Are Your Firewalls and VPNs the Weakest Link in Your Security Stack?
Network World
OCTOBER 21, 2024
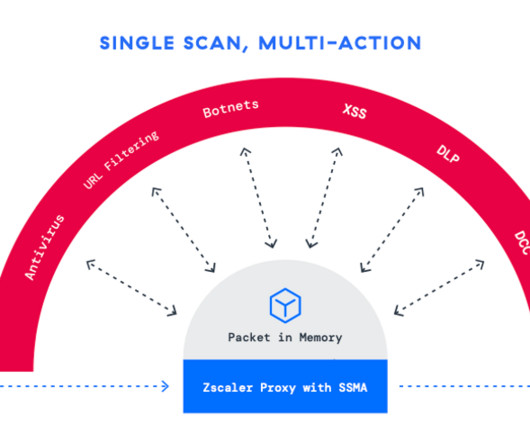
Zero Trust architecture was created to solve the limitations of legacy security architectures. It’s the opposite of a firewall and VPN architecture, where once on the corporate network everyone and everything is trusted. In today’s digital age, cybersecurity is no longer an option but a necessity.



















































Let's personalize your content