Our Top Recommendations For Your Security Program: CISOs Get An Offer They Can’t Refuse
Forrester IT
APRIL 6, 2022
The Scorsese classic has a few surprising parallels with today's chief information security officer.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Forrester IT
APRIL 6, 2022
The Scorsese classic has a few surprising parallels with today's chief information security officer.

SecureWorld News
OCTOBER 24, 2023
At the end of the day, it turned out that this was the work of the company's information security team, aimed at showing management how simply attackers could gather data for targeted phishing campaigns. Consequently, the task of enhancing employee security awareness often lands on the shoulders of information security or IT teams.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Forrester IT
JUNE 8, 2017
In a world where infrastructure-as-code scales quickly and massively scales, it is crucial to bake in security at every level of the stack. This means leveraging automation tools such as configuration management and application release automation, as well as applying Zero Trust principles all the way down to the bare metal.

CTOvision
MARCH 27, 2014
Position Summary: The Internet2 Chief Cyberinfrastructure Security Officer (CCSO) is the leader responsible for establishing the cyberinfrastructure security strategy and direction for Internet2′s global infrastructure programs.

CTOvision
NOVEMBER 10, 2016
New Capital Infusion to Expand Platform Ecosystem, Sales and Digital Risk Applications. This financing will enable the company to expand its ecosystem, global sales, and platform applications within the disruptive Digital Risk Management market. With that in mind we share a RiskIQ press release below -bg. Million in Series C Funding.

CIO Business Intelligence
MAY 24, 2024
A variety of roles in the enterprise require or benefit from a GRC certification, such as chief information officer, IT security analyst, security engineer architect, information assurance program manager, and senior IT auditor , among others.

ForAllSecure
DECEMBER 15, 2021
What’s needed is autonomous application security. We need an application security testing solution that is able to accurately identify issues at speed and scale. Unlike automation, autonomous capabilities encompasses more than doing a pre-programmed task at the machine speed. Autonomous is not Automation.

CIO Business Intelligence
OCTOBER 1, 2024
With each passing day, new devices, systems and applications emerge, driving a relentless surge in demand for robust data storage solutions, efficient management systems and user-friendly front-end applications. Yet, even if we run the same tool on 100 different applications, the tool hardly ‘learns’ from each test!

CIO Business Intelligence
JULY 25, 2024
Exam fee: $450 plus a $50 application processing fee Expiration: Three years Certified Associate in Project Management (CAPM) As an IT manager, you’ll be responsible for overseeing multiple IT projects during your career.
Network World
JULY 9, 2024
The layers help network pros visualize what is going on within their networks and can help network managers narrow down problems (is it a physical issue or something with the application?), as well as computer programmers (when developing an application, which other layers does it need to work with?).

CTOvision
DECEMBER 5, 2014
Insights include: IoT – Internet Of Things will become practical as government figures how to extend applications, solutions and analytics from the Gov Enterprise & Data Centers. We manage public sector programs that deliver higher operational efficiency and measurable value to clients.

CIO Business Intelligence
OCTOBER 31, 2023
When an application is finally ready for deployment, the last thing the development team wants to hear is: “Stop! There’s a security issue.” And then, after months of painstaking work, their application launch is delayed even further. We realize there are multiple ways to address a specific vulnerability.
CIO Business Intelligence
NOVEMBER 2, 2023
In the ever-evolving realm of information security, the principle of Least Privilege stands out as the cornerstone of safeguarding sensitive data. However, this fundamental concept, emphasizing limited access to resources and information, has been progressively overlooked, placing our digital ecosystems at greater risk.

CTOvision
AUGUST 15, 2014
For healthcare professionals participating in the Centers for Medicare & Medicaid Services electronic health record (EHR) incentive program, you’ll soon need to demonstrate compliance with the Stage 2 Meaningful Use requirements in order to continue receiving incentive payments. Network Security. By William McElmurry.

CIO Business Intelligence
MARCH 25, 2024
The CSO30 Awards ceremony is an exclusive invitation-only event for leading security decision-makers in enterprises across the Middle East who have demonstrated the highest standards of competence in the domain of cyber and information security. Europe, ASEAN, Asia/Pacific, India, and a host of other countries.

