Introducing Maintenance for Agile Applications
Information Week
MAY 3, 2024
At what point does continuous, iterative development for Agile applications turn into a maintenance exercise?
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Information Week
MAY 3, 2024
At what point does continuous, iterative development for Agile applications turn into a maintenance exercise?
Network World
MARCH 25, 2025
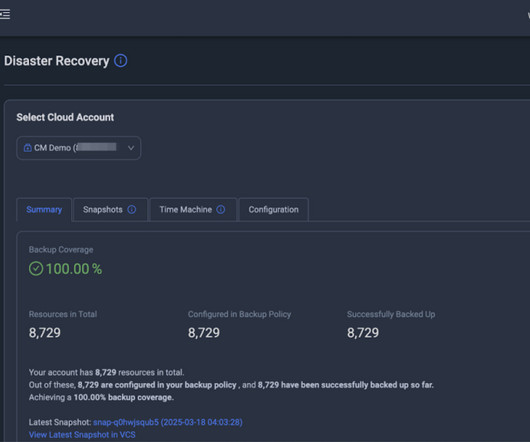
Today the company launched its automated disaster recovery technology specifically engineered for cloud infrastructure configurations, addressing a common blind spot in enterprise disaster recovery strategies that typically focus primarily on data or application protection. Twizer claims that ControlMonkey can do it in one-click.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Network World
MARCH 13, 2025
It takes a lot of expensive research and development to create new materials. And theres no shortage of applications for new discovery of magnetic materials, says Alan Baratz, CEO at D-Wave Quantum, a company that makes annealing-style quantum computers. Its not just a theoretical exercise. It solves a real-world problem.

CIO Business Intelligence
APRIL 2, 2025
The guide addresses four phases of software ownership: software supply chains, development practices, deployment, and vulnerability management, and says they help organizations buying software better understand their software manufacturers approach to cybersecurity, and ensure that secure by design is a core consideration. Prouty asks.
CIO Business Intelligence
DECEMBER 10, 2024
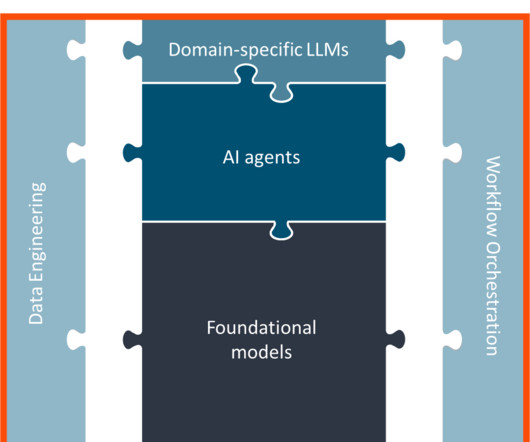
to GPT-o1, the list keeps growing, along with a legion of new tools and platforms used for developing and customizing these models for specific use cases. The rise of vertical AI To address that issue, many enterprise AI applications have started to incorporate vertical AI models. From Llama3.1 to Gemini to Claude3.5

CIO Business Intelligence
NOVEMBER 19, 2024
Microsoft is describing AI agents as the new applications for an AI-powered world. While that is true, your development teams may not be ready to implement yet. Development teams starting small and building up, learning, testing and figuring out the realities from the hype will be the ones to succeed.
CIO Business Intelligence
OCTOBER 5, 2023
Consider both the upsides and downsides to every disruptive innovation and develop applications that are smart, secure, and sustainable, without losing your focus on solving real-world challenges,” says Low Jin Phang, President, Digital Systems, ST Engineering. To find out more about ST Engineering Digital Systems, visit [link].

Network World
AUGUST 13, 2024
You can’t say you’ve tested unless you’ve exercised all these paths. Of 89 enterprise development managers who shared comments with me, all said they had to deal with this in their own testing, and they’d expect a software supplier to be even more careful than an end user. The same thing has to be considered in multi-cloud.

CIO Business Intelligence
JUNE 21, 2024
INE Security , a leading global cybersecurity training and cybersecurity certification provider, predicts large language model (LLM) applications like chatbots and AI-drive virtual assistants will be at particular risk. “AI As automated attacks increase, our defense strategies must also be automated and intelligent.

CIO Business Intelligence
FEBRUARY 3, 2025
src="[link] alt="alex tan" loading="lazy" width="400px"> Alex Tan Group Chief Information Officer (Yinson) As 2025 unfolds, we foresee a shift in the technology landscape: The generative AI (genAI) frenzy will give way to pragmatic applications, commencing with bespoke in-house chatbots that streamline operations.

Network World
SEPTEMBER 18, 2024
By thinking and acting like attackers, red teams provide valuable insights into an organization’s security posture and help develop effective countermeasures. Improving overall security posture: The insights gained from red team exercises can be used to enhance security policies, procedures, and technologies.

CIO Business Intelligence
DECEMBER 20, 2023
Albeit emerging recently, the potential applications of GenAI for businesses are significant and wide-ranging. Generative AI can help businesses achieve faster development in two main areas: low/no-code application development and mainframe modernisation. percent of the working hours in the US economy.

