How to defend your organization against social engineering attacks
Tech Republic Security
NOVEMBER 5, 2020
A security awareness program backed by multi-factor authentication can help protect your critical assets, says NordVPN Teams.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
NOVEMBER 5, 2020
A security awareness program backed by multi-factor authentication can help protect your critical assets, says NordVPN Teams.

CIO Business Intelligence
DECEMBER 18, 2024
And if they werent, multi-factor authentication (MFA), answers to security questions, and verbal passwords would solve the issue. Navigating IVR According to an analysis of call center deepfake attacks, a primary method favored by fraudsters is using voice deepfakes to successfully move through IVR-based authentication.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CIO Business Intelligence
OCTOBER 31, 2024
The attacks, in which criminals frequently leverage social engineering to impersonate company insiders, C-suite executives or trusted vendors to request urgent payments, can financially devastate organizations. It can be easy to fall victim to a BEC attack, especially for companies with limited resources and leaner teams handling payments.

Network World
OCTOBER 21, 2024
We will also navigate the ever-evolving landscape of cybersecurity and discover how to protect your organization from the ever-growing arsenal of cyber threats. This philosophy demands rigorous and continuous authentication and authorization procedures before granting access to any resources or systems.

CIO Business Intelligence
MAY 5, 2022
However, cybercriminals commonly take the path of least resistance, and organizations’ reliance on password-based authentication provides numerous avenues of attack. Passwords are known to be a weak form of authentication, and the widespread use of weak and reused passwords puts companies and their customers at risk.

CIO Business Intelligence
MARCH 4, 2025
Liminal Panda in particular has demonstrated extensive knowledge of telecom networks and how to exploit interconnections between providers to move and initiate intrusions across various regions.

CIO Business Intelligence
MARCH 4, 2025
Liminal Panda in particular has demonstrated extensive knowledge of telecom networks and how to exploit interconnections between providers to move and initiate intrusions across various regions.

CIO Business Intelligence
MAY 24, 2024
Cybersecurity has been promoted from the purview of the chief security officer (CSO) to a boardroom environmental, social, and corporate governance (ESG) responsibility. HP Anyware is a secured access enterprise software product offering zero trust user authentication and endpoint device management strategies.

CIO Business Intelligence
MAY 2, 2022
Password-based authentication is likely the most widely used method of authenticating users to online services. Password-based authentication is used because it is easy to understand and implement. They provide multifactor authentication (MFA) without the usual burden on the user. on a user’s other online accounts.

CIO Business Intelligence
AUGUST 29, 2024
When you add multi-factor authentication (MFA) resets to the picture, that number is likely even higher. Most authentication methods are actually quite easy to get around, and in many cases were never intended to be security factors. But what happens when a user can’t access their authenticator app?

CIO Business Intelligence
OCTOBER 16, 2023
But casino gaming companies MGM Resorts International and Caesars Entertainment were caught short in this area in recent weeks by hackers using identity-based and social engineering attacks that spoofed identity to gain access to secure systems. According to reports, MGM and Caesars were both customers of identity management company Okta.

Network World
JANUARY 30, 2025
simple AI assistants are supplemented by AI agents with more advanced capabilities, employees will need to manage entire teams of agents that are completing tasks autonomouslyand learn how to work with chat-based supervisory AI agents that can help streamline this process. This third wave of AI promises to transform workflows wholesale.7

CIO Business Intelligence
JUNE 18, 2022
This quaint excess of modesty about your career accomplishments might seem like an endearing trait—a refreshing lack of vanity in a world awash in social media noise. based), this Microsoft-owned social network dominates the business landscape. “No How do I find a good resume writer? “I’m really not into self-promotion.”.

CIO Business Intelligence
JANUARY 23, 2025
A large majority of autistic people, around 85%, report they enjoy the work they do, however only 44% say they feel they can be their authentic selves at work. Office environments can have many unspoken rules and nuanced social conventions that arent directly expressed, especially to new workers.

Dataconomy
JANUARY 26, 2025
Social media benchmarks show it solving LeetCode problems 12% faster than OpenAIs o1 model while using just 30% of the system resources. How to integrate DeepSeek-R1 into your projects DeepSeek-R1 can be integrated locally or via its cloud API: 1. Why DeepSeek-R1 is trending? All data remains on your machine, ensuring privacy.

GeekWire
MARCH 25, 2025
This past weekend, I attended the ATmosphere Conference in Seattle, the first conference about the Authenticated Transfer (AT) Protocol. You likely haven’t heard about it and what it does, but you’ve certainly heard of the social network built using this protocol: Bluesky. players that you came to love and hate.

SecureWorld News
FEBRUARY 10, 2025
The attackers place themselves between the user and the legitimate website, intercepting session data and bypassing multi-factor authentication (MFA) by relaying the authentication process in real time. Multi-factor authentication (MFA) is also a must to prevent unauthorized access from just a stolen password.

