Find Your Perfect IT Job: One Step at a Time
Association of Information Technology Professional
DECEMBER 2, 2022
IT pro Ryan Anastasia outlines what it takes to become a systems administrator.

Association of Information Technology Professional
DECEMBER 2, 2022
IT pro Ryan Anastasia outlines what it takes to become a systems administrator.

Association of Information Technology Professional
DECEMBER 14, 2022
Building a plan for speed that also considers long-term objectives will be the best way to clear the hurdles organizations may face in 2023.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

TM Forum
DECEMBER 5, 2022
The past few years have seen the particular need for radical, rapid change within communications service providers (CSPs), particularly cloud transformation to support 5G innovation. Join us to understand how telecom’s cloud investment and transformation have evolved over the last decade, main investments, hyperscaler partnerships and hybrid strategies.
Social, Agile and Transformation
DECEMBER 12, 2022
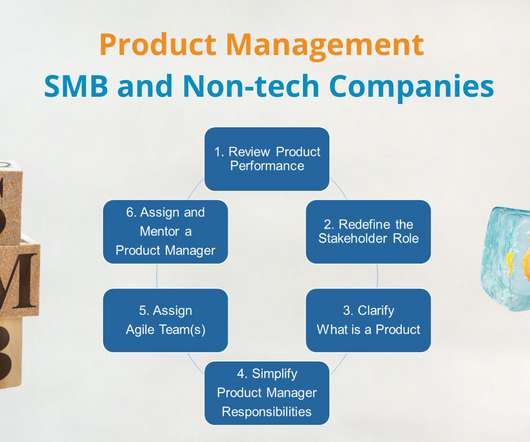
I learned two truths this week. During the Coffee with Digital Trailblazers, a LinkedIn audio event that I host most Fridays at 11 am ET, Jay Cohen shared that January was a good time of the year to focus on learning programs and driving department and team-level realignments. It makes sense because people return to work from the holidays refreshed and ready to learn.

Advertiser: ZoomInfo
Sales and marketing leaders have reached a tipping point when it comes to using intent data — and they’re not looking back. More than half of all B2B marketers are already using intent data to increase sales, and Gartner predicts this figure will grow to 70 percent. The reason is clear: intent can provide you with massive amounts of data that reveal sales opportunities earlier than ever before.

Information Week
DECEMBER 9, 2022
Artificial intelligence represents an exciting new frontier in technology. How do companies decide how to begin leveraging next-generation solutions that will result in tangible value?

Forrester IT
DECEMBER 27, 2022
Command, Control, And The Changing Workplace Organizational and people management has perennially been a favorite topic of writers and researchers. Even the Bible tells a story of how Moses’ father-in-law gave him advice about management and delegation of tasks! For much of the 20th century, a top-down, command-and-control style of management was favored, with a […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

The Accidental Successful CIO
DECEMBER 21, 2022
CIOs are responsible for ensuring that software projects don’t fail Image Credit: Spry. As the person with the CIO job, it is expected that you’ll manage an IT department that can successfully complete software projects in order to show the company the importance of information technology. However, this is not always the case. In fact, sometimes the software projects that our department are working on fail – and may even fail spectacularly.

Association of Information Technology Professional
DECEMBER 19, 2022
Luis Fernandez, a cyber threat hunter, got an early start as a gamer. He has built an impressive career, with CompTIA providing knowledge and confidence at each step.

Social, Agile and Transformation
DECEMBER 19, 2022
A few weeks ago, I reviewed my son’s C code that he and a classmate developed for their college first-year computer science class. The assignment required them to use a linked list to simulate shuffling a deck of cards, finding pairs, and exchanging cards between players. They struggled to debug their code, and running it produced inconsistent results and null.

TM Forum
DECEMBER 12, 2022
Communications service providers (CSPs) have fresh impetus to transform the way their networks operate as they aim to make their network operations more sustainable.. Read this report to learn more about: The trends driving change in sustainability strategies. How some of the world’s leading CSPs are harnessing AI and machine learning to reduce power usage.

Advertiser: GEP
For years, you and your team have fought an uphill battle. Supply disruptions. Cost pressures. ESG compliance. You name it, and you’ve had to navigate it. In 2025, many challenges will persist, but procurement and supply chain teams have a powerful tool with rapidly advancing capabilities to tackle them — artificial intelligence (AI). The GEP Outlook 2025 report examines the disruptive transformation AI is driving in procurement and supply chains, alongside other key trends and the macroeconomic

Forrester IT
DECEMBER 19, 2022
Long-standing “waterfall” knowledge management (KM) practices are failing to meet the needs of the modern enterprise, and technology leaders must reassess their approach. Agile principles transform knowledge management within the enterprise from lengthy, delay-laden processes to lean practices that seek to make sharing knowledge easy and adaptable. For the same reasons that agile principles have […].

IT Toolbox
DECEMBER 14, 2022
Here’s how composability and proactive adapting can enable digital transformation in banking. The post Composability: The Key to Digital Transformation in Banking appeared first on.

