6 Best Authenticator Apps for 2024
Tech Republic Security
MARCH 26, 2024
Authenticator apps provide an extra layer of security. Learn about the best authenticator apps to secure your online accounts and protect your privacy.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
MARCH 26, 2024
Authenticator apps provide an extra layer of security. Learn about the best authenticator apps to secure your online accounts and protect your privacy.

Tech Republic Security
APRIL 2, 2024
Discover the top passwordless authentication solutions that can enhance security and user experience. Find the best solution for your business needs.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IT Toolbox
MAY 1, 2024
On the occasion of World Password Day 2024, tech experts from around the world discuss the growing redundancy and alternatives to conventional passwords. The post World Password Day 2024: Tech Leaders Discuss Password Obsolescence and Alternatives appeared first on Spiceworks Inc.

Tech Republic Security
MARCH 20, 2024
Explore top multi-factor authentication solutions for enhanced security and user authentication. Learn about the benefits and features of leading MFA providers.

CIO Business Intelligence
JANUARY 22, 2024
The remote work revolution has pushed companies to rethink their security and data protection practices amidst hybrid work and cloud environments. trillion by 2025, as cyber risk management has not kept up with digital transformation posing serious risks to organizations’ security and revenue.

Tech Republic Security
SEPTEMBER 24, 2024
Implementing multi-factor authentication, supplier risk-management frameworks, and staff security training could help to reduce data breaches.

The Verge
AUGUST 17, 2021
Mastercard is phasing out the use of magnetic stripes on its credit and debit cards over the next decade, as the industry moves towards more secure or convenient alternatives like chips and contactless payments, the company has announced. It says it will be the first payments network to phase out the technology, which dates back to the 1960s.

Network World
MARCH 8, 2021
That led the global company, which has locations in more than 100 countries, to become an early adopter of the network-security architecture dubbed secure access service edge ( SASE ) by research firm Gartner. Tech Spotlight: Security. WFH security lessons learned from the pandemic (Computerworld).

CIO Business Intelligence
AUGUST 21, 2024
The security professional shortage Some 3.5 This drives up wages, making it both expensive to hire security professionals and difficult to retain them. Given the nature of their business, costs for security are baked into the business model. million in 2024 1 – and thus take the necessary steps to reduce cyber risk.

CIO Business Intelligence
DECEMBER 5, 2024
One Identity named Hot Company: Privileged Access Management (PAM) in 12th Cyber Defense Magazines Annual InfoSec Awards during CyberDefenseCon 2024. We are deeply honored to be recognized amongst the winners of the 12th annual Cyber Defense Awards at CyberDefenseCon 2024, said Mark Logan, CEO of One Identity. Ackerman Jr.

SecureWorld News
JANUARY 10, 2024
I have always known about physical security keys, also called hard tokens, but never actually used one despite my curiosity. So, I was kind of excited when I got my hands on two cool things: a YubiKey 5 and a Google Titan security key. The platforms I tested with these two security keys are Microsoft 365 (M365), Google, and Twitter.

Kitaboo
FEBRUARY 22, 2024
In this blog, we will discuss the various strategies and best practices for securing online books. Types of eBook Protection Strategies to Explore in 2024 Digital Rights Management (DRM) Watermarking Securing eBook Files Secure Distribution Platforms Limit eBook Downloads III. Table of Contents: I.

SecureWorld News
OCTOBER 1, 2024
When we're talking security, we often overlook a basic fact of human beings: the best protection strategies won't work if no one is paying attention. Cybersecurity and Infrastructure Security Agency (CISA). And one thing we know is that it's time to center our security awareness programs around your audience. Our 2024 Oh Behave!

Tech Republic Security
DECEMBER 11, 2024
Keepers extensive authentication options and generous discounts make it an alluring password manager to try this year. Read more about it in our full review.

CIO Business Intelligence
JULY 1, 2024
These details are from the Check Point 2024 Cyber Security Report , which paints a combination of grim prospects and optimism. This means the need to adopt a new paradigm in securing IT infrastructures. SD-WAN is neither inherently secure nor naturally prone to attacks.

SecureWorld News
AUGUST 15, 2024
The breach, which allegedly occurred in April 2024, has raised significant concerns about data security and identity theft risks. However, in a concerning development, a version of the stolen data was reportedly leaked for free on a hacking forum in early August 2024. Enable multi-factor authentication (MFA) wherever possible.

SecureWorld News
JULY 17, 2024
As the 2024 Olympics approach, the world's eyes will turn to Paris. Increased attack surface The 2024 Paris Olympics will involve a massive digital infrastructure, including ticketing systems, live-streaming platforms, and IoT devices used in venues. The challenges can be broadly categorized into several key areas.

