Why Data Science Isn't an Exact Science
Information Week
JULY 27, 2020
Organizations adopt data science with the goal of getting answers to more types of questions, but those answers are not absolute.

Information Week
JULY 27, 2020
Organizations adopt data science with the goal of getting answers to more types of questions, but those answers are not absolute.

Forrester IT
JULY 29, 2020
Forrester’s view on the future of banking is here – examining the changes that we expect to play out over the next decade of retail banking. The drivers of the future are evolutions of the past – some playing out now, others that will be far more prominent by 2025 and table stakes by 2030. […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
JULY 28, 2020
Read about the saga of Facebook's failures in ensuring privacy for user data, including how it relates to Cambridge Analytica, the GDPR, the Brexit campaign, and the 2016 US presidential election.
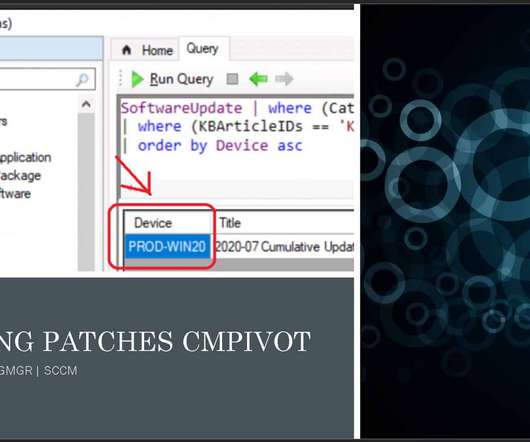
Anoop
JULY 28, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s Find Missing Patches using ConfigMgr CMPivot Query. I have seen many questions in HTMDForum that we want the patch report using the SQL query. In this post, you will learn how to use the SCCM CMPivot query to find out missing patches. You can customize the CMPivot query as per your need and requirement.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, CTO of Betterworks, will explore a practical framework to transform Generative AI prototypes into
Tech Republic Cloud
JULY 31, 2020
Microsoft has provided more information on Dataflex, its new low-code platform for building apps and bots directly within Teams.
Forrester IT
JULY 28, 2020
Prioritization is the art and science of making decisions, an active process of choosing one thing over another. Just like we all need some form of prioritization in our day-to-day activities, whether we’re thinking about how to tackle our current day’s workload or household chores, companies need prioritization processes and approaches that ensure decisions are […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Anoop
JULY 31, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s learn how to troubleshoot out of band hotfix installation logs. You can find more details about the troubleshooting steps in this blog post. SCCM Troubleshooting Out of Band Hotfix Logs | ConfigMgr. NOTE! – More details available Dmpdownloader.log ( DMP Downloader Troubleshooting with State Messages).

Information Week
JULY 29, 2020
Here's how IT leaders can better manage the bias that becomes embedded in algorithms and datasets to help increase opportunities for minority tech professionals.

Forrester IT
JULY 31, 2020
Low-code platforms speed delivery of applications, but are they secure? The answer is more complicated than I expected when I started this research project with my colleagues, John Bratincevic and John R. Rymer. We’re still gathering information, but we’ve discovered that: Low-code security is not well understood. Even vendors with extensive security investments acknowledged that […].

Tech Republic Security
JULY 29, 2020
A recent investigation by NordPass and a white hat hacker discovered more than 9,000 unsecured databases online with more than 10 billion individual entries.

Advertisement
While data platforms, artificial intelligence (AI), machine learning (ML), and programming platforms have evolved to leverage big data and streaming data, the front-end user experience has not kept up. Holding onto old BI technology while everything else moves forward is holding back organizations. Traditional Business Intelligence (BI) aren’t built for modern data platforms and don’t work on modern architectures.
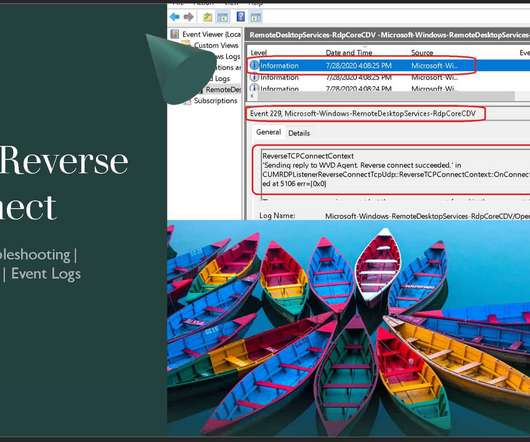
Anoop
JULY 30, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s quickly go-through the WVD event logs using TCP Reverse Connect technologies. You can check this internal process of RDP connection through the secure channel from Windows 10 devices. I have a WVD Troubleshooting Options Tips Tricks – Windows Virtual Desktop in the previous post.

Tech Republic Cloud
JULY 31, 2020
Commentary: Diamanti started off as a way to make on-premises Kubernetes deployments sing. Now it's aiming to extend that to the cloud.

Forrester IT
JULY 28, 2020
A decade ago I completed the first ever assessment of Australia’s emerging “trusted” or private Infrastructure-as-a-Service (IaaS) market. I followed this up with a 2010 opinion-editorial calling for improved “cloud computing regulation” in Australia as a model for global oversight of a hugely important market segment.

Tech Republic Security
JULY 31, 2020
New survey finds that cybersecurity professionals want more training to keep up with the threat landscape and learn new software platforms.