CIO Business Intelligence
SEPTEMBER 17, 2024
Moreover, undertaking digital transformation and technology modernization programs without an architect can lead to delays, technical debt , higher costs, and security vulnerabilities. Many organizations create program charters for strategic initiatives in which they define the program’s leadership roles and accountabilities.

CTOvision
DECEMBER 23, 2014
Pete Jobse, CIT President and CEO and MACH37™ Executive Chairman, said, “MACH37 has created a unique public-private program that brings together domain experts, successful cybersecurity entrepreneurs, and investors familiar to the security market to create a platform that enables next generation technology to be deployed more rapidly.

CIO Business Intelligence
AUGUST 30, 2024
INE Security is pleased to announce that it has been recognized as a 2024 SC Award finalist in the Excellence Award category for Best IT Security-Related Training Program.

SecureWorld News
SEPTEMBER 5, 2023
Arun DeSouza is the Chief Information Security Officer and Chief Privacy Officer for Nexteer Automotive. He has been a CISO for 20 years and has extensive global IT and security leadership and transformation experience. Organizations can help by supporting via scholarships and co-op programs.

CIO Business Intelligence
SEPTEMBER 7, 2023
By including a wide range of participants who represent different facets of how AI is being used, unique use cases, and differing perspectives, we can create AI guardrails applicable across business units within Discover. Visit Discover Technology to learn more about Discover’s approach to security, AI, reliability and more.

CTOvision
DECEMBER 15, 2014
An autonomic computing system would control the functioning of computer applications and systems without input from the user, in the same way that the autonomic nervous system regulates body systems without conscious input from the individual. Application Streaming / Virtualization. 3D Printing Design & Implementation.

CIO Business Intelligence
MAY 27, 2024
If there is a single theme circulating among Chief Information Security Officers (CISOs) right now, it is the question of how to get stakeholders on board with more robust cybersecurity training protocols. Highlighting the potential financial losses from breaches and the ROI of training programs can make a compelling case.

GeekWire
APRIL 3, 2024
F5 Photos) — Seattle-based application security and delivery giant F5 announced two new executive appointments this week: Lyra Schramm , the company’s new chief people officer, and Kunal Anand , chief technology officer. Techstars announced one month later that it was shutting down the Seattle program. Sarah Studer.

CIO Business Intelligence
JUNE 20, 2024
That necessitates end-to-end solutions that encompass connectivity, cloud applications, security, data management, support services, and the specialized expertise that is needed to guide them throughout their entire cloud journey. For more information on CITIC Telecom CPC, please visit here.
Dataconomy
NOVEMBER 13, 2024
Google and Microsoft have committed to hybrid work arrangements The disconnect between executives and employees regarding AI’s application Interestingly, Slack’s report highlights a notable disconnect in the expectations between executives and their teams.

CIO Business Intelligence
MARCH 24, 2023
The Business Application Research Center (BARC) warns that data governance is a highly complex, ongoing program, not a “big bang initiative,” and it runs the risk of participants losing trust and interest over time. The program must introduce and support standardization of enterprise data.

SecureWorld News
JUNE 24, 2024
The TRIAD Model During my career as a CISO, I relied on my TRIAD Model to envision, enact, and mobilize Information Security & Privacy strategic planning and roadmap execution activities with foundational pillars as illustrated below. I – Identity A cornerstone of a strong security and privacy program.

CIO Business Intelligence
JUNE 14, 2022
It was very challenging, but I learned so much and it prepared me, as a CIO, to really understand what a cyber program should be and how we needed to mature moving forward,” she says. You have to make sure that you’re building in the security as you’re doing these transitions.”. Taking Mount Sinai to the cloud.

CIO Business Intelligence
JANUARY 5, 2023
Low-code/no-code visual programming tools promise to radically simplify and speed up application development by allowing business users to create new applications using drag and drop interfaces, reducing the workload on hard-to-find professional developers. It’s for speed to market,” says CTO Vikram Ramani.

CIO Business Intelligence
OCTOBER 4, 2023
Around two-thirds of the top 25 premiums were for security-related certifications, with GIAC Security Leadership (GSLC); GIAC Strategic Planning, Policy, and Leadership (GSTRT); Certificate of Cloud Security Knowledge (CCSK); Offensive Security Exploitation Expert (OSEE); and Offensive Security Defense Analyst (OSDA) attracting the biggest bonuses.