CIO Business Intelligence
JUNE 3, 2024
However, amidst the allure of newfound technology lies a profound duality—the stark contrast between the benefits of AI-driven software development and the formidable security risks it introduces. This dichotomy underscores the need for a nuanced understanding between AI-developed code and security within the cloud-native ecosystem.

CIO Business Intelligence
JULY 22, 2024
Ninety percent of customers do not, according to one 2024 study , but 78% said they’d be more likely to share their data with a company they trust. A fraudster beats out Knowledge-based Authentication (KBA) to illegally obtain access to a customer’s account. Malicious outside criminals (a.k.a.

Network World
JANUARY 14, 2025
In 2024, we witnessed a remarkable acceleration in cyberattacks of all types, many fueled by advancements in generative AI. For security leaders, the stakes are higher than ever. Before diving in, lets reflect on a few 2024 predictions that rang true, shaping lessons we carry forward into the new year.

SecureWorld News
JANUARY 16, 2024
The clock is ticking for organizations worldwide as a maelstrom of cybersecurity compliance deadlines looms in 2024. From data privacy regulations to payment card security standards, businesses of all sizes must scramble to implement new protocols and strengthen their defenses against cyber threats. Hold onto your credit cards!

Network World
OCTOBER 11, 2024
In the first half of this year, 38% of organizations had at least one cloud workload that was critically vulnerable, highly privileged, and publicly exposed, according to a study of telemetry from customers of cloud security vendor Tenable released this week. used to standardize on a security baseline.”

Kitaboo
FEBRUARY 21, 2024
Protecting your digital content helps you prevent piracy, combat unauthorized access to content, manage distribution rights, and securely share valuable content with users across the globe. It’s a powerful tool for authors, publishers, and content creators across different industries, ensuring your investments are secure in 2024.

CIO Business Intelligence
AUGUST 29, 2024
Unlike traditional one-time passwords (OTPs), which have become increasingly vulnerable to phishing, SIM swapping, and message interception, payment passkeys utilize biometric data stored on a user’s device to authenticate transactions. This growing threat has made it imperative for companies to innovate around payment security.

Dataconomy
FEBRUARY 26, 2024
In light of the recent ISC chemistry 2024 paper leak, the HindustanTimes has reported a significant update: the ISC Chemistry Paper 1 (Theory) exam, originally slated for Monday (February 26) at 2 pm, has been unexpectedly postponed. How did ISC chemistry 2024 paper leak surface?

Kitaboo
MAY 7, 2024
If you are looking to learn more about document security systems and the challenges it poses, you’re at the right place. In this comprehensive guide, we will cover multiple aspects of document security, its features, and challenges. What Is the Security of Documents and Information? Why Is Document Security Important?

SecureWorld News
MAY 2, 2024
World Password Day, observed annually on the first Thursday of May, serves as a crucial reminder to buck these poor password habits and prioritize better password security. Additionally, enabling multi-factor authentication (MFA) whenever possible adds a critical second layer of security beyond just a password.
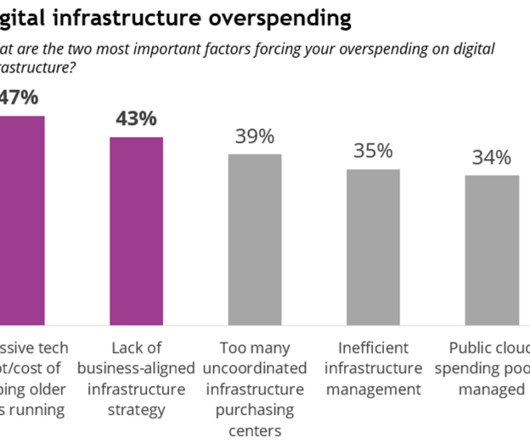
CIO Business Intelligence
AUGUST 1, 2024
Looking ahead to the next 12-18 months, two top priorities emerge for IT leaders: developing a strong business case for AI infrastructure spending (cited by 35% of respondents to IDC’s Future Enterprise Resiliency and Spending Survey, Wave 3 , March 2024) and increasing cyber resilience and security (34%).

SecureWorld News
JULY 8, 2024
This unprecedented leak has put the cybersecurity community and beyond on high alert—as if it was not already there—highlighting the ongoing need for robust digital security practices. Fast forward to 2024, and the scale of the latest leak dwarfs its predecessor by several orders of magnitude.

CIO Business Intelligence
AUGUST 29, 2024
Then there are the potential security vulnerabilities that go hand-in-hand with frequent lockouts, password resets, and re-verifications. When you add multi-factor authentication (MFA) resets to the picture, that number is likely even higher. But what happens when a user can’t access their authenticator app?

SecureWorld News
JANUARY 10, 2024
Securities and Exchange Commission's (SEC) account on X (formerly Twitter) was briefly compromised on Tuesday, January 9, sending shockwaves through the cryptocurrency market and raising serious questions about the agency's cybersecurity practices. Additionally, promoting transparency in response to security incidents is crucial.

