Interview on Automated Malware Removal
CTOvision
JULY 29, 2014
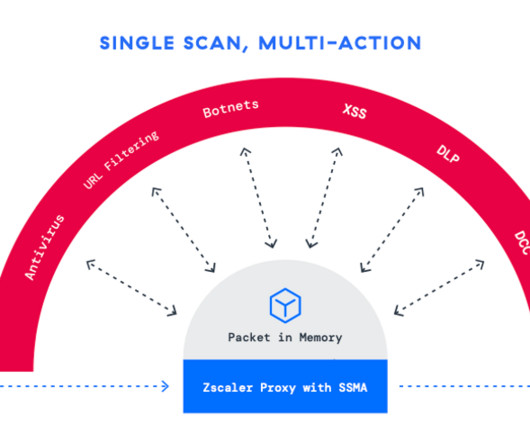
Three Questions on Automated Malware Removal with Bob Gourley, Cognitio Corp and CTOVision. While there’s still an emphasis – and related spending – on malware detection, most incident response teams are actually overwhelmed by vast number of security alerts they receive. Another day, another data breach. Bob Gourley: That’s simple.












































Let's personalize your content