Why Isn't Machine Learning Living up to the Hype?
Information Week
MARCH 18, 2020
An obsession with tasks is leading to marginal returns on tech investments. Now is the time to rethink our approaches to machine learning.

Information Week
MARCH 18, 2020
An obsession with tasks is leading to marginal returns on tech investments. Now is the time to rethink our approaches to machine learning.

Forrester IT
MARCH 20, 2020
Emotion is the most important dimension of CX quality — even for digital. Our CX Index™ data proves it. That goes double given the uncertainty of the COVID-19 pandemic. Read three ways to ensure you're delivering emotionally relevant CX during this difficult time.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Accidental Successful CIO
MARCH 18, 2020
Friending colleagues can be a tricky business Image Credit: Photo by Tim Bennett on Unsplash. So just exactly what is this “friendship” thing? For that matter how important is it? For most CIOs, friendship is very important. We’d all like to have as many friends as we possibly can. However, in this day and age we often indicate our friendship with someone by “friending” them in online social media sites.

CTOvision
MARCH 16, 2020
I received word yesterday of the passing, far too young, of Archie Clemins. He passed after a two year battle with cancer. Upon hearing of this terribly sad news I was overcome with a rush of memories, some of which I want to capture here for their valuable leadership lessons. Including lessons in enterprise technology […].

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Network World
MARCH 16, 2020
As the coronavirus spreads, many companies are requiring employees to work from home, putting unanticipated stress on remote networking technologies and causing bandwidth and security concerns. Businesses have facilitated brisk growth of teleworkers over the past decades to an estimated 4 million-plus. The meteoric rise in new remote users expected to come online as a result of the novel coronavirus calls for stepped-up capacity.

Forrester IT
MARCH 18, 2020
Today’s increasingly complex channel environment means once-reliable partner performance measurements such as revenue tiers, profit contribution, certifications, and customer satisfaction surveys fail to properly predict overall channel performance. To succeed, channel leaders must embrace techniques that will measure the expanding ecosystems’ influence on the entire buyer’s journey and not just the transaction.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

CTOvision
MARCH 17, 2020
Read Aaron Burciaga list the five core virtues for data science and artificial intelligence on Forbes : Virtues should be digitized. As we speed toward reliance on machines to process more and more information and provide cognitive support for all types of decision-making, we must consider ways to imbue automated processes, data machinations and recommender […].

Social, Agile and Transformation
MARCH 16, 2020
As I said in my last post, the world took a hard pivot right over the last couple of weeks. I'm reasonably sure that whatever you had planned to do this week is crossed out and replaced with a new plan and way of working. Many organizations closed their offices and working remotely. I ran a small poll on Twitter to snapshot the impact, and over 26% of respondents state that at least part.

Forrester IT
MARCH 20, 2020
Earlier this week, CX research directors David Truog and Harley Manning published a blog post that highlights two key points that I urge CX leaders who manage VoC programs to consider: understanding your customers is critical right now, and it is time to adapt your approach to CX. When it comes to your VoC program: […].

Anoop
MARCH 18, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s check how to create AppLocker Policies to Secure Windows Environments. These Applocker policies can help to build appropriate Windows Information Protection (WIP) using Intune. Introduction Applocker is introduced with the Windows 7 operating system, Windows Server 2008 R2.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

CTOvision
MARCH 16, 2020
Read Alyse Falk take a look at the impact of artificial intelligence on the Internet of Things on Toolbox : The Internet of Things (IoT) has been developing very quickly in the recent few years, it is expected that more devices will join the network in the future. Artificial intelligence goes hand in hand with […].

Network World
MARCH 15, 2020
Digital innovation is disrupting businesses. Data and applications are at the hub of new business models, and data needs to travel across the extended network at increasingly high speeds without interruption. To make this possible, organizations are radically redesigning their networks by adopting multi-cloud environments, building hyperscale data centers, retooling their campuses, and designing new connectivity systems for their next-gen branch offices.

Forrester IT
MARCH 16, 2020
Read the three essentials of customer experience that every organization should prioritize during the ongoing COVID-19 pandemic.

Anoop
MARCH 20, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s see how to Fix DCM Compliance Rules Error 0x87d00320 with Configuration Manager. Learn how to reate or build the Desired Configuration Management (DCM). Issue Description: When created a configuration item and targeted it using configuration baseline the rule fails to run and evaluate.

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.

CTOvision
MARCH 17, 2020
The cybersecurity industry has been targeted by technology and business leaders as one of the top advanced use cases for artificial intelligence (AI) and machine learning (ML) in the enterprise today. According to the latest studies, AI technology in cybersecurity is poised to grow over 23% annually through the second half of the decade. That’ll […].

Network World
MARCH 19, 2020
Cisco has issued five warnings about security weaknesses in its SD-WAN offerings, three of them on the high-end of the vulnerability scale. The worst problem is with the command-line interface (CLI) of its SD-WAN Solution software where a weakness could let a local attacker inject arbitrary commands that are executed with root privileges, Cisco wrote.

Forrester IT
MARCH 17, 2020
The adage says that character is what you do when no one’s watching. But as the internet’s gargantuan reach brings radical transparency to the critical eyes of values-based empowered customers, what you do when everyone is watching is even more important. And during a crisis like COVID-19, vigilance is at its peak. In addition to […].

