6 Best Authenticator Apps for 2024
Tech Republic Security
MARCH 26, 2024
Authenticator apps provide an extra layer of security. Learn about the best authenticator apps to secure your online accounts and protect your privacy.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
MARCH 26, 2024
Authenticator apps provide an extra layer of security. Learn about the best authenticator apps to secure your online accounts and protect your privacy.
Tech Republic Security
MARCH 5, 2024
Learn about passwordless authentication, and explore the different types, benefits and limitations to help you decide which solution to choose.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
MARCH 20, 2024
Explore top multi-factor authentication solutions for enhanced security and user authentication. Learn about the benefits and features of leading MFA providers.

Tech Republic Security
APRIL 2, 2024
Discover the top passwordless authentication solutions that can enhance security and user experience. Find the best solution for your business needs.

Tech Republic Security
JANUARY 25, 2024
Learn how to protect yourself and your sensitive information from phishing attacks by implementing multi-factor authentication.
Tech Republic Security
MARCH 14, 2024
The benefits of passwordless authentication include enhanced security, convenience, and boosted productivity. Learn how your organization can take advantage.

Information Week
JUNE 28, 2024
Ticketmaster, Santander Bank, and other large firms have suffered data leaks from a large cloud-based service, underscoring that companies need to pay attention to authentication.

Network World
OCTOBER 11, 2024
In the first half of this year, 38% of organizations had at least one cloud workload that was critically vulnerable, highly privileged, and publicly exposed, according to a study of telemetry from customers of cloud security vendor Tenable released this week. The cloud is a tool like any other; how you use it is what matters,” he said.

Tech Republic Security
NOVEMBER 9, 2022
Strategic Business Initiatives – Does the solution support cloud, mobile and BYOD initiatives? The post Two-Factor Authentication Evaluation Guide appeared first on TechRepublic. Can it fulfill compliance? Total Cost of Ownership (TCO) – Does the solution.

Network World
OCTOBER 1, 2018
billion deal it made for network identity, authentication security company Duo. Duo’s cloud-delivered technology lets IT professionals set and enforce risk-based, adaptive access policies and get enhanced visibility into users’ devices and activities. Cisco said today it had closed the $2.35

Tech Republic Security
MARCH 24, 2022
The post How to add an authenticated DockerHub registry to Portainer appeared first on TechRepublic. Portainer is a great way to help make Docker container development much more efficient. If your company has an official DockerHub registry, you should connect the two. Jack Wallen shows you how.

Network World
JANUARY 21, 2025
Integrating traffic management, policy enforcement, and role-based access control, Red Hat Connectivity Link is a new technology from IBMs Red Hat business unit thats aimed at simplifying how enterprises manage application connectivity across distributed cloud environments. Red Hat Connectivity Link is not a mesh, Ferreira emphasized.

Network World
MARCH 11, 2019
Some elements remain in an on-premise data center, while other portions have gone to the cloud and even to multi-cloud. Many companies today have a hybrid approach to their networking and IT infrastructure. As a result, the network perimeter is permeable and elastic. To read this article in full, please click here

Network World
AUGUST 29, 2024
Simplicity is a superpower that’s strong,” said Chris Wolf, global head of AI and advanced services, VMware Cloud Foundation division of Broadcom. One bright shiny object that VMware pursued a decade ago, he said, was the public cloud. You’re confronting the three Cs of public cloud. Complexity: It is another platform.

Tech Republic Security
JULY 11, 2024
Exploiting the BlastRADIUS vulnerability leverages a man-in-the-middle attack on the RADIUS authentication process.

CIO Business Intelligence
AUGUST 17, 2022
In my last column for CIO.com , I outlined some of the cybersecurity issues around user authentication for verification of consumer and business accounts. . FIDO as an industry initiative was set up a decade ago to standardize the need for strong authentication/password technologies. Well, yes, but there is more that tech pros can do.

IT Toolbox
DECEMBER 4, 2023
Authentication allows the verification of user identity, ensuring only authorized access to systems, services, and resources. The post What Is Authentication? Meaning, Types, and Tools appeared first on Spiceworks.

