How to Balance Disaster Recovery, Backup Systems, and Security
Information Week
APRIL 22, 2024
Dale Zabriskie, field CISO with Cohesity, and Kim Larsen, CISO with Keepit, discuss ways disaster recovery can work more closely with security.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Information Week
APRIL 22, 2024
Dale Zabriskie, field CISO with Cohesity, and Kim Larsen, CISO with Keepit, discuss ways disaster recovery can work more closely with security.

Tech Republic Security
APRIL 12, 2024
Research has found that criminals can demand higher ransom when they compromise an organisation’s backup data in a ransomware attack. Discover advice from security experts on how to properly protect your backup.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CIO Business Intelligence
FEBRUARY 12, 2025
To bridge this critical gap, IT leaders should focus on the five Ss speed, security, scale, simplicity, and smarts to strengthen their cybersecurity and response capabilities. To address these challenges, organizations need to implement a unified data security and management system that delivers consistent backup and recovery performance.

Network World
JULY 27, 2020
Businesses considering the secure access service edge (SASE) model need to understand that there are numerous ways to implement it that can be tailored to their future needs and the realities of their legacy networks. To read this article in full, please click here

IT Toolbox
SEPTEMBER 15, 2022
Data backup may seem basic, yet businesses have experienced a loss of data as a result of not backing up or a failed backup. In this article, Kurt Markley, managing director of Apricorn, discusses three steps to improve your data backup and resilience plans.

CIO Business Intelligence
MARCH 26, 2025
Allow me to explain by discussing what legacy platform modernization entails, along with tips on how to streamline the complex process of migrating data from legacy platforms. Protect data security and privacy Along similar lines, ensuring data security and privacy shouldnt be something you do after modernization is complete.

Network World
JUNE 28, 2019
Cisco issued three “critical” security warnings for its DNA Center users – two having a Common Vulnerability Scoring System rating of 9.8 How to buy SD-WAN technology: Key questions to consider when selecting a supplier. How to pick an off-site data-backup method. What are the options for security SD-WAN?

CIO Business Intelligence
MARCH 25, 2025
These areas are considerable issues, but what about data, security, culture, and addressing areas where past shortcuts are fast becoming todays liabilities? This will free them to bring their skills and creativity to higher-value activities such as enhancing data security and delivering innovative solutions for customers.

Network World
MARCH 31, 2020
More about SD-WAN : How to buy SD-WAN technology: Key questions to consider when selecting a supplier • How to pick an off-site data-backup method • SD-Branch: What it is and why you’ll need it • What are the options for security SD-WAN?

SecureWorld News
DECEMBER 8, 2024
Quantum computing brings both opportunities for advancement and significant security challenges. Quantum computing can rapidly process large datasets, benefiting fields like AI and machine learning, but it also poses a risk to current encryption by potentially decrypting secure data.

CTOvision
JANUARY 16, 2019
Read Maria Korolov’s article about how you can protect your backups from ransomware on CSO Online : Despite a recent decline in attacks, ransomware still poses significant threats to enterprises, as the attacks against several major newspapers demonstrated this month. It is also becoming more capable.

IT Toolbox
OCTOBER 10, 2023
Enhance ransomware resilience with a solid response playbook and trusted backup strategies. The post How to Enhance Ransomware Resilience: A Complete Playbook appeared first on Spiceworks.

Network World
NOVEMBER 4, 2024
Data protection is a broad category that includes data security but also encompasses backup and disaster recovery, safe data storage, business continuity and resilience, and compliance with data privacy regulations. Cloud security posture management (CSPM) tools can help identify misconfigurations, among other risks.

Network World
MAY 9, 2019
How to buy SD-WAN technology: Key questions to consider when selecting a supplier. How to pick an off-site data-backup method. What are the options for security SD-WAN? Cisco last year added its Viptela SD-WAN technology to the IOS XE version 16.9.1 Cisco bought Viptela in 2017. . More about SD-WAN.

Tech Republic Cloud
SEPTEMBER 18, 2019
Secure backup of vital data is a necessity in business. With cloud computing services like AWS Backup, businesses can contract for fast, reliable backup services on an as-needed basis.

