Using Analytics to Improve IT Operations and Services
Information Week
APRIL 30, 2020
Analytics has already enhanced an array of business functions. Now it's IT's turn to benefit from analytics-driven insights.

Information Week
APRIL 30, 2020
Analytics has already enhanced an array of business functions. Now it's IT's turn to benefit from analytics-driven insights.

Forrester IT
MAY 1, 2020
In January of 2020, we launched our inaugural “Future of the CISO” report, which identified the “Six Types of CISOs” we discovered through our research. At its release, we received copious amounts of feedback – some we had considered, and some we hadn’t. However, while we were conducing our research, the omnipresent event we know […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Accidental Successful CIO
APRIL 29, 2020
Robotic Process Automation is coming, will CIOs be ready? Image Credit: Photo by Rock’n Roll Monkey on Unsplash. As the person with the CIO job at your company, you are constantly under pressure to understand the importance of information technology and to find ways to allow the company to do more things quicker. You’ve probably already done the simple things such as deploying a group chat application, installing an ERP suite, and, of course, putting in countless firewalls to keep th

Information Week
MAY 1, 2020
One of the biggest mistakes a leader can make is blindly following a prescriptive list of one-size-fits-all tips and solutions for remote work.

Advertiser: ZoomInfo
Sales and marketing leaders have reached a tipping point when it comes to using intent data — and they’re not looking back. More than half of all B2B marketers are already using intent data to increase sales, and Gartner predicts this figure will grow to 70 percent. The reason is clear: intent can provide you with massive amounts of data that reveal sales opportunities earlier than ever before.

CTOvision
APRIL 27, 2020
Read Shinie Bentotahewa and Chaminda Hewage take a look at the challenges and obstacles faced by Big Data applications due to the GDPR on Infosec Magazine : The primary focus of the General Data Protection Regulation (GDPR) framework is on protecting the rights of individuals to privacy, without compromising their personal data stored by state […].

Forrester IT
APRIL 30, 2020
The topic of CISO burnout has been something I’ve wanted to write about for a while. It is something I speak about to CISOs around the world regularly. Even before COVID-19, CISOs had a stressful job. They were already dealing with bureaucracy, internal politics, lack of organizational support, and the constant feeling that they would be […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Tech Republic Security
APRIL 28, 2020
Conscious of the state of employment during the pandemic, as well as after, Fortinet offers an opportunity to build skill sets from home.

CTOvision
APRIL 28, 2020
Read why Danny Palmer says that artificial intelligence can be used for cyberattacks on ZDNet : Intelligence and espionage services need to embrace artificial intelligence (AI) in order to protect national security as cyber criminals and hostile nation states increasingly look to use the technology to launch attacks. The UK’s intelligence and security agency GCHQ commissioned […].

Forrester IT
APRIL 30, 2020
With the ever-changing economic landscape, Forrester’s Forecastview team developed a scenario model to understand the short- and long-term impacts of COVID-19 on the retail industry. Our model examines three scenarios; a base case, best case, and worst case, which estimate retail sales at global and regional levels for the total, online, and offline space.

Information Week
APRIL 28, 2020
These are the programming languages most likely to be used in enterprise IT and most likely to help you get a job.

Advertiser: GEP
For years, you and your team have fought an uphill battle. Supply disruptions. Cost pressures. ESG compliance. You name it, and you’ve had to navigate it. In 2025, many challenges will persist, but procurement and supply chain teams have a powerful tool with rapidly advancing capabilities to tackle them — artificial intelligence (AI). The GEP Outlook 2025 report examines the disruptive transformation AI is driving in procurement and supply chains, alongside other key trends and the macroeconomic

Anoop
APRIL 29, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. In this post, let’s learn How to Configure ConfigMgr Preferred MP. You can learn more about Preferred Management Points selection Criteria from the client perspective. Introduction – Configure ConfigMgr Preferred MP Microsoft official released Preferred Management points in SCCM 2012 R2 SP1 or SCCM 2012 SP2 version.

CTOvision
APRIL 27, 2020
US Northern Command overseas DoD actions in the anti-Covid19 fight inside the US. There are many moving parts in an operation this size, making command and control and decision-making a critical component of success. Technology is critical to success in this operation. Decades of experience in tech support to military operations leaves me with both […].

Forrester IT
APRIL 30, 2020
Publicis Groupe announced today the creation of “The Pact, Powered by Epsilon,” a new digital media planning and buying service that offers “money-back performance commitments” that guarantee the business outcomes from digital marketing campaigns. The introduction of The Pact is a timely move to give brands a mechanism to manage the risk of marketing during […].

All Things Distributed
APRIL 27, 2020
The global healthcare pandemic has been like nothing many of us in Europe have ever known. During this time, many organizations have been contemplating their role in the COVID-19 crisis, and how they can best serve their communities. I can tell you it has been no different for us at Amazon Web Services (AWS). We are focused on where we can make the biggest difference, to help the global communities in which we all live and work.

Speaker: Carolyn Clark and Miriam Connaughton
Forget predictions, let’s focus on priorities for the year and explore how to supercharge your employee experience. Join Miriam Connaughton and Carolyn Clark as they discuss key HR trends for 2025—and how to turn them into actionable strategies for your organization. In this dynamic webinar, our esteemed speakers will share expert insights and practical tips to help your employee experience adapt and thrive.

