5 Pillars of Sustainable Digital Transformation
Information Week
APRIL 1, 2022
C-suite execs need to move away from short-term thinking and instead consider the long-term impact and value of the decisions they are making.

Information Week
APRIL 1, 2022
C-suite execs need to move away from short-term thinking and instead consider the long-term impact and value of the decisions they are making.

Information Week
APRIL 14, 2022
The use of open-source software offers multiple benefits to organizations of all sizes, but open-source security is often undermanaged.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Forrester IT
APRIL 26, 2022
From their interactions as consumers, B2B buyers and customers are already accustomed to receiving relevant information curated by algorithms and delivered at the right time in dynamic and digestible formats. Across channels, devices, and interfaces, these audiences ask for what they want. They’re also aware of how their behavior drives the algorithmic co-creation of interest-based […].

Association of Information Technology Professional
APRIL 6, 2022
Whether you prefer learning in a classroom or self-study, CompTIA live online training may be the right option for you by giving you the best of both worlds.

Advertiser: ZoomInfo
Sales and marketing leaders have reached a tipping point when it comes to using intent data — and they’re not looking back. More than half of all B2B marketers are already using intent data to increase sales, and Gartner predicts this figure will grow to 70 percent. The reason is clear: intent can provide you with massive amounts of data that reveal sales opportunities earlier than ever before.

Social, Agile and Transformation
APRIL 4, 2022
She was a developer with an innate talent for UX. A leader with big ideas but trapped supporting a website on an outdated content management system. She learned agile, led offshore development teams, and developed her confidence to become an architect on several modern SaaS platforms. He could have just been another software developer on one of our teams, trying to.

Doctor Chaos
APRIL 10, 2022
Many people who know me know that I have accumulated quite a few frequent flyer miles. Before COVID, I had many years where I would clock in 200k+ air miles in a single year. It was pretty easy to rack up miles when you have a job that requires travel Sunday through Friday. I can’t say I don’t enjoy it. Some of that has to do with the fact that I have learned a few tips to make my travel life easier.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Information Week
APRIL 14, 2022
Although the adoption of this technology will be widespread, there is still time for workers to get ahead of the curve so that they do not become obsolete once the integration is complete.

Forrester IT
APRIL 20, 2022
Alongside the COP26 Conference, many businesses communicated their green pledge and how much they are acting to protect the environment. Expect more of this to happen this week, with Earth Day falling on Friday, April 22 — and get ready to see many brands accused of greenwashing. Greenwashing — when a business is perceived to […].

Association of Information Technology Professional
APRIL 20, 2022
With the launch of the new CompTIA A+ came many questions, so we’ve set out to answer them here. Keep reading to learn more about the CompTIA A+ core series.

Tech Republic Security
APRIL 1, 2022
A phishing technique called Browser in the Browser (BITB) has emerged, and it’s already aiming at government entities, including Ukraine. Find out how to protect against this new threat. The post “Browser in the Browser” attacks: A devastating new phishing technique arises appeared first on TechRepublic.

Advertiser: GEP
For years, you and your team have fought an uphill battle. Supply disruptions. Cost pressures. ESG compliance. You name it, and you’ve had to navigate it. In 2025, many challenges will persist, but procurement and supply chain teams have a powerful tool with rapidly advancing capabilities to tackle them — artificial intelligence (AI). The GEP Outlook 2025 report examines the disruptive transformation AI is driving in procurement and supply chains, alongside other key trends and the macroeconomic

Network World
APRIL 4, 2022
Today’s announcement of IBM’s new z16 mainframes promises a system that caters to enterprise needs that include support for AI, security, hybrid cloud, and open source efforts well into the future. The new, more powerful and feature-rich Big Iron boasts an AI accelerator built onto its core Telum processor that can do 300 billion deep-learning inferences per day with one millisecond latency and includes what IBM calls a quantum-safe system to protect organizations from anticipated quantum-based

Anoop
APRIL 29, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Install Microsoft Windows Defender Application Guard for Edge appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Jitesh Kumar.

Information Week
APRIL 6, 2022
Big tech and other companies are mandating employees return to the office, at least on a hybrid basis, after two years of pandemic-driven work-from-home. Will employees show up? Or will they quit?

Forrester IT
APRIL 18, 2022
Earth Day is Upon Us! Earth Day is this Friday, April 22nd. As such, I wanted to take a break from my normal IT service management/knowledge management cover to discuss my own journey to reduce my carbon footprint using smart technologies: I have lived in California for over 20 years, and every month I get […].

Speaker: Carolyn Clark and Miriam Connaughton
Forget predictions, let’s focus on priorities for the year and explore how to supercharge your employee experience. Join Miriam Connaughton and Carolyn Clark as they discuss key HR trends for 2025—and how to turn them into actionable strategies for your organization. In this dynamic webinar, our esteemed speakers will share expert insights and practical tips to help your employee experience adapt and thrive.