CIO Business Intelligence
DECEMBER 9, 2024
They have to be really good at that stop-start-continue exercise. Such connected devices and the digital world as a whole are running on millions upon millions of lines of code that have not undergone the same rigorous development and review as those that ran that early medical device, according to Wilson. But they know that thats OK.

Network World
JUNE 13, 2024
In the cyber world, this translates to performing lateral propagation to gain access to crown-jewel applications. Stage 4: This is when the thieves make their getaway with large sums of money, which is just like how cybercriminals steal large volumes of data from these crown-jewel applications that they can then use to commit extortion.

CIO Business Intelligence
JULY 26, 2023
That said, many of the participants pointed out the need to develop a common enterprise-wide “cloud-native” approach to managing and securing their heterogeneous environments. This objective can be accomplished by inviting broader segments of the corporate community to security tabletop exercises.

CIO Business Intelligence
JULY 5, 2024
We developed an algorithm to measure our different applications based on these 12 categories so we can eliminate technical debt via a more strategic and standardized approach,” she says, noting that the goal was to do away with any guesswork and make decisions based on opportunities and potential revenue risks. “We

SecureWorld News
DECEMBER 30, 2024
This may involve identifying compromised servers, web applications, databases, or user accounts. ISO 22398: Covers the principles of planning, conducting, and developing training programs to prepare teams for critical situations through practical exercises and simulations. Introduce MFA for all corporate accounts.

CIO Business Intelligence
APRIL 16, 2024
For each of these efforts, teams would develop plans, get estimates, and ultimately obtain the budgetary approval needed to get started. If an application is critical to a business, it’s not something that can be treated as a one-and-done project. Teams don’t just deploy the application and move on.

CIO Business Intelligence
SEPTEMBER 17, 2024
On the one hand, enterprise architects play a key role in selecting platforms, developing technical capabilities, and driving standards. They also have a well-defined means for collaborating with agile development teams and can work with them to deliver a roadmap of improvements tied to technical debt remediations.

Network World
FEBRUARY 10, 2025
Replacing a network management tool is not a trivial exercise, especially in large and complex networks. Their applications lived in on-premises data centers, and they connected remote sites via managed WAN services with service-level agreements (SLA). It can take months to install and tune a tool so that it is delivering value.

CTOvision
FEBRUARY 4, 2014
Application Software Security. href="[link] Control 6: Application Software Security. Penetration Tests and Red Team Exercises. href="[link] Control 20: Penetration Tests and Red Team Exercises. Patching Applications: Patching of applications must be continuously maintained. Malware Defenses.

CIO Business Intelligence
AUGUST 8, 2024
The process would start with an overhaul of large on-premises or on-cloud applications and platforms, focused on migrating everything to the latest tech architecture. For the past 10-15 years, business transformation initiatives have been the sole mandate of the technology team. This is a massive change in conventional business practices.

CIO Business Intelligence
NOVEMBER 29, 2023
Once enterprises commit to running business-critical applications in the cloud, they rarely move to another provider. But if you do your planning exercise properly, you shouldn’t have to move your applications around,” he says. In this case you have to re-architect the application before you can migrate it.

CIO Business Intelligence
AUGUST 26, 2024
I focused this exercise on three primary areas: Business support. How do we ensure that our technology infrastructure, applications, security posture and core IT operations are not only up to industry standards but also positioned to drive the long-term success of our business? Innovation.

CIO Business Intelligence
MARCH 8, 2023
It’s about making sure there are regular test exercises that ensure that the data backup is going to be useful if worse comes to worst.” As part of this exercise, organizations need to prepare adequate response plans and enforce the requisite best practices to bring the business back online. Shore up a data protection strategy.
CIO Business Intelligence
AUGUST 29, 2024
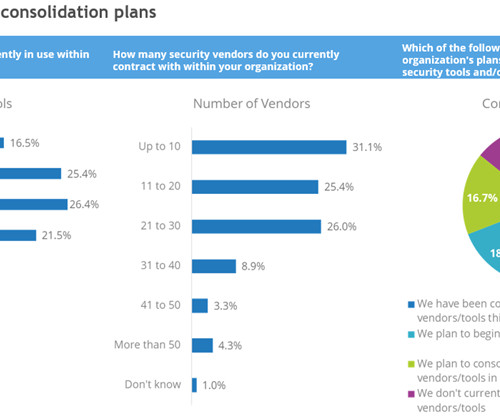
SaaS application management tools, which identify all SaaS apps purchased and used by the organization. They can also identify redundant applications or licenses. This is where it pays to use the recommendations that resulted from the security tool rationalization exercise. Others hire an outside specialist.

CIO Business Intelligence
FEBRUARY 27, 2024
And AI poster child Sam Altman is lobbying for a $7 trillion investment in AI chip development. I begin the AI hysteria detox with a series of exercises trying to place the technology moment in which we find ourselves in historical context. I ask executives to recount their “most memorable experience with emerging technologies.”