Network World
APRIL 15, 2020
Cisco has posted a package of 17 critical security warnings about authentication vulnerabilities in its Unified Computing System that could let attackers break into systems or cause denial of service troubles.

Information Week
JULY 10, 2024
Cloud firm answers customers' calls to strengthen its multifactor authentication policies, in the wake of over 100 breaches that exploited unprotected Snowflake accounts.
CIO Business Intelligence
MAY 24, 2022
They may have a built-in user store supporting password authentication, for example. Others are related to cloud-specific systems, like Azure AD B2C. In response to cloud-based customer experiences, more focus has shifted to authentication. 5 Essential modern customer authentication elements that FIDO enables.

CIO Business Intelligence
AUGUST 21, 2024
The days when most companies completely shied away from using cloud resources for highly sensitive data or applications have passed, and for good reason. Today, cloud providers may offer better cybersecurity protections than many companies can provide on-premises. But you need to know what to look for in a cloud provider.

Network World
MARCH 31, 2021
Cisco made enhancements to its security offerings that will expand and change the way customers buy its Secure Access Service Edge products as well as bolster network-access authentication.

Tech Republic Security
MARCH 15, 2024
Learn the key differences between multi-factor authentication (MFA) and two-factor authentication (2FA) and find out which one is best for your business needs.

Network World
MAY 18, 2022
The increased deployment of core business applications in the cloud and the shift to remote work brought on by the pandemic have obliterated any notion of the traditional “corporate moat” style of security. Zero Trust Network Access (ZTNA) has emerged as the preferred approach to address today’s security challenges.

CIO Business Intelligence
MARCH 9, 2022
Today’s cloud strategies revolve around two distinct poles: the “lift and shift” approach, in which applications and associated data are moved to the cloud without being redesigned; and the “cloud-first” approach, in which applications are developed or redesigned specifically for the cloud.

Network World
OCTOBER 23, 2024
Its “backbone as a service” gives customers the ability to connect branch locations, cloud workloads and applications through Alkira’s fabric. The basic concept behind ZTNA overall is to make sure that all access is authenticated and that there is no implied trust, just because a user has access to a network.

CIO Business Intelligence
JANUARY 31, 2023
Here, I’ll share a few tips to help you uncover your authentic leadership style. If you can answer these questions, you’ll be on your way to uncovering your authentic style. And it creates a positive feedback loop, where your honesty helps others feel safe being their authentic selves, too. What are your values?

CIO Business Intelligence
OCTOBER 26, 2022
A massive shift to cloud and API-based ways of working has made the sector become more agile and innovative, but it has also opened the floodgates for identity theft. Have you thought about what can be done with this device to enhance identity authentication? Avaya’s research report reveals three critical ways to do so.

CTOvision
JUNE 24, 2020
Read Raj Mallempati explain the cloud permissions management on Dark Reading : By using the AAA permissions management framework for cloud operations, organizations can address authentication, authorization, and auditing. As […].

Network World
FEBRUARY 14, 2025
Admins with firewalls from Palo Alto Networks should make sure the devices are fully patched and the management interface blocked from open internet access after the discovery this week of a zero-day login authentication bypass in the PAN-OS operating system. The issue doesnt affect the companys Cloud NGFW or Prisma Access software.
Tech Republic Security
MARCH 25, 2022
The post How to add an authenticated DockerHub registry to Portainer appeared first on TechRepublic. Portainer is a great way to help make Docker container development much more efficient. If your company has an official DockerHub registry, you should connect the two. Jack Wallen shows you how.

Tech Republic Security
FEBRUARY 5, 2025
Fingerprint sign-in on Windows 11 offers a secure, password-free login method. Set it up easily for faster, more convenient access to your device.

Tech Republic Security
MAY 18, 2023
The single sign-on market leader’s Security Center, now generally available, uses Okta Customer Identity Cloud for insights into authentication activity for insights into anomalies, threats and security friction.
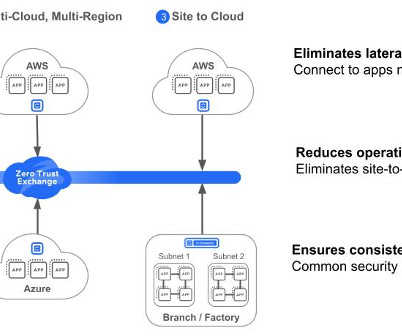
CIO Business Intelligence
NOVEMBER 8, 2023
Today, many organizations are embracing the power of the public cloud by shifting their workloads to them. A recent study shows that 98% of IT leaders 1 have adopted a public cloud infrastructure. It is estimated by the end of 2023, 31% of organizations expect to run 75% of their workloads 2 in the cloud. 8 Complexity.

