AI focus shifts to ‘small and wide’ data
Venture Beast
SEPTEMBER 7, 2021
A Gartner report finds that companies will increasingly embrace responsible AI while seeking ways to more efficiently deploy AI systems. Read More.

Venture Beast
SEPTEMBER 7, 2021
A Gartner report finds that companies will increasingly embrace responsible AI while seeking ways to more efficiently deploy AI systems. Read More.

Association of Information Technology Professional
SEPTEMBER 9, 2021
Do you know which tech trends you should be looking out for in 2021? Here are the top 15 emerging trends in information technology for 2021.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CTOvision
SEPTEMBER 9, 2021
DataRobot announced three key additions to its executive leadership bench, welcoming Sirisha Kadamalakalva as the company’s first Chief Strategy Officer and Steve Jenner, who steps into the role of Chief Customer Officer. DataRobot veteran Jay Schuren has been elevated from SVP of Customer Success and Enablement to Chief Data Science Officer, representing the deep talent […].
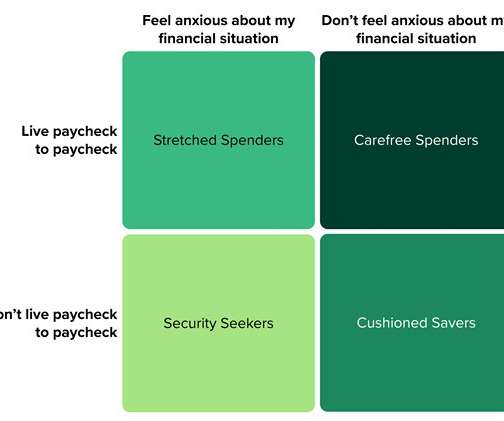
Forrester IT
SEPTEMBER 9, 2021
To help financial services firms understand where French consumers stand on the financial well-being spectrum, Forrester surveyed 2,592 French online adults in 2020.

Advertiser: ZoomInfo
Sales and marketing leaders have reached a tipping point when it comes to using intent data — and they’re not looking back. More than half of all B2B marketers are already using intent data to increase sales, and Gartner predicts this figure will grow to 70 percent. The reason is clear: intent can provide you with massive amounts of data that reveal sales opportunities earlier than ever before.

Social, Agile and Transformation
SEPTEMBER 7, 2021
Labor Day has new meaning in our house. I have tremendous new respect for all people who earn their living from hard, sweaty, dirty work. And yet, while I call this my personal disaster recovery, it really isn't that personal or that significant of a disaster. My family and I came home to Hurricane Ida's wreckage after it dumped an estimated seven inches of rain in our town.

Association of Information Technology Professional
SEPTEMBER 8, 2021
Learn how pen testing and vulnerability assessment work together to strengthen a cybersecurity strategy, and how CompTIA PenTest+ can teach you these skills.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Forrester IT
SEPTEMBER 8, 2021
In many ways, virtual events are more convenient than in-person events, but they demand a different approach as a delegate.

Anoop
SEPTEMBER 10, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Intune Security Baseline Microsoft Defender Policy Troubleshooting Tips for Cloud PCs appeared first on HTMD Blog #1 by Anoop C Nair.

Association of Information Technology Professional
SEPTEMBER 10, 2021
If you have the strategic, operational and tactical skills necessary to protect data in the cloud, cloud security specialist may be a good fit for you.

CTOvision
SEPTEMBER 9, 2021
Read Jacob Silverman’s criticism of Facebook’s version of The Metaverse and why he calls its the soulless version of future on The New Republic : If you’ve skimmed the tech press in recent months, it’s been difficult to escape articles about the breathlessly overhyped promise of “the metaverse,” a vast digital space that combines virtual […].

Advertiser: GEP
For years, you and your team have fought an uphill battle. Supply disruptions. Cost pressures. ESG compliance. You name it, and you’ve had to navigate it. In 2025, many challenges will persist, but procurement and supply chain teams have a powerful tool with rapidly advancing capabilities to tackle them — artificial intelligence (AI). The GEP Outlook 2025 report examines the disruptive transformation AI is driving in procurement and supply chains, alongside other key trends and the macroeconomic

Forrester IT
SEPTEMBER 7, 2021
The comparison between relay racing and revenue organizations has been around forever. Marketing generates a qualified opportunity and hands it off to sales to pursue and win the deal. Sales then passes it on to customer success to support and renew the relationship. In the past, this approach made sense, but today’s buyers don’t work […].

