How to defend your organization against social engineering attacks
Tech Republic Security
NOVEMBER 5, 2020
A security awareness program backed by multi-factor authentication can help protect your critical assets, says NordVPN Teams.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
NOVEMBER 5, 2020
A security awareness program backed by multi-factor authentication can help protect your critical assets, says NordVPN Teams.

CIO Business Intelligence
MARCH 4, 2025
Simply relying on multi-factor authentication is not enough to prevent complex breaches that rely on social engineering and impersonation to exploit existing relationships.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CIO Business Intelligence
JANUARY 23, 2025
A large majority of autistic people, around 85%, report they enjoy the work they do, however only 44% say they feel they can be their authentic selves at work. The programs through ATI are customized to the companies they partner with, offering free technical training that aligns with the organizations skills needs.

CIO Business Intelligence
NOVEMBER 21, 2024
The identified scenarios where AI is used include judicial, news, medical, biometric recognition, autonomous driving, social credit, social bots and where AI is used by state organizations. As well, the principles address the need for accountability, authentication, and international standards. Contact us today to learn more.

CIO Business Intelligence
MARCH 4, 2025
Simply relying on multi-factor authentication is not enough to prevent complex breaches that rely on social engineering and impersonation to exploit existing relationships.

CIO Business Intelligence
APRIL 19, 2022
“It seemed too good to be true — free classes for six months, a paid internship, partnerships with great companies in my area, high graduation and employment rates, and lastly, an emphasis on social justice,” says Burrows, who now works as a software engineer at RealSelf. Mariya Burrows, software engineer, RealSelf. Mariya Burrows.

CIO Business Intelligence
OCTOBER 16, 2023
But casino gaming companies MGM Resorts International and Caesars Entertainment were caught short in this area in recent weeks by hackers using identity-based and social engineering attacks that spoofed identity to gain access to secure systems. It sounds simple, but it could be a hedge against similar social engineering and phishing hacks.

CTOvision
JUNE 28, 2016
Social engineering is one of the most problematic attack techniques to combat. User education is most effective at stopping a social engineer. Users who are aware of the potential for social engineering attacks and learn to recognize them can use simple methods to thwart these attacks successfully. Stu Sjouwerman.

Trends in the Living Networks
AUGUST 2, 2011
Defense Advanced Research Projects Agency (DARPA) (slogan: Creating and Preventing Strategic Surprise) is offering $42 million in funding for “revolutionary&# research into social media in strategic communication. Recognize persuasion campaign structures and influence operations across social media sites and communities.

CIO Business Intelligence
OCTOBER 20, 2022
In fact, CIO has reported that it takes only a few minutes for experienced hackers to set up a social engineering attack against enterprises (and their managed service providers) that consider themselves to be secure and protected. Deploy email authentication standards on enterprise email servers to check and verify inbound emails.

SecureWorld News
JANUARY 22, 2025
Additionally, these conventional tools lack the contextual awareness needed to identify sophisticated social engineering tactics employed by AI-powered phishing campaigns. Multi-factor authentication (MFA) : Enforce robust MFA protocols to add an extra layer of security.

CIO Business Intelligence
OCTOBER 4, 2023
Sandboxing is a highly respected security method that creates a confined execution environment where you can run programs with low rights or privileges. Many documents include personally identifying information, such as Social Security Numbers (SSNs), birthdates, and home addresses. Provide access control.

CIO Business Intelligence
MAY 31, 2022
The metaverse will require a digital foundation that enables trust and authenticity. Currently, society is at an inflection point as people have lower confidence in the internet and in social media. There are endless avenues to enable new ways to augment, customize, and otherwise “program” our physical environments.

CIO Business Intelligence
JUNE 18, 2024
So, what’s the difference between the two, why does it matter, and how can a strong identity program help achieve both? Verification and access control Effective identity management begins with a verification process to establish the authenticity of users and entities accessing critical systems and data. In other words, insiders.

CIO Business Intelligence
SEPTEMBER 29, 2023
Using the “same old” low-skill tactics, common tools, and a bit of social engineering, hackers can get around complex security policies such as multi-factor authentication (MFA) and identity and access management (IAM) systems. Let’s revisit the most prevalent security threats and see how they’re evolving in 2023.

CIO Business Intelligence
JANUARY 22, 2025
With the power of social media and the internet, connecting with people virtually anywhere in the world is possible. Ive found incredible value in hearing someone authentically share their experiences from all levels. If your mentor is accessible to you in the form of informal coffee catchups, consider yourself lucky.