CIO Business Intelligence
NOVEMBER 1, 2024
One of the world’s largest risk advisors and insurance brokers launched a digital transformation five years ago to better enable its clients to navigate the political, social, and economic waves rising in the digital information age.
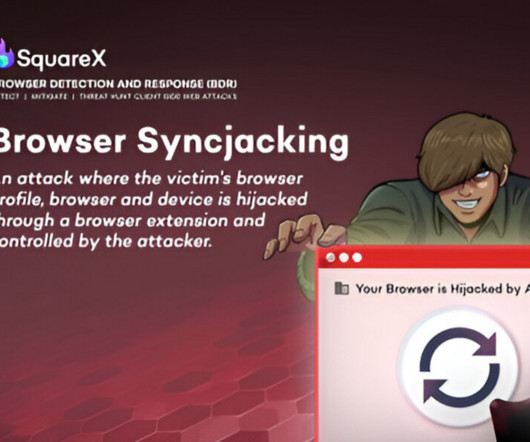
CIO Business Intelligence
JANUARY 30, 2025
The extension then silently authenticates the victim into a Chrome profile managed by the attackers Google Workspace. Once this authentication occurs, the attacker has full control over the newly managed profile in the victims browser, allowing them to push automated policies such as disabling safe browsing and other security features.

Dataconomy
JANUARY 16, 2025
With social media platforms dominating the way consumers discover products and services, influencers bridge the gap between brands and their target audiences. Their ability to connect authentically with followers makes them a powerful tool for increasing brand visibility and driving engagement. What is influencer marketing?

SecureWorld News
AUGUST 22, 2022
Social media is allowing companies to show their creativity and personality to customers and the world like never before. Today, businesses have the ability to reach millions of people through social media—regularly and as creatively as they dare. How does AI boost social media? A staggering 4.62
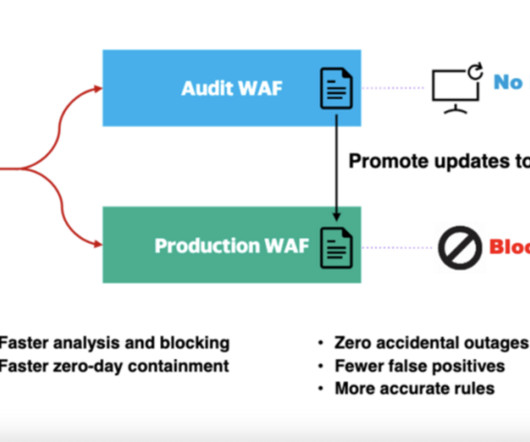
CIO Business Intelligence
JULY 17, 2023
This can occur through techniques like phishing, social engineering, or exploiting vulnerabilities in authentication mechanisms. Account Hijacking: Cloud exploitation can involve the compromise of user accounts, allowing attackers to gain control over cloud resources.

CIO Business Intelligence
MAY 17, 2022
Knowing this, cybercriminals focus on exploiting weak authentication methods as part of their attacks. Additionally, when implemented correctly, Customer Identity and Access Management (CIAM) passwordless solutions enable companies to build multi-factor authentication into their digital experiences.

CIO Business Intelligence
NOVEMBER 1, 2024
One of the world’s largest risk advisors and insurance brokers launched a digital transformation five years ago to better enable its clients to navigate the political, social, and economic waves rising in the digital information age.

CIO Business Intelligence
OCTOBER 25, 2023
Identity attacks use social engineering, prompt-bombing, bribing employees for 2FA codes, and session hijacking (among many techniques) to get privileged access. Train users on the importance of strong passwords, how to recognize phishing attempts, and how to properly use MFA methods.

CIO Business Intelligence
MAY 31, 2022
The metaverse will require a digital foundation that enables trust and authenticity. Currently, society is at an inflection point as people have lower confidence in the internet and in social media. Here are five implications these technologies will have on security and privacy as we build our collective future. . Building trust.

GeekWire
FEBRUARY 25, 2022
As disinformation and Russian propaganda flood social media during the invasion of Ukraine, information experts are providing advice about how avoid propagating false narratives. Russia has likely already “infiltrated some of our trusted social networks,” said Starbird. GeekWire Photo | Charlotte Schubert). Correct mistakes.

CIO Business Intelligence
FEBRUARY 26, 2024
This includes displays of empathy, authenticity, and concerted efforts to build human connection, either in-person or virtually. Some regions could differ in their approach to data sovereignty and IP protection, so organizations may weigh privacy concerns when determining where and how to store sensitive information.