Anoop
APRIL 30, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Well, the single pane of glass is back again for Configuration Manager and Intune customers. With SCCM 2002 or later version, you can sync ConfigMgr Devices to Intune. Let’s learn how to build sync between SCCM Intune Portal. This is also referred to as Tenant attach.

CTOvision
APRIL 27, 2020
Read why Remko van Hoek and Mary Lacity say that CoronaVirus pandemic is actually helping in adapting blockchain technology on Harvard Business Review : Because blockchain technologies are uniquely suited to verifying, securing and sharing data, they’re ideal for managing multi-party, inter-organizational, and cross-border transactions. Over the past five years, enterprises across the globe have […].

Forrester IT
APRIL 29, 2020
Commerce vendors are busy consulting to their clients to keep retail — online and offline — moving as best possible during the pandemic. Now some of those big-name vendors are helping small businesses adapt quickly through Keep Small Strong, an organization that didn’t exist until a little over a month ago. The organization’s mission is […].

Information Week
MAY 1, 2020
Remote work and communication styles that arise with it will not disappear after the current pandemic concerns ease. Here's how IT teams can play a vital role in managing this.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?
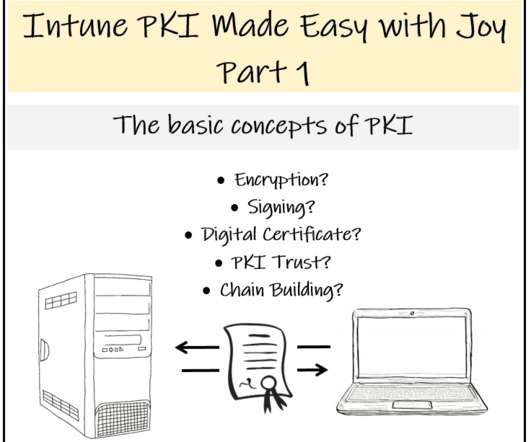
Anoop
APRIL 27, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. [New Post Alert!] Learn the Basic Concepts of PKI - Intune PKI Made Easy with Joy (Part 1). The post Learn The Basic Concepts of PKI – Intune PKI Made Easy With Joy Part-1 appeared first on How to Manage Devices by Joymalya Basu Roy.

CTOvision
APRIL 28, 2020
In this second of a two part OODAcast, OODA CTO Bob Gourley, was joined by Lewis Shepherd, seasoned federal technology executive and a senior director of technology strategy at VMware for an interactive discussion on the actionable lessons we should all be learning from the current crisis but also how the events of today are […].

Forrester IT
APRIL 27, 2020
Small businesses globally are experiencing a serious credit crunch from COVID-19 lockdowns. Many small and medium-sized businesses sit on little if any cash reserves and some have already lost most of their revenue; but they still have to pay their bills, maintain their supply chain, compensate their employees, and repay their debts. Millions of businesses […].

Information Week
APRIL 27, 2020
The sheer scope of AI's impact on society does require some regulation. It will be essential to ensure that AI regulation is fair and ethical while not impeding innovation.

Advertiser: ZoomInfo
In this exploration, we're diving into predictions about the future of sales. We're talking about a complete shake-up powered by automation and artificial intelligence (AI). These aren't just fancy tools — they're real game-changers. Automation and AI are here to redefine every interaction, making them smarter, faster, and more meaningful. From personalized customer journeys to streamlined sales processes, the goal is to make every moment count, enhancing both efficiency and connection.

Anoop
APRIL 28, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. A quick draft about “SCCM Client Agent Installation and Health validation PowerShell Script” there is a lot of ways to install the ConfigMgr client agent automatically, Client push via SCCM console, GPO’s, and many more options. NOTE! – GPO needs to be created as a logon script.

CTOvision
APRIL 26, 2020
In this two part OODAcast, OODA CTO Bob Gourley was joined by Lewis Shepherd, seasoned federal technology executive and a senior director of technology strategy at VMware for an interactive discussion on the actionable lessons we should all be learning from the current crisis but also how the events of today are shaping the future […].
Forrester IT
APRIL 29, 2020
With much of the business world working remotely due to COVID-19, reaching potential buyers through digital channels is now critical to B2B marketing success. But with everyone doing “virtual” everything, how do you cut through the noise to engage your target audience?

Tech Republic Security
APRIL 29, 2020
Application Guard for Office and Safe Documents will make phishing attacks harder and the Office experience better for users, starting with Office 365 Pro Plus and E5 licences.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

Anoop
MAY 1, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. This is a step by step guide to install Root CA and Sub-Ordinate CA installation. Install Certificate Server – ROOT CA and Sub-Ordinate CA. This Installation is an Offline method for non-trusted domains. This helps to install CA Servers for SCCM PKI/Internet clients, creating Certificate templates and How to Configure GPO for Certificate auto-enrollment.

CTOvision
MAY 1, 2020
In this OODAcast, OODA CTO Bob Gourley was joined by Dr. Jane Melia of QuintessenceLabs to dive deep into topics of Quantum Computing, Quantum Security and best practices for ensuring […].

Forrester IT
APRIL 30, 2020
The etymology of the term crisis refers in Latin to a “turning point in a disease, that change which indicates recovery or death”, but comes in fact from the ancient Greek krinein “to judge” By analogy, the massive economic crisis that will follow Covid-19 will dramatically accelerate existing gaps in how companies have adapted to […].

Tech Republic Security
APRIL 30, 2020
Attackers used an account checker tool to identify Nintendo accounts with compromised and vulnerable login credentials, says SpyCloud.

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.
Let's personalize your content