Network World
AUGUST 9, 2024
It’s not just knowing how to set up and maintain your servers and understanding how system commands work that makes you a good system administrator. This might involve restoring a user account from your backups, reverting to an older version of an application, or even, depending on where you’re working, reverting to a backup server.

SPF13
JANUARY 11, 2012
Backup, Replication and Disaster Recovery. One of the most common concerns people have is how to ensure that their application is safe, secure and available in the event of an emergency. A backup consists of a dump of the data ideally stored in a remote secure location. s important to keep (offsite) backups.

CIO Business Intelligence
FEBRUARY 1, 2024
When organizations buy a shiny new piece of software, attention is typically focused on the benefits: streamlined business processes, improved productivity, automation, better security, faster time-to-market, digital transformation. Backup: Application data doesn’t simply live in one place. Then there’s backups and disaster recovery.

Network World
MARCH 5, 2025
As organizations grapple with exponential data growth and complex hybrid cloud environments, IT leaders and professionals who can effectively manage, optimize and secure data storage are indispensable, says Gina Smith, research director at IDC and lead for its IT Skills for Digital Business practice. Price: $150 Exam duration: 1.5

CIO Business Intelligence
DECEMBER 18, 2024
However, CIOs must still demonstrate measurable outcomes and communicate these imperatives to senior leadership to secure investment. According to Salesforces Perez, even though AI brings much opportunity, it also introduces complexity for CIOs, including security, governance, and compliance considerations.

Network World
DECEMBER 10, 2024
But networking vendors are constantly innovating to keep pace with skyrocketing volumes of traffic that need to move securely and reliably across complex multicloud environments. It is the first and only secure networking solution built to deliver performance, agility, simplicity, and security without tradeoffs.

CIO Business Intelligence
SEPTEMBER 23, 2022
The practice brings together formerly separate disciplines of information security, business continuity, and disaster response (BC/DR) deployed to meet common goals. It’s about making sure there are regular test exercises that ensure that the data backup is going to be useful if worse comes to worst.”. A Cyberresilience Road Map.

CIO Business Intelligence
MARCH 15, 2023
Multifactor authentication fatigue and biometrics shortcomings Multifactor authentication (MFA) is a popular technique for strengthening the security around logins. Securing the software supply chain The Log4j vulnerability that reared its ugly head in late 2021 showed a bright light on the problem of software supply chain security.

Tech Republic Security
DECEMBER 6, 2022
Your virtual machines are the backbone of your business and are essential to running your workloads, from mission-critical backup applications to test and development environments. The VMware Backup For Dummies e-book shows how to ensure seamless recovery of critical workloads with an agentless backup solution.

Tech Republic Security
DECEMBER 6, 2022
Your virtual machines are the backbone of your business and are essential to running your workloads, from mission-critical backup applications to test and development environments. The VMware Backup For Dummies e-book shows how to ensure seamless recovery of critical workloads with an agentless backup solution.

CIO Business Intelligence
DECEMBER 7, 2023
Moreover, there are increasing consumer and regulatory expectations for both enterprise security and continuity today. How to ensure business continuity plan support, awareness One way to ensure your plan is not successful is to adopt a casual attitude toward its importance.

The Accidental Successful CIO
AUGUST 14, 2013
It turns out that there is another problem that has arrived at the same time and right now there is not a clear answer to how best to deal with it: how to back up all of that data. Solutions To Your Big Data Backup Problem. Technology "big data" archive audio backup capacity cost disk images storage tape video'

Network World
MARCH 31, 2020
More about SD-WAN : How to buy SD-WAN technology: Key questions to consider when selecting a supplier • How to pick an off-site data-backup method • SD-Branch: What it is and why you’ll need it • What are the options for security SD-WAN?

Network World
AUGUST 13, 2024
Early on July 19, just minutes after data security giant CrowdStrike released what was supposed to be a security update, enterprises started losing Windows endpoints, and we ended up with one of the worst and most widespread IT outages of all time. There’s been a lot said about the why and the how.
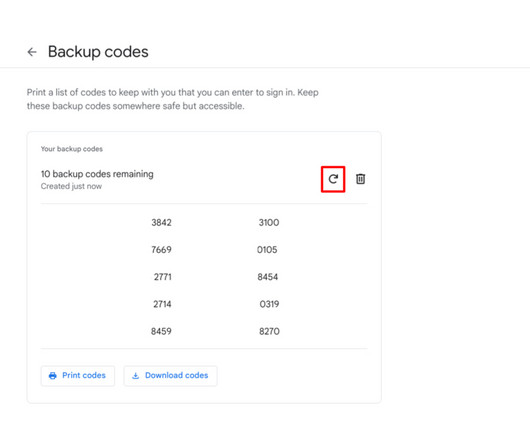
Tech Republic
AUGUST 17, 2023
Learn how to retrieve and generate Google 2FA backup codes with this easy-to-follow, step-by-step tutorial.

