businesses to install malware that can capture passwords and other sensitive information, says Check Point Research.

Information Week
JUNE 2, 2020
You can't wait for the world to go back to "normal" or expect your old metrics to work in the future. Listen intently, experiment relentlessly, and spread your bets.

Tech Republic Cloud
JUNE 1, 2020
If you want to build software that is more resilient, agile, and faster, you can do just that with microservice architecture.
Anoop
MAY 31, 2020
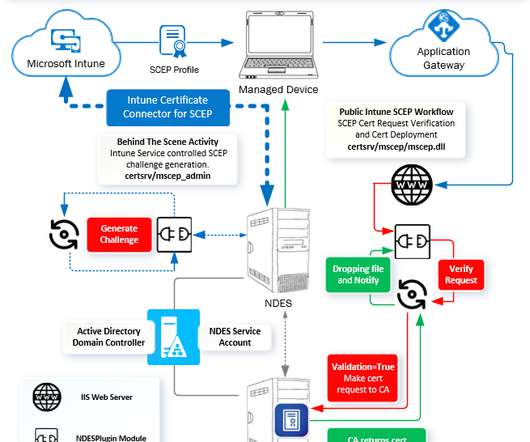
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. [New Post Alert!] Intune SCEP Certificate Workflow Made Easy With Joy - Part 4. The post Intune SCEP Certificate Workflow Analysis – Intune PKI Made Easy With Joy – Part 4 appeared first on How to Manage Devices by Joymalya Basu Roy.

Advertiser: GEP
Procurement and supply chain leaders are presented with their fair share of challenges, with a host of tools and strategies to resolve them. That said, what’s the best path forward to leverage this year’s trends? In this recap of a recent GEP-WBR webinar, 7 Leadership Themes for Procurement & Supply Chain Leaders in 2024, GEP’s Pramod Sethumadhavan explores seven vital leadership trends that will help guide procurement and supply chain decision-makers.

Tech Republic Security
JUNE 4, 2020
A new partnership with Dedrone has led to a platform that can instantly detect and notify security personnel of drones in sensitive airspace.

Information Week
JUNE 4, 2020
Almost overnight, companies pivoted to remote work, but long-term viability requires an all-in commitment to digital transformation across technology and culture.

Tech Republic Data Center
JUNE 3, 2020
Recovering data isn't something any IT pro wants to face. But when the occasion arises, you'll be glad Linux is around to give you a hand.

Tech Republic Cloud
JUNE 5, 2020
These eight areas will net fast budget reductions with minimal disruption to the business and headcount.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Tech Republic Security
JUNE 3, 2020
Unauthorized access was the most common type of attack in 2019, and it was responsible for 40% of all data breaches, says ForgeRock.

TechSpot
JUNE 5, 2020
Slack and Amazon have struck a multi-year agreement, where the latter will adopt Slack for in-house communication for its AWS teams and will provide additional services to Slack for expanding its footprint in the enterprise workspace. Once Amazon's rollout to its employees is complete, the company could potentially overtake IBM.

The Verge
JUNE 5, 2020
Illustration by Alex Castro / The Verge. Facebook is limiting the spread of pages and groups linked with the word “boogaloo,” an internet slang term used in some far-right extremist circles to refer to the idea of an impending second American Civil War, as first reported by Reuters. The boogaloo term has since evolved into a disjointed anti-government movement with various and at times conflicting views.

Tech Republic Cloud
JUNE 1, 2020
A new report from Yellowbrick examines the impact the coronavirus has had on the technology industry.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Tech Republic Security
JUNE 1, 2020
According to a Tessian survey, data protection concerns go out the window for remote employees.

GeekWire
JUNE 4, 2020
Rich Reynolds, an employee of James G. Murphy Auctioneers, keeps an eye on the thermal vacuum chamber in the machine shop at Planetary Resources’ former HQ in Redmond, Wash. (GeekWire Photo / Alan Boyle). REDMOND, Wash. — Wanna buy a used thermal vacuum chamber? If you have a sudden yen to replicate outer-space conditions, it behooves you to check out today’s online-only auction of the hardware left over from Planetary Resources , the Redmond venture that aimed to create a trillion-d

Gizmodo
JUNE 3, 2020
The ACLU has filed a class-action lawsuit against Minnesota authorities on behalf of journalists whom state and local police were filmed beating, shooting, gassing, and arresting during protests against the police killing of George Floyd. Read more.

The Verge
JUNE 4, 2020
Illustration by William Joel / The Verge. The comments came during a town hall meeting amid the George Floyd protests On Wednesday, LinkedIn hosted a town hall about racial justice in the wake of the police killing of George Floyd. The forum was supposed to be an opportunity for employees to come together and discuss how they could support one another.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.
Let's personalize your content