The Accidental Successful CIO
DECEMBER 14, 2022
When workers can’t be found, it’s time for the robots to step in Image Credit: Zach. CIOs are, among other things, responsible for making sure that the business keeps running smoothly. Although we generally only get involved in hiring when the company is hiring people to work in the IT department, it turns out that we can also play a role in hiring in other parts of the company.

Association of Information Technology Professional
DECEMBER 5, 2022
Eduardo Gijon explains what it’s like to transition from a general IT role to a cybersecurity career – and the perks that follow.

Speaker: Carolyn Clark and Miriam Connaughton
Forget predictions, let’s focus on priorities for the year and explore how to supercharge your employee experience. Join Miriam Connaughton and Carolyn Clark as they discuss key HR trends for 2025—and how to turn them into actionable strategies for your organization. In this dynamic webinar, our esteemed speakers will share expert insights and practical tips to help your employee experience adapt and thrive.

Information Week
DECEMBER 28, 2022
Developers and data scientists can work together using MLOps through a shared methodology to make sure that machine learning initiatives are in line with wider software delivery and, even more broadly, IT-business alignment.

Anoop
DECEMBER 6, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post SCCM 2211 Upgrade Step by Step Guide | New Features appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar.

Forrester IT
DECEMBER 20, 2022
As Forrester approaches its 40th anniversary, we reflect on a few of the monumental changes that we correctly predicted.

IT Toolbox
DECEMBER 13, 2022
A data center houses backend computers (without a user interface) and ancillary systems like cooling and networking. The post What Is a Data Center? Working, Types, Architecture, and Best Practices appeared first on.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Network World
DECEMBER 13, 2022
Backup and recovery systems are at risk for two types of ransomware attacks: encryption and exfiltration – and most on-premises backup servers are wide open to both. This makes backup systems themselves the primary target of some ransomware groups, and warrants special attention. Hackers understand that backup servers are often under-protected and administered by junior personnel that are less well versed in information security.

Association of Information Technology Professional
DECEMBER 12, 2022
Perks like remote work, work-life balance and a lucrative salary are all attractive. But Joseph Marchis found something even more rewarding as a senior security engineer.

Information Week
DECEMBER 1, 2022
Many say the pace of digital transformation has slowed, but IT teams are just ushering in the acceleration phase as businesses ensure transformed internal systems are translated externally.

Tech Republic Cloud
DECEMBER 6, 2022
Learn how to enable Defender for Cloud, the differences between the basic and enhanced versions, and what they can do for your security posture. The post How to enable Microsoft Defender for Cloud plans through the Azure portal appeared first on TechRepublic.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

Forrester IT
DECEMBER 20, 2022
“You haven’t defined what story is,” said the voice of experience that afternoon, September 16, 2022. “That’s odd,” I thought. “What am I missing?” We were discussing my first leadership storytelling report, Master Storytelling For Impactful Leadership, intended to explain the “what?” and “why?” of leadership storytelling. In the report, I describe the three-arc structure […].

IT Toolbox
DECEMBER 6, 2022
R and Python are among the most commonly used programming languages in the age of AI. The post R vs. Python: 12 Key Comparisons appeared first on.

Network World
DECEMBER 16, 2022
Hybrid and multicloud initiatives will continue to shape enterprise IT in 2023, and the impact on data-center networking will be felt across key areas including security, management, and operations. Network teams are investing in technologies such as SD-WAN and SASE , expanding automation initiatives, and focusing on skills development as more workloads and applications span cloud environments.

Association of Information Technology Professional
DECEMBER 8, 2022
Cybersecurity and emerging tech were top themes for CompTIA research and resources, but legal and business trends were also popular downloads in 2022.

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.

Information Week
DECEMBER 5, 2022
An entire week of coverage devoted to the question: How do we give privacy back to the people when customer data is now the coin of the realm and the fuel that powers business?

Social, Agile and Transformation
DECEMBER 26, 2022
Before I say goodbye to 2022, I want to thank the people and companies that contributed to my successful year. In 2022, I published over 130 articles, and my top subjects were about data science data governance, dataops (29 posts), digital transformation (25), agile ways of working (19), and DevOps (15). Most of my writing appears on this blog (54 posts), InfoWorld (41), and the.

Forrester IT
DECEMBER 7, 2022
We look at a few ways that retailers can use messaging to support customers through the holidays and beyond.

IT Toolbox
DECEMBER 7, 2022
Find out the top five AI trends to prepare for. The post Top 5 AI Trends to Look Out for in 2023 appeared first on.

Advertiser: ZoomInfo
In this exploration, we're diving into predictions about the future of sales. We're talking about a complete shake-up powered by automation and artificial intelligence (AI). These aren't just fancy tools — they're real game-changers. Automation and AI are here to redefine every interaction, making them smarter, faster, and more meaningful. From personalized customer journeys to streamlined sales processes, the goal is to make every moment count, enhancing both efficiency and connection.
Let's personalize your content