Rethinking enterprise architects’ roles for agile transformation
CIO Business Intelligence
SEPTEMBER 17, 2024
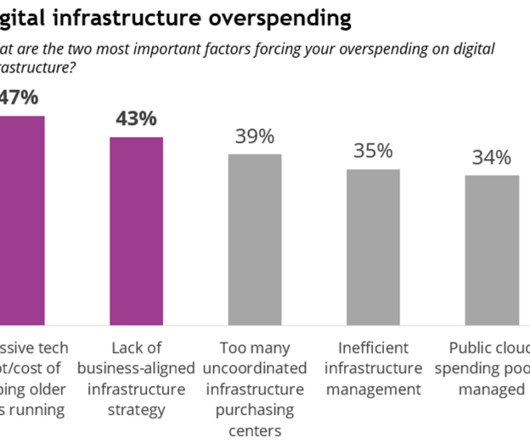
On the one hand, enterprise architects play a key role in selecting platforms, developing technical capabilities, and driving standards. Moreover, undertaking digital transformation and technology modernization programs without an architect can lead to delays, technical debt , higher costs, and security vulnerabilities.


















































Let's personalize your content