RAG Is All The Rage — Retrieval-Augmented Generation, Demystified
Forrester IT
JULY 23, 2024
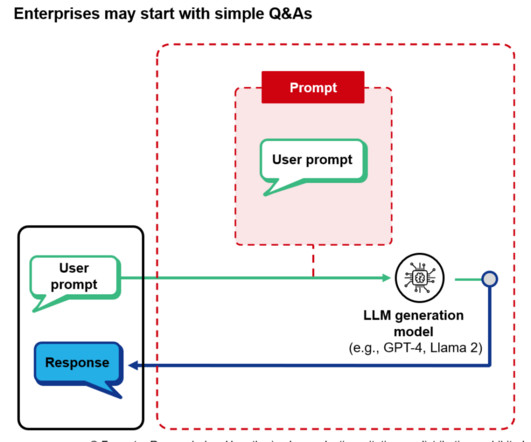
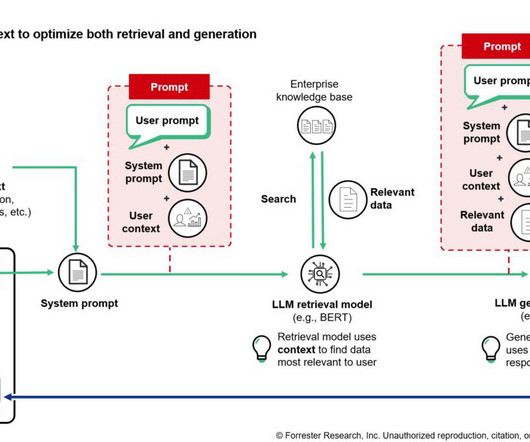
Enterprises experimenting with generative AI (genAI) are prioritizing use cases that enable internal and external users to better retrieve information they need, be it data, how-to pages, corporate policies, or return policies. Retrieval-augmented generation (RAG) is now the most common underlying approach for building this type of large language model (LLM)-based enterprise knowledge-retrieval application.










































Let's personalize your content