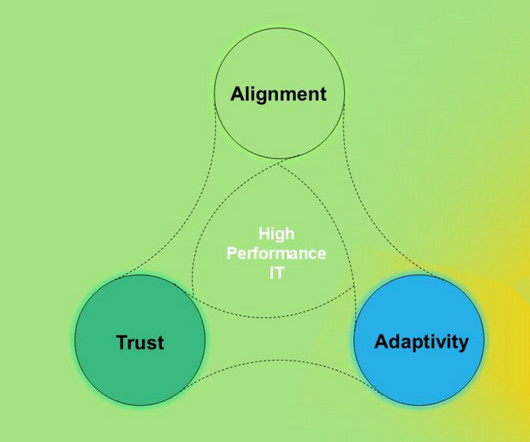
Trust, Alignment, And Adaptivity Must Be The Focus Of Your AI Initiatives
Forrester IT
AUGUST 12, 2024
Successful AI projects depend on three things: trust, alignment, and adaptivity. Learn how technology and CX professionals can further trust, alignment, and adaptivity when devising effective, sustainable, and scalable AI solutions.









































Let's personalize your content