Governance and Fighting the Curse of Complexity
CIO Business Intelligence
MARCH 20, 2024
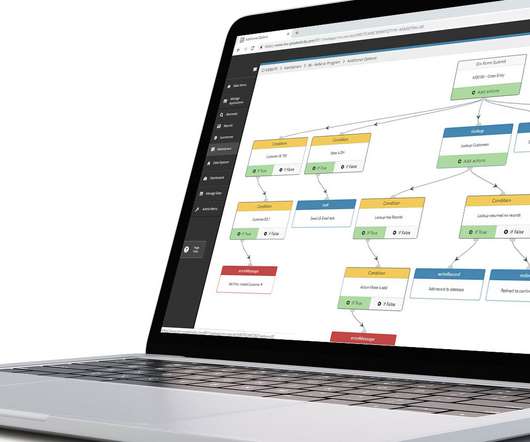
The road other is paved with disciplined IT and business governance. Shadow IT introduces systems and applications that are often outside of an enterprise’s catalog of IT tools. There will always be new computing paradigms: think of virtual reality or robotics or quantum computing. Password strategies. Incident response plans.



































Let's personalize your content