Tech Republic Security
SEPTEMBER 9, 2021
Some of these phrasings are standard day-to-day subject lines, but as one expert explained, "the attacker wants you to be moving too fast to stop and question if it's legitimate.

Anoop
SEPTEMBER 8, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Enable Windows 11 Patching using SCCM WSUS appeared first on HTMD Blog #1 by Anoop C Nair.

CTOvision
SEPTEMBER 9, 2021
A recent study by S&P Global Market Intelligence and Immuta revealed that companies that follow data privacy and security regulations are leading the way in data strategies. Indeed, it was reported that regulated organizations have to deal with fewer challenges regarding data access and use as well as have a better-dedicated data engineering team and analytics. […].

Speaker: Carolyn Clark and Miriam Connaughton
Forget predictions, let’s focus on priorities for the year and explore how to supercharge your employee experience. Join Miriam Connaughton and Carolyn Clark as they discuss key HR trends for 2025—and how to turn them into actionable strategies for your organization. In this dynamic webinar, our esteemed speakers will share expert insights and practical tips to help your employee experience adapt and thrive.

Forrester IT
SEPTEMBER 10, 2021
There is no executive role that better aligns with the trust imperative than the CISO. Find out why and how it may impact your organization directly.

Tech Republic Security
SEPTEMBER 9, 2021
IT teams are experiencing employee pushback due to remote work policies and many feel like cybersecurity is a "thankless task" and that they're the "bad guys" for implementing these rules.

Anoop
SEPTEMBER 6, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Download Intune CIS Benchmark for Windows 10 appeared first on HTMD Blog #1 by Anoop C Nair.

Information Week
SEPTEMBER 10, 2021
Business/citizen developers will neither take over the world nor ruin it. Rather than focus on extremes, enterprises should consider the targeted use cases for low code.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Forrester IT
SEPTEMBER 9, 2021
Most companies’ focus on data and technology capabilities is not balanced with focus on people and process. Learn why people skills matter in data insights.

Tech Republic Security
SEPTEMBER 8, 2021
Technology is not the only answer: An expert suggests improving the human cyber capacity of a company's workforce plus cybersecurity technology offers a better chance of being safe.

Anoop
SEPTEMBER 8, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Cloud PC Monthly Patching Process using Intune appeared first on HTMD Blog #1 by Anoop C Nair.

Information Week
SEPTEMBER 8, 2021
If optimizing your cloud spending is on your to-do list this year, these tips could help you stay within budget.

Advertiser: ZoomInfo
In this exploration, we're diving into predictions about the future of sales. We're talking about a complete shake-up powered by automation and artificial intelligence (AI). These aren't just fancy tools — they're real game-changers. Automation and AI are here to redefine every interaction, making them smarter, faster, and more meaningful. From personalized customer journeys to streamlined sales processes, the goal is to make every moment count, enhancing both efficiency and connection.

Forrester IT
SEPTEMBER 10, 2021
Digitally savvy delegators are an overlooked segment and represent an attractive opportunity for wealth management firms right now. As incumbents and fintechs alike continue to compete for customers, firms need to understand who digitally savvy delegators are and design the right solutions to attract and retain them. I recently published a report about this customer […].

Tech Republic Security
SEPTEMBER 8, 2021
Only 33% of users surveyed by NordPass changed the default passwords on their IoT devices, leaving the rest susceptible to attack.

Anoop
SEPTEMBER 6, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Outlook Web App OWA instead of Outlook Desktop App 4 Months Experience appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Cloud
SEPTEMBER 10, 2021
Choosing CRM software is difficult with all of the options available. Compare features of the best CRM tools of 2021.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

Forrester IT
SEPTEMBER 10, 2021
Greetings everyone! Each month, the infrastructure and operations (I&O) team writes incredible research. As a research director, I get to not only see the final outcome but also all of the work and client insights that went into its creation. For those who know me, I am quick to call these out via inquiry calls […].

Tech Republic Security
SEPTEMBER 9, 2021
Cyberattacks have surged during the coronavirus pandemic as criminals rake in bountiful ransomware payouts. Malicious office docs have been on the rise for months, per a new report.

Anoop
SEPTEMBER 9, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Windows 11 with Recycle Bin Modern Context Menu Adoption Preview Build appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Cloud
SEPTEMBER 10, 2021
Adjust a few settings, install an extension, select files and you can work without an internet connection on a Chromebook.

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.
Let's personalize your content