CIO Business Intelligence
MARCH 16, 2023
Private 5G is the next evolution of networking for mission-critical applications used in factories, logistics centers and hospitals. It’s also a much simpler exercise to reconfigure connectivity between devices and improve the timing and synchronization of data feeds from sensors.

CIO Business Intelligence
MAY 11, 2022
Establishing development and deployment processes. Businesses should also examine their software development and deployment processes for sustainability gains. For example, tools like AWS Codeguru help profile applications and frameworks and provide automatic recommendations on potential improvements.

CIO Business Intelligence
DECEMBER 6, 2024
Develop an AI platform and write a gen AI playbook to allow it to move quickly without shortchanging on security and governance measures. Muthukrishnan and his team developed three simple guiding principles: Experiment with intern-facing use cases first, always have a human in the middle, and never expose any Ally data externally to LLMs.

CIO Business Intelligence
SEPTEMBER 29, 2022
Waqar Qureshi, General Manager for Network & Technology at Horizon Energy Group, says they have developed a work-from-home policy for their organisation which includes awareness and responsibilities for accessing, storing and sharing the data/information. Educating your organisation is key.

CIO Business Intelligence
DECEMBER 18, 2024
This involves establishing guardrails around AI, performing disaster training exercises, mitigating third-party threats, and more. And while 99% of packages have updated versions available, 80% of application dependencies remain un-upgraded for over a year.

CIO Business Intelligence
APRIL 26, 2023
Treating training as a checkbox exercise sends the message to your team that you don’t really care all that much about the content they’re learning — and that mindset is contagious,” warns Steve Ryan, a manager at BARR Advisory, a cloud-based security and compliance solutions provider. Don’t fear attrition — fear stagnation, Ávila advises.

CIO Business Intelligence
MARCH 21, 2023
Many organizations still retain significant amounts of data, applications, and workloads on premises, even as they continue migrating to the cloud. If they migrated applications, now they can refactor them for the cloud,” he says. “If The cloud is at an inflection point, Schwartz states.

CIO Business Intelligence
MARCH 15, 2022
Any set of predictions about the coming months is by definition always a fraught exercise, and we know at Broadcom Software to always expect the unexpected. That’s why it’s so vital to develop a security plan that starts with the assumption that a breach has occurred. Composable applications become all the rage.

CIO Business Intelligence
SEPTEMBER 24, 2024
The issue began early Monday morning when a key SSL certificate expired and affected the company’s Management, Instrumentation, and Discovery (MID) Server, leaving users unable to integrate applications, access updates, and manage critical operations. The company notified its customers in an advisory admitting the issue.

SecureWorld News
OCTOBER 13, 2024
The synergy of AI and VR Integrating AI into VR experiences is a project that many developers have begun experimenting with. As these technologies mature and intersect, industry-wide applications could be far more groundbreaking. Regular testing and validation of AI models is crucial.

CIO Business Intelligence
OCTOBER 26, 2023
Some of the top BI certifications include: Certified Business Intelligence Professional (CBIP) IBM Data Analyst Professional Certificate Microsoft Certified: Power BI Data Analyst Associate QlikView Business Analyst SAP Certified Application Associate: SAP BusinessObjects Business Intelligence Platform 4.3
GeekWire
NOVEMBER 4, 2024
The 12 finalists were selected from applicants that were required to have founders in Whatcom or Skagit counties. The remaining finalists: Synapse Software previewed Slingshot, a no-code business process automation platform for small and mid-sized businesses that don’t have a “small army” of developers.

CIO Business Intelligence
JULY 23, 2024
At the same time, it allows exercising appropriate control and supervision that permits maintaining standards of quality and robustness.” “It gives business areas the agility and autonomy to extract value from information without waiting, without dependencies, and without bottlenecks,” he says. “At

CIO Business Intelligence
JANUARY 10, 2024
Migrating infrastructure and applications to the cloud is never straightforward, and managing ongoing costs can be equally complicated. Refactoring applications to take advantage of cloud-native services is vital to maximizing cloud ROI. The requesting team works only at the application layer.

CIO Business Intelligence
SEPTEMBER 12, 2022
Company leadership also creates space and time for employees to innovate by dedicating a team of people to explore emerging technologies, run experiments, and identify business applicability, Crowe says. Now the capability is embedded in the product development process. IT is in the throes of launching a couple of mobile apps.

CIO Business Intelligence
MARCH 19, 2024
For instance, Ethan Mollick tried this 30-minute experiment more than a year ago and revisited it recently with a sub-1-minute exercise. As the end user constructing the prompts, you’re going to create a content roadmap for a new mobile application. Log into genAI applications in 5 browser windows (one for each piece of content).

CIO Business Intelligence
AUGUST 14, 2024
Between building gen AI features into almost every enterprise tool it offers, adding the most popular gen AI developer tool to GitHub — GitHub Copilot is already bigger than GitHub when Microsoft bought it — and running the cloud powering OpenAI, Microsoft has taken a commanding lead in enterprise gen AI. That’s risky.”
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content