6 Ways to Manage Cybersecurity Burnout and Support Teams Better
Information Week
JUNE 13, 2023
Burnout is a contributing factor to the cybersecurity talent shortage. How can this issue be recognized and managed to help teams thrive?

Information Week
JUNE 13, 2023
Burnout is a contributing factor to the cybersecurity talent shortage. How can this issue be recognized and managed to help teams thrive?

TechSpot
JUNE 15, 2023
Experts at cybersecurity firm CyberCX unintentionally put themselves in this exact situation. Old Lenovo L440 laptops the company used in the past had their BIOS "conveniently locked" once the devices were decommissioned. The experts decided to use the computers as test subjects to learn how to break through BIOS passwords.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IT Toolbox
JUNE 14, 2023
Moving beyond the myths around PBAC to deliver broader security strategies. The post Debunking 5 Myths about Policy-based Access Control appeared first on Spiceworks.

Forrester IT
JUNE 15, 2023
Change fatigue is not about stamina; it’s about a lack of perceived value. Read this blog to learn the key steps to stop fatigue from creeping into your transformation journey.

Advertiser: ZoomInfo
Sales and marketing leaders have reached a tipping point when it comes to using intent data — and they’re not looking back. More than half of all B2B marketers are already using intent data to increase sales, and Gartner predicts this figure will grow to 70 percent. The reason is clear: intent can provide you with massive amounts of data that reveal sales opportunities earlier than ever before.

Social, Agile and Transformation
JUNE 12, 2023
Sponsored by Verizon A successful hybrid work program includes effective online collaboration and information sharing so remote workers can be productive at home and feel like they are contributing as much as their onsite colleagues Upgrading remote work solutions is an important first step to improving employee experiences, enabling near-real-time issue

The Accidental Successful CIO
JUNE 14, 2023
CIOs need to make AI less mysterious when it comes to hiring Image Credit: Steve Jurvetson The hiring process at any company is a complex undertaking. CIOs are often involved in the mechanics of how the process works. With the arrival of artificial intelligence (AI) technology, AI is now being incorporated into many of the tools that companies are using as a part of their hiring process.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

IT Toolbox
JUNE 12, 2023
Uncover the keys to employee engagement in the digital-first workplace. The post The Great Disengagement: What Is It and How Can Employers Fix It? appeared first on Spiceworks.

Forrester IT
JUNE 15, 2023
Read about the four categories of insights that portfolio marketers should consider when aiming to advance business outcomes, drive customer experiences, and support their organization’s growth strategy.

Tech Republic Big Data
JUNE 15, 2023
Learn all about Microsoft Dataverse in this comprehensive overview. Discover its features, benefits, and how it can enhance your data management. The post What is Microsoft Dataverse: A comprehensive overview appeared first on TechRepublic.
Tech Republic Security
JUNE 16, 2023
Threat intelligence firm Abnormal Software is seeing cybercriminals using generative AI to go phishing; the same technology is part of the defense. The post AI vs AI: Next front in phishing wars appeared first on TechRepublic.

Advertiser: GEP
For years, you and your team have fought an uphill battle. Supply disruptions. Cost pressures. ESG compliance. You name it, and you’ve had to navigate it. In 2025, many challenges will persist, but procurement and supply chain teams have a powerful tool with rapidly advancing capabilities to tackle them — artificial intelligence (AI). The GEP Outlook 2025 report examines the disruptive transformation AI is driving in procurement and supply chains, alongside other key trends and the macroeconomic
IT Toolbox
JUNE 15, 2023
Research shows that manufacturers are competing on the quality of CX, not just the quality of their products. The post How Better CX Can Solve Supply Chain Issues in Manufacturing appeared first on Spiceworks.

Forrester IT
JUNE 14, 2023
Enterprise business intelligence (BI) continues to be the last mile to insights-driven business (IDB) capabilities. No matter what technology foundation you’re using – a data lake, a data warehouse, data fabric, data mesh, etc. – BI applications are where business users consume data and turn it into actionable insights and decisions.

Anoop
JUNE 15, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post Account-Driven Apple User Enrolment in Intune – Part 1 appeared first on HTMD Community Blog #1 Modern Device Management Guides by Malepati Naren.

Tech Republic Security
JUNE 13, 2023
Read the technical details about a new AiTM phishing attack combined with a BEC campaign as revealed by Microsoft, and learn how to mitigate this threat. The post New phishing and business email compromise campaigns increase in complexity, bypass MFA appeared first on TechRepublic.