CIO Business Intelligence
MAY 16, 2023
When employees feel they can bring their authentic selves to work, it can result in higher levels of employee productivity and satisfaction, improved retention rates, and more effective recruiting efforts. BCBSNC’s Ladder program addresses this issue by fostering leadership relationships for BIPOC IT workers. Diggs says.

Galido
JUNE 1, 2017
Now, in the era of the Internet, it’s hard to imagine a person who does not use at least one of the social networks. Social networks are used by everyone – both young and old. In order to protect yourself as much as possible from the risks that social networks carry, it is necessary to follow a number of simple rules.

SecureWorld News
AUGUST 22, 2022
Social media is allowing companies to show their creativity and personality to customers and the world like never before. Today, businesses have the ability to reach millions of people through social media—regularly and as creatively as they dare. How does AI boost social media? A staggering 4.62

SecureWorld News
MARCH 13, 2025
Key findings from Tenable's report Tenable's research team investigated DeepSeek R1's ability to generate malicious code, specifically a keylogger and a simple ransomware program. While the AI-generated malware required manual debugging to function properly, its mere existence signals an urgent need for security teams to adapt their defenses.

Vox
FEBRUARY 21, 2023
Friso Gentsch/picture alliance via Getty Images You used to pay for social media with your eyeballs. If you’re not paying for the product, you are the product” has long been a common refrain about the business of social media. But now, this free model of social media — subsidized by advertising — is under pressure.
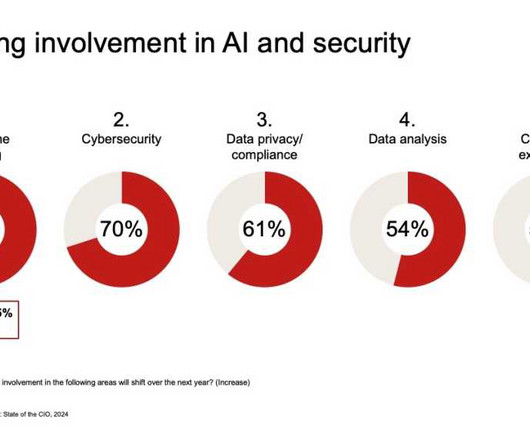
CIO Business Intelligence
MAY 20, 2024
He has set up an AI program centered around identifying business use cases where intelligence could have an impact, such as solving a problem or streamlining a process. Those projects include implementing cloud-based security, anti-ransomware, and user behavior analytics tools, as well as various authentication technologies.

CIO Business Intelligence
FEBRUARY 9, 2023
Unfair and hostile work environments A study from The Kapor Center for Social Impact and The Ford Foundation found unfair treatment to be the top driver of employee turnover, in particular for employees from underrepresented groups. Evaluate your sponsorship programs to make sure they work for everyone.

CIO Business Intelligence
JANUARY 13, 2023
And the murder of George Floyd — and the social unrest that followed — made it clear that taking a stand around social justice is necessary to recruitment, retention, and even the viability of your brand. That is all part of being authentic.” We have an entire system when folks decide to leave,” says Maurer. “So,

CIO Business Intelligence
FEBRUARY 27, 2023
Whether it’s workplace issues, social justice issues, or talking about engineering, and help each other along with our careers,” says Greenlee. In another example, Greenlee’s family member attended a programming course in high school but was immediately discouraged after being made to feel uncomfortable in an all-white classroom. “He

Network World
OCTOBER 31, 2016
Most users know the basics of computer privacy and safety when using the internet, including running HTTPS and two-factor authentication whenever possible, and checking haveibeenpwned.com to verify whether their email addresses or user names and passwords have been compromised by a known attack.

Network World
AUGUST 21, 2024
As of this April, 320 hospitals were approved to participate in the program , treating over 11,000 patients. In addition, there are daily video visits with physicians, continual monitoring of vital signs, and coordination with testing, therapy, social work, and meal services providers, and 24-hour access to a virtual care team.

CTOvision
JUNE 12, 2014
However, those solutions require fingerprint readers, better encryption, key management programs, and card provisioning systems, which also translates to more people needed to manage the security infrastructure. Their two-factor authentication solution consists of a unique device ID and the big data pattern associated with it.