Advertiser: GEP
Procurement and supply chain leaders are presented with their fair share of challenges, with a host of tools and strategies to resolve them. That said, what’s the best path forward to leverage this year’s trends? In this recap of a recent GEP-WBR webinar, 7 Leadership Themes for Procurement & Supply Chain Leaders in 2024, GEP’s Pramod Sethumadhavan explores seven vital leadership trends that will help guide procurement and supply chain decision-makers.
Anoop
JULY 29, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. If you are working as an SCCM Admin in your organization, you might have been asked to create custom reports (Create Custom Report Using Report Builder) according to customer requirements. As an admin, some create WQL queries and some prefer to work on SQL Queries and achieve their desired results.

Tech Republic Data Center
JULY 28, 2020
Microsoft has announced long-term commitments to reduce its carbon footprint. Recent data center hydrogen fuel cell tests take another step toward these goals.

Forrester IT
JULY 28, 2020
The novel coronavirus shut down the US economy, freezing US consumer spending. This, however, is a temporary situation – consumers will resume spending when it is safe again for them to conduct regular commerce. So, the question customer experience (CX) professionals must ask their businesses is, “Are we positioned to recapture our clients once they […].
Tech Republic Security
JULY 29, 2020
PQShield, a spin-out from the UK's Oxford University, is developing advanced cryptographic solutions for hardware, software and communications to protect businesses' data from the quantum threat.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Anoop
JULY 30, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s see how to create a custom SCCM Client Version Dashboard using a report builder and SQL query. Since the release of the Configuration Manager Current Branch, admins must analyze and keep their environment to the latest version of the client along with the server.

The Verge
JULY 30, 2020
Google is launching a new tool that allows businesses to identify themselves as Black-owned through the company’s Maps and Search listings. The new feature is part of the company’s pledge announced last month to support the Black community with “initiatives and product ideas that support long-term solutions.”. When searching for a business through Google.com or Google Maps, you’ll now be able to see a new badge to represent Black-owned businesses — it’s a black heart over an orange three-striped

Forrester IT
JULY 30, 2020
Marketers today must understand and use myriad technologies to support omnichannel ad strategies and deliver moments-based marketing. But the landscape of 7,000+ options is overwhelming and rapidly evolving, especially as new privacy regulations and tech giants like Apple and Google limit access to consumer data. We just published some research to help marketers keep up. […].

Tech Republic Security
JULY 29, 2020
Dr. David Brumley, a professor at Carnegie Mellon University and CEO of ForAllSecure, explains what DevSecOps is and how companies can use it to improve security.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Anoop
JULY 27, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s understand how to Fix SCCM Duplicate Records when Co-Management & Tenant Attach is enabled. Microsoft recently released a new hotfix for ConfigMgr 2002. The KB 4575339 hotfix is released to fix the co-managed devices that are duplicated in the Microsoft Endpoint Manager admin center.

GeekWire
JULY 30, 2020
A United Launch Alliance Atlas 5 rocket sends NASA’s Mars Perseverance rover into space from its launch pad at Cape Canaveral Air Force Station in Florida. (ULA Photo). With the fiery flash of a rocket launch, NASA’s Perseverance rover headed out today for what’s expected to be a decade-long campaign to store up and bring back Martian samples that may hold evidence of alien life.

Gizmodo
JULY 28, 2020
In 2018, the world’s collective heart broke for Tahlequah, a Southern Resident killer whale in the Pacific Northwest that’s formal name is J35. The mama whale carried around her dead calf for more than two weeks. Now, Tahlequah is pregnant again. Read more.

Tech Republic Security
JULY 31, 2020
Professionals in the aerospace and defense industries should watch out; a wave of fake job offers containing malicious documents have been spotted in the wild by McAfee researchers.

Advertisement
In the rapidly-evolving world of embedded analytics and business intelligence, one important question has emerged at the forefront: How can you leverage artificial intelligence (AI) to enhance your application’s analytics capabilities? Imagine having an AI tool that answers your user’s questions with a deep understanding of the context in their business and applications, nuances of their industry, and unique challenges they face.

The Verge
JULY 28, 2020
Fool an algorithm today: wear a mask. | Photo by Robin Utrecht/SOPA Images/LightRocket via Getty Images. Face masks are one of the best defenses against the spread of COVID-19, but their growing adoption is having a second, unintended effect: breaking facial recognition algorithms. Wearing face masks that adequately cover the mouth and nose causes the error rate of some of the most widely used facial recognition algorithms to spike to between 5 percent and 50 percent, a study by the US National

GeekWire
JULY 29, 2020
Zillow’s downtown Seattle offices in the Russell Investments Center, left, as seen from the nearby Pike Place Market. (GeekWire Photo / Kurt Schlosser). Zillow Group introduced a new policy on Wednesday allowing about 90% of its employees the option of working from home indefinitely, significantly extending a move the company made at the end of April in response to the coronavirus pandemic.

Gizmodo
JULY 26, 2020
Guillermo del Toro’s Frankenstein. The idea alone gives you chills. It’s been the director’s dream project for as long as he’s been asked the question, and the subject came up again at this weekend’s virtual San Diego Comic-Con. Del Toro explained a bit more about how he’d adapt the Mary Shelley book for the big… Read more.

Tech Republic Security
JULY 31, 2020
Experts weigh in to share their thoughts on the hottest topics to expect at this year's all-digital Black Hat conference.

Advertiser: GEP
Generative AI goes beyond just automating tasks and providing real-time answers. Did you know that implementing generative AI reduces sourcing cycle times and allows for faster decision-making across procurement operations? In this whitepaper — Next-Gen Procurement: Transforming Processes With the Power of Generative AI — experts reveal how the strategic application of generative AI within procurement processes is paving the way for groundbreaking improvements.
Let's personalize your content