Network World
OCTOBER 21, 2024
AI, security, energy-efficient computing , robotics, and virtual computing interactions are among the research firm’s top 10 strategic technology trends, which were unveiled at Gartner’s annual IT Symposium/XPO in Orlando. Disinformation security Gartner’s third hot topic is also related to AI: disinformation security.

SecureWorld News
MAY 28, 2024
In the advisory , Check Point says the attackers are targeting security gateways with old local accounts using insecure password-only authentication, which should be used with certificate authentication to prevent breaches. "We We have recently witnessed compromised VPN solutions, including various cyber security vendors.

Kitaboo
MAY 7, 2024
The integrity of personal data and proprietary information is increasingly jeopardized, necessitating robust measures for secure content distribution. Since its development by Martin Dougiamas in 2002, Moodle has risen to become one of the top learning management systems of 2024. Wrapping Up What is Moodle?

CIO Business Intelligence
SEPTEMBER 9, 2024
According to IDC’s Worldwide AI and Generative AI Spending Guide (August 2024) , the global AI market is expected to surge from US$235 billion in 2024 to US$632 billion by 2028. billion in 2024 to over US$110 billion by 2028.

Kitaboo
MARCH 28, 2024
These solutions help publishers and authors secure their content and protect eBooks from unauthorized distribution. How DRM Protects eBook Content Encryption License Management Digital Watermarking Authentication Mechanisms IV. Our secure cloud-based distribution ensures that your content is DRM-protected and encrypted.

Kitaboo
FEBRUARY 21, 2024
Blockchain for Content Authenticity: As misinformation becomes a growing concern, blockchain technology can be employed to verify the origin and ownership of content, providing readers with confidence in the information they consume.

Network World
SEPTEMBER 19, 2024
Additional features such as encryption and authentication over WPA3 Enterprise further strengthen Wi-Fi security. One significant milestone occurred when the Wi-Fi Alliance approved its certification standard in January 2024. There have been a number of Wi-Fi 7 developments this year.

SecureWorld News
JULY 2, 2024
This trend reflects improved business security practices, evolving insurance industry dynamics, and changing attitudes toward cyber risk management. Interestingly, this downward trend in premiums comes despite an 18% increase in recorded ransomware incidents during the first five months of 2024 compared to the previous year.

Dataconomy
NOVEMBER 6, 2024
Google Cloud is set to make multi-factor authentication (MFA) mandatory for all users by 2025, a move aimed squarely at bolstering security in response to escalating cyber threats. This phased enforcement plan underscores a broader industry trend: when it comes to security, relying solely on passwords is a thing of the past.

SecureWorld News
OCTOBER 8, 2024
There is a growing disconnect between the increasing sophistication of cybersecurity threats and the preparedness of IT teams to combat them, according to the O'Reilly 2024 State of Security Survey report which surveyed more than 1,300 IT professionals. of respondents identified cloud security as the most significant skills shortage.

Dataconomy
JANUARY 16, 2025
The Cash App Class Action Settlement is a response to alleged security and data misuse issues affecting millions of users in the United States. parent company of Cash App) is paying $15 million to settle claims related to data breaches that occurred between August 23, 2018, and August 20, 2024. Who is eligible for settlement claims?
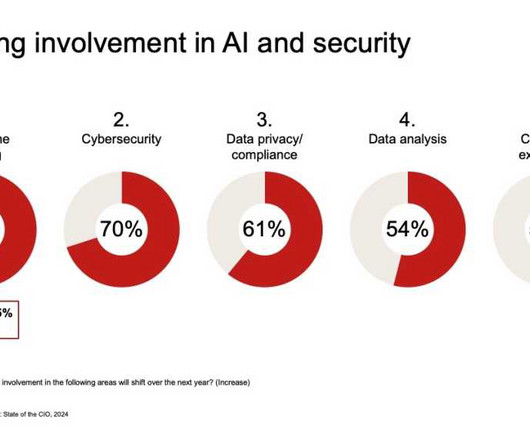
CIO Business Intelligence
MAY 20, 2024
Nearly half (49%) of IT leaders responding to the 2024 State of the CIO Study from Foundry, publisher of CIO.com, say they expect to play more of a strategic role in the upcoming years, with another 36% anticipating a heavy emphasis on transformational responsibilities. Other surveys offer similar findings. Foundry / CIO.com 3. For Rev.io

CIO Business Intelligence
SEPTEMBER 12, 2023
Over 100,00 organizations are expected to be impacted by Network and Information Security Directive (NIS2) cybersecurity standards that European Union (EU) member states must implement by October 2024. [i] This concept of least-privilege access is fundamental to Zero Trust Security practices.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content