9 Ways to Improve IT and Operational Efficiencies in 2020
Information Week
JANUARY 2, 2020
Facing economic uncertainty, many IT leaders are looking to become more efficient while also investing in the latest technology.

Information Week
JANUARY 2, 2020
Facing economic uncertainty, many IT leaders are looking to become more efficient while also investing in the latest technology.

CTOvision
JANUARY 2, 2020
Read Carlos Asuncion explain how you can prevent hackers from targeting your mobile payment apps on Dark Reading : Consumers love paying for goods and services with their smartphones. But as more retailers release their own mobile apps with in-store payment options, the threat of fraud must be carefully considered. Retailers offering in-store purchasing through […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
DECEMBER 31, 2019
Bias can result in undesirable AI outcomes. A recent DataRobot survey says organizations are most concerned about its impact on trust and their reputations.

Forrester IT
JANUARY 2, 2020
It’s that time of year. When folks make up their minds that things are going to change. The gym is full of new members who are eager to get into their journey towards some other semblance of better health, or a beach body, or some change that they desire. Others are in that annual state […].

Advertiser: ZoomInfo
Sales and marketing leaders have reached a tipping point when it comes to using intent data — and they’re not looking back. More than half of all B2B marketers are already using intent data to increase sales, and Gartner predicts this figure will grow to 70 percent. The reason is clear: intent can provide you with massive amounts of data that reveal sales opportunities earlier than ever before.
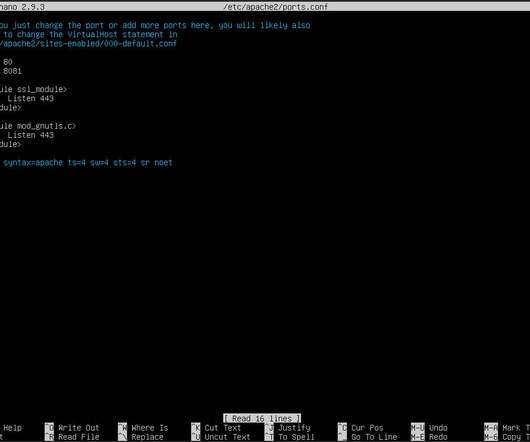
Tech Republic Security
DECEMBER 30, 2019
If you find port 80 is a security risk on your network, you can change the Apache listening port to something non-standard.

CTOvision
JANUARY 1, 2020
The Dali Lama just posted some very wise thoughts for our consideration: Time never stands still, it’s always moving on. The past is beyond our control, but the future is still in our hands. To shape it we must use our intelligence and make an effort. We can change our circumstances. Becoming demoralized is of […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Forrester IT
JANUARY 3, 2020
The best New Year’s resolution? Become machine-learning-literate! It’s good for your organization, your career, and the sanity of your data scientists. See the new “Shatter The Seven Myths Of Machine Learning” report below for a mini course on machine-learning fundamentals and terminology.

Social, Agile and Transformation
DECEMBER 30, 2019
Every once and a while, I draw inspiration from movies and actors/actresses. I have a post paying tribute to the great movie. What about Bob? Baby Steps - A Guide to Digital Transformation. I have another post comparing executive meetings with a classic Darth Vadar scene from The Empire Strike's Back. My two personal favorite movie posts are product management advice from the Tom Hanks movie.

CTOvision
DECEMBER 30, 2019
Read Marcus Chung list seven signs which will tell you if your cybersecurity strategy is failing on Helpnet Security : While most enterprises have come to terms with the fact that a security incident is not a factor of “if,” but rather “when,” many are still struggling to translate this into the right security architecture […].

Linux Academy
JANUARY 1, 2020
To continually support your mission to learn and grow, we encourage you to try these free courses and resources for developing and advancing your Cloud skills. Courses Free in January : Implementing Azure DevOps Development Processes. Azure Cloud Services and Infrastructure. Included with Community Membership. How to Get a Linux Job. This course helps prepare you for applying for and successfully obtaining a Linux Job.

