The Architecture of Identity Systems
Phil Windley
SEPTEMBER 28, 2020
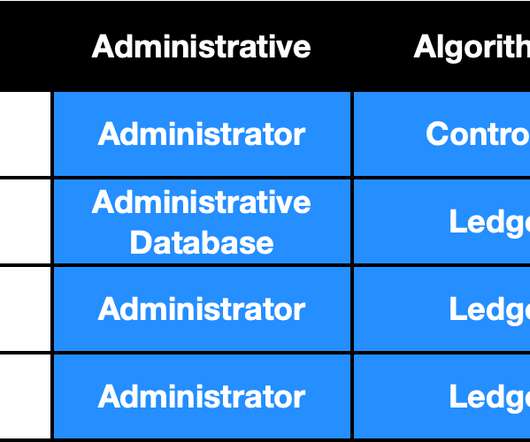
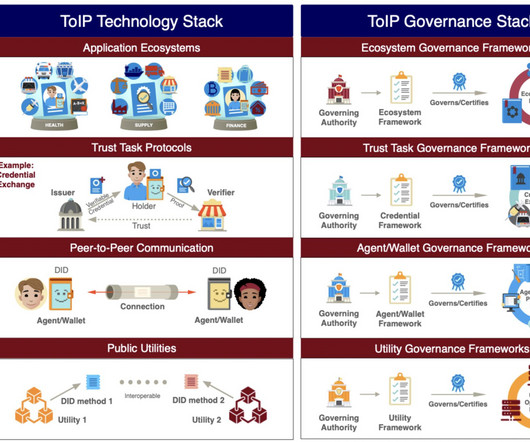
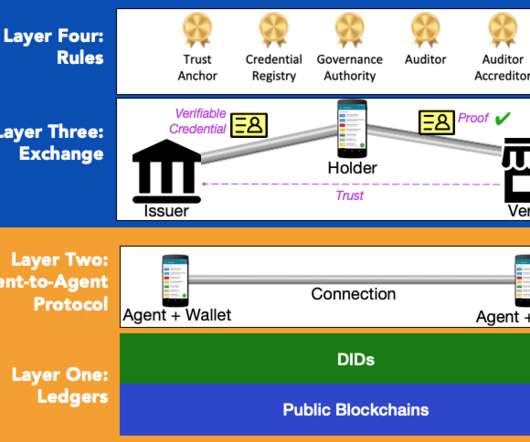
Summary: The architecture of an identity system has a profound impact on the nature of the relationships it supports. This blog post uses terminology and ideas from Sam's paper to classify and analyze three different identity system architectures. The controller might be the subject that the identifier refers to, but not necessarily.











































Let's personalize your content