Speaker: Carolyn Clark and Miriam Connaughton
Forget predictions, let’s focus on priorities for the year and explore how to supercharge your employee experience. Join Miriam Connaughton and Carolyn Clark as they discuss key HR trends for 2025—and how to turn them into actionable strategies for your organization. In this dynamic webinar, our esteemed speakers will share expert insights and practical tips to help your employee experience adapt and thrive.

IT Toolbox
JUNE 14, 2023
Centralized master data management (MDM) solutions offer companies high levels of flexibility and customization. The post Take Control of Your Supply Chain With Master Data Management appeared first on Spiceworks.

Forrester IT
JUNE 15, 2023
For those of us old enough to remember “The Jetsons” — or those of us young enough to consider the science-fantasy series from the ’60s as “retro cool” — it was always fun to watch George Jetson spend his workday pushing the single red button on his computer.
Information Week
JUNE 12, 2023
Is it time to put out a welcome mat for AI, or is the technology about to pull the rug out from under humanity? Opinions differ, to say the least.

Anoop
JUNE 14, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post First Windows 11 Controlled Feature Rollout Coming Soon appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

IT Toolbox
JUNE 15, 2023
Harness the power of language diversity for enhanced innovation, cross-cultural communication, and market adaptation. The post How Language Diversity Boosts Innovation In Tech Teams appeared first on Spiceworks.
Forrester IT
JUNE 15, 2023
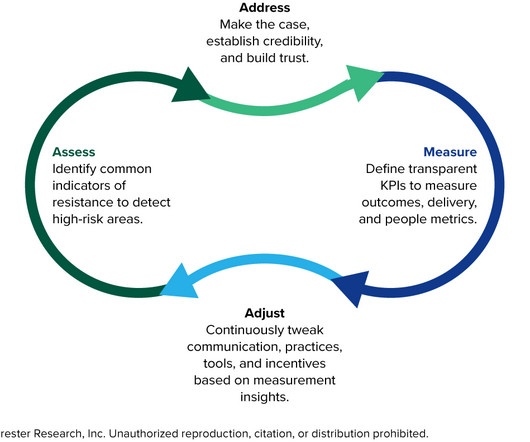
Change resistance can derail be best transformation roadmap. Read this blog to learn about the most common mistakes to avoid.

Information Week
JUNE 12, 2023
What to look for when reevaluating your team’s tech stack will depend on where your artificial intelligence solution best fits the team’s workflow. Here are a few ideas.

Anoop
JUNE 13, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post Microsoft Defender for Endpoint Portal Walkthrough appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.

Advertiser: ZoomInfo
In this exploration, we're diving into predictions about the future of sales. We're talking about a complete shake-up powered by automation and artificial intelligence (AI). These aren't just fancy tools — they're real game-changers. Automation and AI are here to redefine every interaction, making them smarter, faster, and more meaningful. From personalized customer journeys to streamlined sales processes, the goal is to make every moment count, enhancing both efficiency and connection.

IT Toolbox
JUNE 15, 2023
Can business transformation and ESG goals be attained together? The post 5 Keys to Unlock Healthy ESG and Business Transformation appeared first on Spiceworks.

Forrester IT
JUNE 16, 2023
If there’s a hair’s breadth between keeping pace and treading water, the US health insurance industry is balancing right on it.

Information Week
JUNE 15, 2023
Generative AI is now automating the creation of written content, but the new technology also requires guardrails, experts say.

Anoop
JUNE 16, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post MDE Network Protection Policy Deployment using Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

IT Toolbox
JUNE 15, 2023
AWS launched Amazon CodeGuru Security, Amazon Verified Access, Amazon Verified Permissions, and more at AWS re:Inforce 2023. The post AWS re:Inforce 2023: Key Highlights From the Cloud Security Event appeared first on Spiceworks.

Forrester IT
JUNE 15, 2023
Storage is a fundamental element of enterprise compute. Everyone’s data must go somewhere. Up until recently, mechanical spinning disk has been the default storage media for very large data needs. Flash media has steadily eaten away at the hard-disk footprint in the data center, however. Originally, flash attacked performance-oriented workloads.

Information Week
JUNE 15, 2023
A focus on nature represents the next stage of environmental, social, and corporate governance (ESG). Here’s what businesses need to know.

Tech Republic Security
JUNE 15, 2023
FBI, CISA and international organizations released an advisory detailing breadth and depth of LockBit, and how to defend against the most prevalent ransomware of 2022 and (so far) 2023. The post CISA advisory on LockBit: $91 million extorted from 1,700 attacks since 2020 appeared first on TechRepublic.

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.
Let's personalize your content