Digital Sovereignty Is Changing The Cloud Market
Forrester IT
FEBRUARY 5, 2024
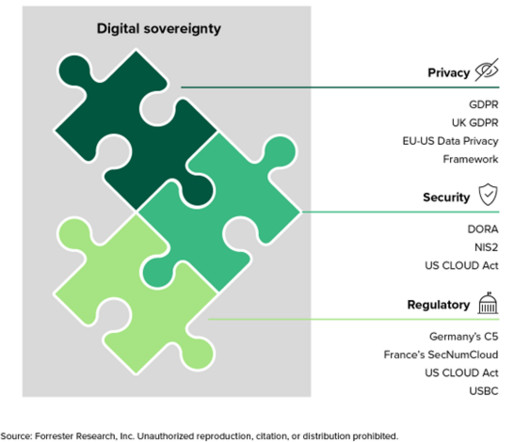
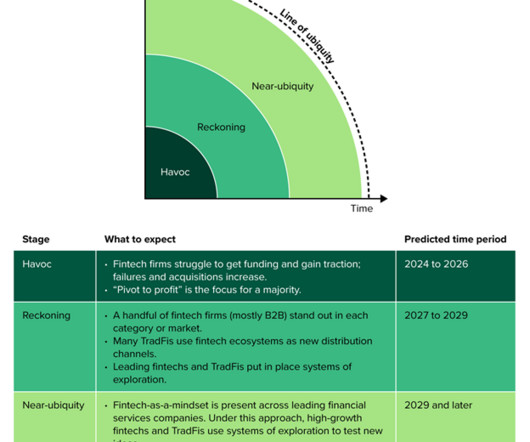
In 2023 global cloud vendors all came up with their own digital sovereignty solution to address rising concerns from their customers. However, when I ask customers and vendors to define what digital sovereignty means for them, silence is the most common response.












































Let's personalize your content