Advertiser: GEP
For years, you and your team have fought an uphill battle. Supply disruptions. Cost pressures. ESG compliance. You name it, and you’ve had to navigate it. In 2025, many challenges will persist, but procurement and supply chain teams have a powerful tool with rapidly advancing capabilities to tackle them — artificial intelligence (AI). The GEP Outlook 2025 report examines the disruptive transformation AI is driving in procurement and supply chains, alongside other key trends and the macroeconomic

Forrester IT
DECEMBER 31, 2019
Is your firm ready for the roaring twenties? Nigel Fenwick predicts the winners in the next decade will be the businesses that master digital product management.

Mick's IT Blog
JANUARY 2, 2020
With the advent of Microsoft Endpoint Manager Configuration Manager 1910, I started researching the upgrade requirements. I happened to run into a great blog post by fellow MVP Martin Bengtsson on what should be done before the upgrade takes place. That got me to thinking that most of the tasks he listed can be automated with PowerShell. The script below will automate the following tasks from his list of prerequisites: Backs up the cd.latest directory to the specified UNC path Disables the follo

CTOvision
DECEMBER 30, 2019
Read Ronald Schmelzer’s article in Forbes about the ways in which the fashion industry is using AI: The fashion industry is just as much about creating demand and brand awareness as it is about the manufacturing of fashion products. Clothing and apparel brands are constantly looking for new ways to get their goods in front […].
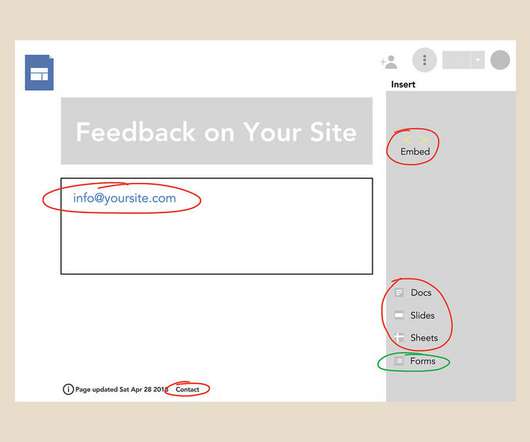
Tech Republic Cloud
JANUARY 2, 2020
Learn five ways to assemble information via a Google Site in this tutorial.

Speaker: Carolyn Clark and Miriam Connaughton
Forget predictions, let’s focus on priorities for the year and explore how to supercharge your employee experience. Join Miriam Connaughton and Carolyn Clark as they discuss key HR trends for 2025—and how to turn them into actionable strategies for your organization. In this dynamic webinar, our esteemed speakers will share expert insights and practical tips to help your employee experience adapt and thrive.

Forrester IT
DECEMBER 30, 2019
In October 2019, our team published its Predictions 2020: B2B Marketing And Sales, and in late December we recorded Webinar: B2B Marketing And Sales Predictions 2020: A Conversation With The Analysts Who Made Them. In the waning hours of 2019, Caroline Robertson and I took the opportunity to double-click into our sales enablement predictions. What […].

Anoop
JANUARY 3, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Great to start the year 2020 by announcing that this blog (www.anoopcnair.com) is part of Feedspot Top 20 SCCM blogs to follow in the year 2020. 😍😍😍👌👌 Subscribe to this blog NOTE! – Feedspot published this list of blogs in SCCM category even though Microsoft changed the name of SCCM to MEMCM.

CTOvision
JANUARY 2, 2020
Read Mary Shacklett explain how artificial intelligence fared in 2020 on Tech Republic : As more businesses realize the benefits of artificial intelligence (AI) in their daily operations, the demand for use cases will increase and drive the AI market. The leaps forward in AI will continue, as we see this young technology blossom into […].
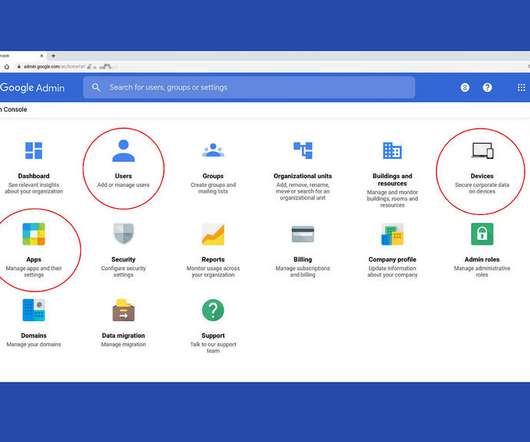
Tech Republic Cloud
JANUARY 2, 2020
Review your organization's G Suite settings to ensure they reflect company user, device, and app needs.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Forrester IT
DECEMBER 31, 2019
As the decade comes to a close, I thought it would be useful to reflect on how the retail industry has changed since 2010. With the wisdom of hindsight, we can now say what trends were rightfully chased and what claims were distractions that proved counterproductive. Two things rightfully received a lot of attention: Retail […].