SecureWorld News
DECEMBER 30, 2024
ISO 22398: Covers the principles of planning, conducting, and developing training programs to prepare teams for critical situations through practical exercises and simulations. Collect and safeguard critical artifacts such as event logs, system logs, and authentication records from corporate systems.

SecureWorld News
DECEMBER 19, 2024
The main reason why phishing is so feared and effective is that it targets the weakest link in any cybersecurity program: employees. For this reason, phishing awareness and education programs have become a crucial element in any robust cybersecurity strategy.

CIO Business Intelligence
MAY 30, 2023
Projects also include the introduction of multifactor authentication; security, orchestration, automation, and response (SOAR); extended detection and response (XTR); and security information and event management (SIEM) software, according to Uzupis, who left his position in spring 2023. It doesn’t end the moment you land on the cloud.”

GeekWire
APRIL 6, 2021
“We also believe there is a level of authenticity to Clubhouse which will lead to a new learned experience for our cohort to solidify their narrative.” The accelerator will run for four weeks, with programming designed to support the startup founders toward presenting on Investor Demo Day on May 1.

Trends in the Living Networks
NOVEMBER 23, 2008
I'm at Online Social Networking & Business Collaboration World , where I'm chairing the plenary sessions and enterprise streams. The book on social networking has not been written yet. Social networking brings together many spheres of competition. The volume of photos shared on the Internet on social networks is phenomenal.

SecureWorld News
FEBRUARY 27, 2025
Bybit's bounty program and industry response In response to the attack, Bybit launched a bounty program to recover the stolen funds and identify those responsible. These funds are believed to play a crucial role in financing North Korea's missile and nuclear weapons programs, circumventing international sanctions.

GeekWire
MAY 25, 2021
Empower employees: Remitly last year provided training and resources to help employees learn how to civically engage with elected officials, attend city hall meetings, share petitions on social media and participate more actively in the public process.

Cloud Musings
DECEMBER 14, 2014
The majority of these attacks are due to hacking, fraud and social engineering. via email) and attaches itself into files and other programs Downloader Software that downloads executable malicious code without the users knowledge or consent Figure 1. For example, in the first half of 2014, 84.6% Most Active Malware Today.

The Verge
MARCH 10, 2021
But far more exciting and intimate ways to shoot ice skating have been emerging on social media, and one person in particular has made a name synonymous with turning the sport into something spectacular to watch: Jordan Cowan, under the name On Ice Perspectives. It can be dull to watch. This conversation has been lightly edited for clarity.
SecureWorld News
MAY 26, 2022
Twitter, like many other social media websites, asks users to provide their phone number and email address to better protect their account. This action violated a 2011 FTC order that prohibited the social media site from misrepresenting its privacy and security practices. Twitter sells 2FA information to advertisers.

GeekWire
NOVEMBER 8, 2021
” Techstars Seattle is running a hybrid-style program for this cohort — founders can work from wherever they are most productive, whether that’s at Startup Hall in Seattle or their home city. We make it easy to collect and store data, set priorities, and take actions around ESG (environmental, social, and governance) goals.
GeekWire
AUGUST 11, 2020
“The EVRGRN Channel, as a result, reflects the authentic PNW persona: resilient, independent, artistic, and adventurous.” “STIRR also provides local, live news programming, which pairs well with our regionally curated catalog.” More people are streaming media due to the pandemic and social distancing mandates.

CTOvision
OCTOBER 28, 2015
The abundance of free email, social media and other electronic communication services, combined with their inability to accurately attribute these accounts to identifiable individuals, provides a veil of anonymity for those seeking to remain undetected or unidentified. Additionally, insiders now have new ways of coordinating with others.

The Accidental Successful CIO
SEPTEMBER 22, 2021
Synchrony Financial uses AI-enabled applications to speed up credit-card authentication, identify and prevent fraud, power virtual agents and personalize marketing offers. AI is a competitive advantage for them. Customers can also request to have personal data deleted.

GeekWire
DECEMBER 18, 2020
Seattle-based FFA just wrapped up a virtual version of its eight-week Ready Set Raise program, which requires each company to have a female or non-binary CEO. The organization doesn’t take equity from companies participating in the accelerator program. Fix Fake solves this problem by halving the authentication costs.

GeekWire
JANUARY 24, 2025
Biometric authentication.) Although I believe that eventually there will be programs that will recreate some elements of human intelligence, I dont think its likely to happen in my lifetime, he wrote. Bonus: Cruise and Top Gun are still around.) commercial real estate.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content