SecureWorld News
MAY 25, 2023
RELATED: Here's an article from The National CIO Review on "The Organizational Importance of the Chief Information Security Officer." They go through data analytics, a business application, digital applications, etc. Botts, Director, Global Cybersecurity Program, University of St.

CIO Business Intelligence
MAY 28, 2022
Foote does not report on any SAP certifications, but among the 579 certifications it does report on, architecture, project management, process and information security certifications remain the most valuable, commanding a pay premium of just over 8%. It is not always the newest technologies that pay the best.

CIO Business Intelligence
AUGUST 22, 2023
Product and delivery leaders: Agents of change While there are many ways to charter a program and define leadership responsibilities, I recommend leading transformation initiatives with these two key roles. Information security specialists guide agile teams on shift-left security practices.

GeekWire
DECEMBER 15, 2022
Protect AI , a Seattle startup that sells cybersecurity tech tailored to code that powers artificial intelligence and machine learning programs, emerged from stealth mode and announced $13.5 million in seed funding. “Machine learning code and tools are different.

CIO Business Intelligence
AUGUST 23, 2024
INE Security + Columbus State University Columbus State University (CSU) is a public university located in the southeastern United States, serving approximately 7,000 students annually. In 2019, CSU partnered with INE Security to integrate the Junior Penetration Tester (eJPT) certification into its curriculum.

CIO Business Intelligence
JUNE 22, 2022
As VMware has observed , “In simple terms, a DPU is a programable device with hardware acceleration as well as having an ARM CPU complex capable of processing data. Meeting the infrastructure needs of next-gen data-centric applications. Second, enterprise apps run across multiple geographically diverse cloud environments.

CIO Business Intelligence
FEBRUARY 24, 2023
By Zachary Malone, SE Academy Manager at Palo Alto Networks The term “shift left” is a reference to the Software Development Lifecycle (SDLC) that describes the phases of the process developers follow to create an application. Why is shift-left security important in cybersecurity? This creates risks.

SecureWorld News
SEPTEMBER 17, 2020
But the holes in the company's cybersecurity program are expensive. Now the company is being forced to take certain information security measures and pay a $650,000 fine to the state of New York. Dunkin's donut holes are delicious. Dunkin' Donuts cybersecurity lawsuit details.

CIO Business Intelligence
APRIL 13, 2023
Gartner projects that spending on information security and risk management products and services will grow 11.3% To better focus security spend, some chief information security officers (CISOs) are shifting their risk assessments from IT systems to the data, applications, and processes that keep the business going.

CIO Business Intelligence
AUGUST 5, 2022
And at its core is the need to secure customer data through a robust set of requirements. The regulations streamline how entities who handle customer banking information will secure their systems and share details within protected application program interfaces. Securing customer data.

CIO Business Intelligence
MAY 26, 2022
Foote does not report on any SAP certifications, but among the 579 certifications it does report on, architecture, project management, process and information security certifications remain the most valuable, commanding a pay premium of just over 8%. It is not always the newest technologies that pay the best.

SecureWorld News
MARCH 31, 2022
He is the Chief Information Security Officer at Veterans United Home Loans in Columbia, Missouri. He has more than 25 years of experience in both public entities and private industry, having built several Information Security programs from the ground up. In this installment, we introduce you to Randy Raw.
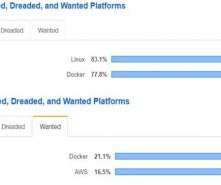
Hacker Earth
JANUARY 22, 2020
Here are some of the hottest tech skills (a mix of programming languages, tools, and frameworks; in random order) to hire for in 2020, which will help you thrive in the workplace of tomorrow. JavaScript has been the fastest-growing and the most sought-after programming language for years. Information security software developers.

SecureWorld News
JANUARY 4, 2024
A User Activity Monitoring (UAM) tool is a software solution designed to track and record the activities and interactions of users on computers or networks for security, compliance, or management purposes. This agent gathers data about the user's actions, such as keystrokes, mouse clicks, application usage, and internet activity.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content