Association of Information Technology Professional
APRIL 1, 2022
Learn how the new CompTIA A+ has been updated to reflect the changing role of IT support in a hybrid work environment.

Tech Republic Security
APRIL 6, 2022
The Washington Post has revealed details of a contract with a software company that will allow the FBI to track social media posts. The post FBI investing millions in software to monitor social media platforms appeared first on TechRepublic.

Network World
APRIL 7, 2022
Picking just 10 Linux open source security tools isn’t easy, especially when network professionals and security experts have dozens if not several hundred tools available to them. There are different sets of tools for just about every task—network tunneling, sniffing, scanning, mapping. And for every environment— Wi-Fi networks , Web applications, database servers.

Anoop
APRIL 4, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Create Custom XML File for Office 365 Intune Deployment appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Kannan CS.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Information Week
APRIL 21, 2022
At its core, the value of a non-fungible token (NFT) today rests in how it is perceived by others. But an NFT's value over time remains to be seen.

Forrester IT
APRIL 14, 2022
[This post was coauthored by Christy Lano.] Forrester’s latest report on the state of fintech shows that funding for fintech companies not only rebounded (from a decidedly down year in 2021) but has skyrocketed to new, historic heights. To dive deeper into this research, we’re looking at specific fintech companies and — more importantly — […].

Association of Information Technology Professional
APRIL 22, 2022
You’ve decided that a career in IT is for you. Read on to learn about how to study for CompTIA A+ and start your career in tech.

Tech Republic Security
APRIL 1, 2022
A report from NCC Group profiles the industries plagued by ransomware as well as the most active hacking groups in February. The post Ransomware attacks are on the rise, who is being affected? appeared first on TechRepublic.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda
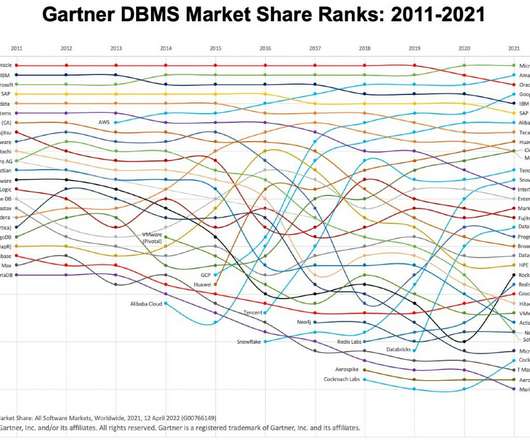
Tech Republic Cloud
APRIL 19, 2022
Databases are supposed to be the last thing an enterprise considers changing, but the cloud is upending all that, for several reasons. The post New Gartner report shows massive growth in the database market, fueled by cloud appeared first on TechRepublic.

Anoop
APRIL 20, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Manage Drivers Using PnPUnattend Command line Utility appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Jitesh Kumar.

Information Week
APRIL 25, 2022
As an overarching best practice, align anything and everything you propose, design, or deploy for cloud around how it benefits the company’s critical applications and the business.

Forrester IT
APRIL 13, 2022
What Is Going On? One of our less pleasant responsibilities here at Forrester is commenting on serious business, security, or technical failures in the digital and IT industry. Due to its duration and the implications for a subset of the user base, the current Atlassian outage rises to that level. Atlassian is staking its future […].

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.

Association of Information Technology Professional
APRIL 13, 2022
The help desk is more important than ever, with organizations needing employees with the most up-to-date skills.
Tech Republic Security
APRIL 13, 2022
The new vulnerabilities are being actively exploited, prompting CISA to advise federal agencies and organizations to patch them in a timely manner. The post CISA adds 8 known security vulnerabilities as priorities to patch appeared first on TechRepublic.

Network World
APRIL 20, 2022
Why is it that over 90% of enterprises tell me that they expect to spend more on security over the next three years, and almost 60% say they expect to spend less on networking? We obviously think that network technology is getting more efficient, more competitive. Why isn’t that the case for security? The short answer is that enterprises have been chasing acronyms and not solutions.
Anoop
APRIL 27, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post 3 Best Methods to Import SCCM PowerShell Module Cmdlets appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Dhanraj Barman.

Advertiser: ZoomInfo
In this exploration, we're diving into predictions about the future of sales. We're talking about a complete shake-up powered by automation and artificial intelligence (AI). These aren't just fancy tools — they're real game-changers. Automation and AI are here to redefine every interaction, making them smarter, faster, and more meaningful. From personalized customer journeys to streamlined sales processes, the goal is to make every moment count, enhancing both efficiency and connection.
Let's personalize your content