CIO Business Intelligence
OCTOBER 20, 2023
Stakeholders need mainframe data to be safe, secure, and accessible — and storing data in these archaic environments accomplishes none of these goals. Resilience: Hyperscale cloud storage is replicated multiple times throughout the infrastructure, and hybrid cloud environments have many excellent additional backup options.

Galido
DECEMBER 6, 2018
Information Technology Blog - - How to Choose a Data Backup Service - Information Technology Blog. New clients, existing customers, employees, and other relevant public of the organization determine a huge chunk of data, some of which is invaluable, and that explains why data backup services are paramount for every company.

CIO Business Intelligence
SEPTEMBER 21, 2023
With the CSO50 Conference + Awards coming to the We-Ko-Pa Casino Resort in Fort McDowell, Arizona, October 2-4, we asked Bill Tsoukatos, Information Technology Director at Fort McDowell Enterprises, which owns the resort, to tell us what it’s like to manage IT security at a casino property.

Mick's IT Blog
DECEMBER 30, 2012
How to Backup Multiple Systems to a Single Online Backup Service Account. You might have wondered how to backup multiple computers in your home with a single online backup service. The answer is yes, you can do this and here is how. We need to give it additional privileges Here is how.

Tech Republic Data Center
JULY 30, 2021
Jack Wallen teaches you how to use simple bash scripts to automate backing up your VirtualBox VMs.

CIO Business Intelligence
JUNE 28, 2022
You need to figure out what to protect and how to protect it. On the primary storage front, you’d be smart to do an analysis of the data, determine what data needs to be encrypted and what doesn’t, and figure out how the protection needs to keep your company in compliance, especially if your company is in a regulated market.

CIO Business Intelligence
OCTOBER 6, 2023
During a health check, expert database administrators will work with you and perform an exhaustive review of the database environment to help ensure that it’s running as smoothly as possible, conforms to best practices, and utilizes practical and sound backup, recovery, and high availability strategies.

The Verge
JULY 21, 2021
Using the tool involves backing up your phone to a separate computer and running a check on that backup. In its documentation, Amnesty says the analysis its tool can run on Android phone backups is limited, but the tool can still check for potentially malicious SMS messages and APKs. Again, we recommend following its instructions.

Eric D. Brown
DECEMBER 9, 2013
Organizations have been trying to figured out how to manage this new ‘bring your own device’ (BYOD) reality but there are very few organizations that have robust strategies and solutions to manage this new mobile world. Meaning, backup and recovery are built around the idea that your devices are able to access to the network.

CTOvision
MARCH 22, 2017
Most companies reported that they know what they need to do to increase their security levels, but it often just falls through the cracks. The best way to protect against ransomware is to have a strong series of backup solutions.

CIO Business Intelligence
FEBRUARY 12, 2025
About the same percentage say they got training that covered both the basics, like how to write prompts, but was also tailored to their role, their tasks, and their workflow. Just as importantly, they apply the same compliance, governance, information security, and auditing tools to agentic AI. There are better processes.

Tech Republic Security
AUGUST 9, 2023
Learn actionable tactics for IT departments on how to manage backups and enable staff so that ransomware is no longer a mythical threat, but a controlled risk. Secure Backup is your best line of Defense. The Ransomware Prevention Kit includes: Proprietary white paper Ransomware Simulation NEW! Veeam Data Platform demo

Kitaboo
MAY 14, 2019
Also read: [Guide] How to Deliver Workplace Safety Training on Mobile Devices. Here’s how you can make workplace safety training modules future-ready: 1. Cloud is the most reliable and secure backup you can have. Organizations are heavily relying on cloud-based storage these days to keep their data secure.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?



Let's personalize your content