Anoop
DECEMBER 30, 2019
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. This is the 3rd article of the Bitlocker series. Links to previous parts are mentioned below. Give them a read if you have not yet! Part 1 – Bitlocker Unlocked with Joy – Behind the Scenes Windows 10 Part 2 – Device Encryption – Bitlocker made Effortless Today in this post, we will be talking […].

CTOvision
JANUARY 2, 2020
Read Stephanie Overby list top 10 artificial trends to watch out for in 2020 on The Enterprisers Project : Artificial intelligence: Everybody’s doing it. Few are doing it well, however. In fact, nine out of ten companies have made some investment in AI, but 70 percent said they have seen minimal or no impact from AI […].

Information Week
JANUARY 3, 2020
Analyst firm ABI Research paired its upbeat predictions for tech concepts in 2020 with a real-world look at the ideas that aren't quite ready for prime time.

Advertiser: ZoomInfo
In this exploration, we're diving into predictions about the future of sales. We're talking about a complete shake-up powered by automation and artificial intelligence (AI). These aren't just fancy tools — they're real game-changers. Automation and AI are here to redefine every interaction, making them smarter, faster, and more meaningful. From personalized customer journeys to streamlined sales processes, the goal is to make every moment count, enhancing both efficiency and connection.

Forrester IT
DECEMBER 30, 2019
My colleagues Danny Mu, Guannan Lu and I attended Alibaba ONE Business Conference on December 18 in Hangzhou. The conference attracted 2,000 business leaders from brands across industries and focused on how Alibaba enables brands’ business growth with its digital ecosystem, data and technology capabilities, and business methodologies. Alibaba wrapped these tools, methods, and capabilities […].

Tech Republic Security
DECEMBER 29, 2019
If you find port 80 is a security risk on your network, you can change the Apache listening port to something non-standard.

CTOvision
DECEMBER 30, 2019
The federal government’s leading tech media brand FedScoop has just published an insightful look inside Palantir’s support to some of the Army’s most critical mission needs. The report dives into a recent contract award that aims to bring together a wide range of disparate data from unique and often totally disjointed systems to provide decision-makers […].

Mick's IT Blog
DECEMBER 31, 2019
I wanted to install the Configuration Manager PowerShell module on my admin machine. After investigating a little, the module does not exist in the Microsoft PowerShell gallery. The PowerShell script below will create the module directory under the WindowsPowerShellmodule directory within %PROGRAMFILES%. It will then copy over all of the necessary files.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

Forrester IT
DECEMBER 30, 2019
I believe most people who own credit cards have experienced fraud or false positives (non-fraud transaction declined), so did I. Three months ago, I have experienced an overseas credit card fraud with amount around 3,000 USD and my bank is still investigating the case now. What gave me a deeper impression was the complicated procedures […].

Tech Republic Security
JANUARY 2, 2020
E-commerce sites are trying to keep up with sophisticated skimming schemes, but chances are your credit card information will still be compromised. A security expert offers advice.

CTOvision
DECEMBER 30, 2019
Healthcare organizations are doing everything they can to modernize and digitally transform their organizations, but by many accounts, healthcare remains a laggard when it comes to digitization. And as a recent PwC report reads, “The question for 2020 will be whether this digital transformation will benefit consumers—marking a new dawn for the US health industry […].

Tech Republic Data Center
DECEMBER 31, 2019
Your best competitive asset might just be the one you already own. Walmart is using edge computing to compete against Amazon with data centers. Could your company use its assets to try something new?

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.
Let's personalize your content