Announcing the Modern Application Development Services Vendor Landscape, Q3 2024
Forrester IT
AUGUST 1, 2024
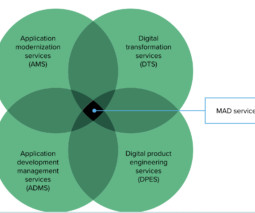
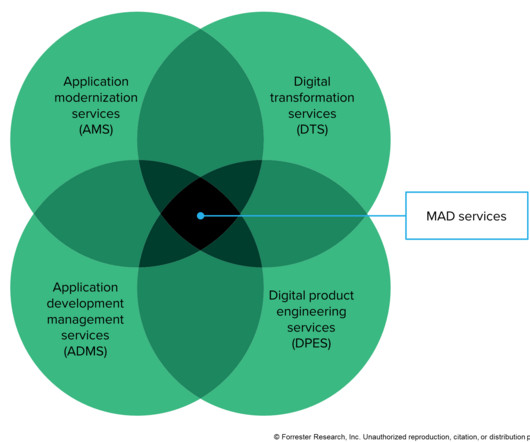
Modern Application Development Services Defined Clients want more autonomy to better control their own innovation and development capabilities to build modern and up-to-date custom applications.

















































Let's personalize your content