Anoop
MARCH 16, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s check what you can do when you see the following error continuously. How to FIX Software Center Crash and Error SCNotification Has Stopped Working on Windows 10 devices. Introduction: We have seen this issue when opening software center, it crashes with below error.

Speaker: Miriam Connaughton and Donald Knight
As organizations scale, keeping employees connected, engaged, and productive can seem like a monumental task. But what if AI could help you do all of this and more? AI has the power to help, but the key is implementing it in a way that enhances, rather than replaces, human connection. Join us for an exploration into how industry trailblazers are using AI to transform employee experience at scale while addressing both the potential and the pitfalls.

CTOvision
MARCH 16, 2020
Read Abhishek Pareek explain the best examples of the Internet of Things solutions in the finance sector on Customer Think : In financial services, the Internet of Things (IoT) is considered the next big thing. IoT is a network of devices connected through the internet which obtain and transmit data. Internet of Things is the […].

Tech Republic Security
MARCH 17, 2020
The app promises access to a coronavirus map tracker but instead holds your contacts and other data for ransom, DomainTools found.

Forrester IT
MARCH 18, 2020
A recent debate on Twitter surrounding the ethics of organizations using COVID-19 as a theme for phishing exercises sparked our interest, since it relates to our coverages areas and prior work experience. In one of Brian’s prior jobs, he conducted the phishing exercises for the employees of one of the larger security companies. Claire covers […].
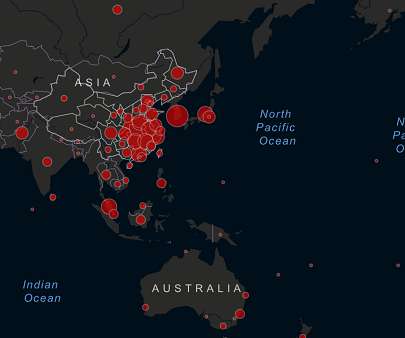
Trends in the Living Networks
MARCH 20, 2020
We can readily stop COVID-19 from spreading and reverse its path of devastation. It just requires health authorities and the government to track our every movement and everyone we come into contact with, with no exceptions. This is already happening to a substantial degree in a numnber of countries, and quite possibly has been a major factor in limiting the spread of the disease in some instances.

Speaker: Christophe Louvion, Chief Product & Technology Officer of NRC Health and Tony Karrer, CTO at Aggregage
Christophe Louvion, Chief Product & Technology Officer of NRC Health, is here to take us through how he guided his company's recent experience of getting from concept to launch and sales of products within 90 days. In this exclusive webinar, Christophe will cover key aspects of his journey, including: LLM Development & Quick Wins 🤖 Understand how LLMs differ from traditional software, identifying opportunities for rapid development and deployment.

CTOvision
MARCH 16, 2020
The endCoronavirus.org organization is built and maintained by the New England Complex Systems Institute (NECSI) and collaborators. The goal of this group of volunteers is to minimize the impact of the Coronavirus COVID-19 by providing useful data and guidelines for action. I’m amazed, really, at how they have been helping government’s understand better what to […].

Tech Republic Security
MARCH 19, 2020
Malicious COVID-19 domains and special virus-themed sales on the dark web are two ways criminals are using the outbreak to ramp up business, said security provider Check Point.

Forrester IT
MARCH 17, 2020
To understand how Forrester’s predictions will unfold in the retail industry in 2020, my colleague Madeline Cyr and I interviewed experts within Forrester for our “Applying 2020 Predictions To Retail” series. To understand the B2C marketing predictions for the year, we spoke with Forrester experts Tina Moffett and Jim Nail. Madeline Cyr: You predict that […].

Information Week
MARCH 19, 2020
Business intelligence will move beyond dashboards, and AI and machine learning will become easier for less skilled workers as augmented analytics are embedded into platforms.

Advertisement
There’s no getting around it: selecting the right foundational data-layer components is crucial for long-term application success. That’s why we developed this white paper to give you insights into four key open-source technologies – Apache Cassandra®, Apache Kafka®, Apache Spark™, and OpenSearch® – and how to leverage them for lasting success. Discover everything you’ll want to know about scalable, data-layer technologies: Learn when to choose these technologies and when to avoid them Explore h

CTOvision
MARCH 18, 2020
Join OODA CEO Matt Devost and CTO Bob Gourley on 19 March 2020 at 2pm Eastern for an interactive discussion on managing through the COVID-19 Crisis. This online zoom based discussion is for OODA members as well as any who registered for our OODAcon Future Proof. If you did not receive your invite, Contact us here. In this […].

Tech Republic Security
MARCH 19, 2020
The suspicious network activities revealed in the research by Positive Technologies are traffic hiding, VPN tunneling, connections to the Tor anonymous network, and network proxying.

Forrester IT
MARCH 17, 2020
In the midst of the coronavirus pandemic, many businesses are asking, or mandating, that office-based employees work from home. Millions of employees who have been logging in from workstations on corporate networks are now logging in from home or elsewhere on public networks. Stronger authentication, and VPNs, that used to be required for a subset […].

Tech Republic Cloud
MARCH 16, 2020
Dozens of digital productivity and collaboration tool providers like Microsoft and Zoom have seen massive upticks in usage across China, Italy, and the US because of the coronavirus.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.
Let's personalize your content