Network World
JANUARY 16, 2025
Nile Navs integration with the Nile Services Cloud AI-enabled Cognitive Decisions module actively monitors deployments against the sites Digital Twin and predefined plans, Kannan stated. The security features include built-in access control for basic authentication, single sign-on (SSO), and multi-factor authentication (MFA).

Network World
OCTOBER 21, 2024
The traditional reliance on firewalls and VPNs for cybersecurity is proving inadequate in the face of mounting cyberthreats and changes to network designs due to the cloud. For those striving to fit existing infrastructure into a modern cloud-first stance, adopting a Zero Trust framework is crucial.

CIO Business Intelligence
MAY 3, 2022
The dramatic shift to cloud services over the past few years has given organizations unprecedented flexibility and scalability, enabling them to forge ahead with digital transformation efforts. For many, it has also led to intermingled, complex strategies that threaten to take away some of the luster of the cloud. Controlling costs.
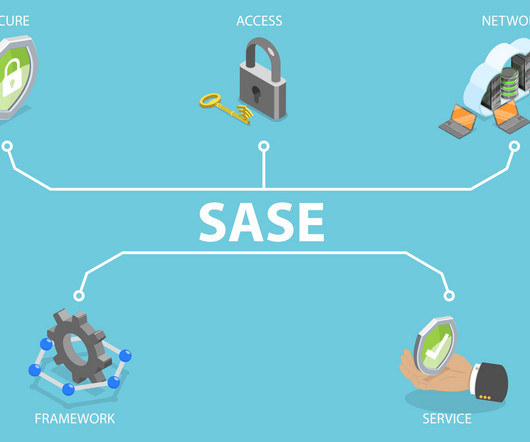
Network World
FEBRUARY 13, 2025
Secure Access Service Edge (SASE) is a network architecture that combines software-defined wide area networking (SD-WAN ) and security functionality into a unified cloud service that promises simplified WAN deployments, improved efficiency and security, and application-specific bandwidth policies. billion by 2025. What is SASE?

Network World
APRIL 24, 2023
The service can also onboard new devices, authenticate existing users, segment devices on the network, or help troubleshoot problems from a cloud-based system, according to Pramod Badjate, group vice president and general manager, of Arista’s Cognitive Campus group. To read this article in full, please click here

CIO Business Intelligence
MAY 30, 2024
Enterprises and SMEs, all share a common objective for their cloud infra – reduced operational workloads and achieve greater scalability. Likewise, a social media platform could have separate functions to handle user authentication, content moderation, and push notifications. optimize the overall performance.

Network World
APRIL 7, 2022
Virtualization and cloud vendor VMware this week disclosed eight vulnerabilities in five of its products , and urged users of Workspace ONE Access and all its products that include VMware Identity Manager components to patch immediately. To read this article in full, please click here

Network World
MARCH 8, 2021
WAN challenges steer Sixt to cloud-native SASE deployment (Network World). SASE, pronounced "sassy," blends SD-WAN's network optimization features with security capabilities such as zero-trust authentication, data loss prevention, threat detection, and encryption. WFH security lessons learned from the pandemic (Computerworld).

Network World
OCTOBER 28, 2024
Extreme Networks is bolstering the access control features of its ExtremeCloud Universal Zero Trust Network Access ( ZTNA ) package, targeting customers that want to boost protection across distributed cloud environments. It ties together network, application and device access security from a single cloud-based dashboard.

CIO Business Intelligence
JUNE 3, 2024
AI-generated code promises to reshape cloud-native application development practices, offering unparalleled efficiency gains and fostering innovation at unprecedented levels. This dichotomy underscores the need for a nuanced understanding between AI-developed code and security within the cloud-native ecosystem.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content