Vox
AUGUST 22, 2024
My Social Security number had been compromised in an alleged data breach. As many as 272 million Social Security numbers are floating around hacker forums after someone stole them from a Florida-based background check company called National Public Data , which is owned by an actor and retired sheriff’s deputy named Salvatore “Sal” Verini.

CIO Business Intelligence
SEPTEMBER 21, 2023
Recent cyberattacks at MGM Resorts and Caesars Entertainment have put the spotlight on cybersecurity practices at casinos – and the importance of educating employees on social engineering tactics. As learned from recent cyberattacks, user education has become a critical component to protecting against these threats as well.

CIO Business Intelligence
JUNE 9, 2022
In recent months, you may have noticed an uptick in two-factor and multi-factor authentication prompts, which are being used to verify consumer and business accounts. In the T-Mobile case, Lapsus$ members hacked into T-Mobile’s network in March 2022 by compromising employee accounts, either via phishing or another form of social engineering.

CIO Business Intelligence
AUGUST 22, 2022
As the industry continues the shift from in-person services toward remote customer service and hybrid models, banks are focusing more than ever on how to support their customer’s experiences in a way that quickly answers inquiries and gives customers a more frictionless experience for loan applications and other financial services. .

Phil Windley
AUGUST 12, 2020
Our online relationships with ecommerce companies, social media providers, banks, and others are cold and impersonal, but also relatively efficient. For example, social media platforms are designed to allow people to form a link (symmetrical or asymmetrical) to others online. Supporting Authentic Relationships.

CTOvision
OCTOBER 28, 2015
The abundance of free email, social media and other electronic communication services, combined with their inability to accurately attribute these accounts to identifiable individuals, provides a veil of anonymity for those seeking to remain undetected or unidentified. Additionally, insiders now have new ways of coordinating with others.

CIO Business Intelligence
JUNE 25, 2024
and you’ll discover that the exploited vulnerability was a bush-league error — failing to institute multifactor authentication on exposed servers. You’ll also read that UHG paid a ransom as part of how it handled the problem. Mission: how the plan will deliver the social value that is the business’s reason for being.

SecureWorld News
AUGUST 2, 2021
Here is how the company describes the threat of phishing emails: "Phishing is a common way scammers try to trick you into giving them personal information such as an account username and password, Social Security number, or other personal information. How to spot phishing emails.

CIO Business Intelligence
FEBRUARY 7, 2023
Cybsafe Some organizations are tailoring their social policies to be more inclusive, such as at security awareness training firm Cybsafe. Yet if considering and including Black women in social gatherings is one issue, a bigger obstacle lies in conscious and unconscious bias. We need strong allies, but it has to be authentic.

The Verge
JUNE 4, 2020
So, for example, if you use Twitter or Instagram at a protest, that activity and your social media account gets tied to the protest. This is a safer way to post to social media or take photos during a protest, and it’s helpful in the event that you need to show someone, including law enforcement, something on your phone.

Network World
OCTOBER 31, 2016
Most users know the basics of computer privacy and safety when using the internet, including running HTTPS and two-factor authentication whenever possible, and checking haveibeenpwned.com to verify whether their email addresses or user names and passwords have been compromised by a known attack.
GeekWire
FEBRUARY 26, 2021
is co-founder of The Chances App , a new social relationships app he’s spent a year creating with daughters Vanessa Lipschutz, 23, a Seattle University grad, and Noelle Lipschutz, 19, a student at UCLA. Chances is a social relationships app created for and by Gen Z. Have you seen “The Social Dilemma” )?

SecureWorld News
MARCH 13, 2025
Threat actors are learning how to use these tools, and as AI models improve, so will their ability to assist in writing complex and evasive malware," the report warns. Hardening endpoints to increase the cost of attack Trey Ford, Chief Information Security Officer at Bugcrowd, takes a pragmatic approach to AI-driven cyber threats.

SecureWorld News
AUGUST 5, 2023
Multi-factor authentication (MFA) is a fundamental component of best practices for account security. Traditionally, this approach to authentication delivers a unique code to a user's email or phone, which is then inputted following the account password. SMS-based MFA MFA via SMS (i.e., However, MFA via SMS is not without its issues.

CIO Business Intelligence
JULY 27, 2023
Schwarz recommends taking the time to do three things: Know the value of your company’s currency, invest heavily in peer relationships, and above all, be authentic to your personal brand. Not sure how to get on one? Make sure your brand is authentic to how you operate,” says Schwarz. They have to build an ecosystem.

Network World
NOVEMBER 22, 2016
RELATED: How to dodge Black Friday schemes + Here are a dozen steps you can take to avoid becoming a victim. Avoid using simple passwords, and use two-factor authentication if you can. Be suspicious of great deals you learn about via social media or emails and don’t click the links. Don’t use free pubic Wi-Fi to make purchases.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content