Scaling AI: The 4 challenges you’ll face
Venture Beast
FEBRUARY 14, 2021
I've worked in big data and AI with several organizations. Here's where I've seen them flounder after an enthusiastic start. Read More.

Venture Beast
FEBRUARY 14, 2021
I've worked in big data and AI with several organizations. Here's where I've seen them flounder after an enthusiastic start. Read More.

Forrester IT
FEBRUARY 18, 2021
One of the top challenges and misunderstandings that I continue to see here at Forrester is about what the definition of Zero Trust actually is. Zero Trust is not one product or platform; it’s a security framework built around the concept of “never trust, always verify” and “assuming breach.” Attempting to buy Zero Trust as […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
FEBRUARY 15, 2021
Planning a data model takes a clear look at how variables should be used. A few techniques like factor analysis can help IT teams develop an efficient means to manage a model. Here's how.

CTOvision
FEBRUARY 15, 2021
Crypto startup The Graph has announced it is exploring providing support for additional layer-one blockchains, including Bitcoin, Polkadot and NEAR. The potential integrations, which comes over a month after The Graph […].

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Anoop
FEBRUARY 18, 2021
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s understand the ConfigMgr Client Action called Software Updates Scan Cycle in a bit more. Read More ConfigMgr Software Updates Scan Cycle Client Action | SCCM. The post ConfigMgr Software Updates Scan Cycle Client Action | SCCM appeared first on How to Manage Devices by Anoop C Nair.

Forrester IT
FEBRUARY 16, 2021
Tell Us About You I have a background in computer engineering, and over the past 10 years I’ve been in engineering and consulting roles at organizations like MIT and a variety of startups. I live in New York City and love to read, do yoga, and learn new languages. In normal, non-pandemic times, I’m an avid traveler, though that has obviously […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

CTOvision
FEBRUARY 15, 2021
Read Lenley Hensarling, chief strategy officer at Aerospike explain to Tom Taulli that mainframe or legacy systems are here to stay for another 30 to 40 years on Forbes : […].

Anoop
FEBRUARY 15, 2021
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s understand how to fix ConfigMgr Power BI Report Unexpected Error. I was not able. Read More Fix ConfigMgr Power BI Report Unexpected Error | SCCM. The post Fix ConfigMgr Power BI Report Unexpected Error | SCCM appeared first on How to Manage Devices by Anoop C Nair.

Forrester IT
FEBRUARY 16, 2021
Forrester’s take on the SASE model This is big, folks. This is really big. Bigger than Gamestop. Even bigger than Heeleys (the adult version saved in my Amazon wish list). This could be the biggest technological transformation since sliced bread, Dorito tacos, or public cloud. A year ago, fellow Forrester analyst Andre Kindness and I […].

Information Week
FEBRUARY 18, 2021
While DevOps as a practice is evolving, so are the roles within a DevOps team. Following are an explanation of some of the trends worth watching.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

CTOvision
FEBRUARY 18, 2021
Read Byron Rashed explain how Centripetal CleanINTERNET recently applied cyber threat intelligence to defend a SonicWall VPN host from over 400,000 attack attempts on their blog: Centripetal Networks observed 472,584 […].

Anoop
FEBRUARY 19, 2021
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s check what is the Best Option to Deploy Zoom Application Using SCCM (a.k.a Configuration. Read More How to Deploy Zoom Application using SCCM | ConfigMgr. The post How to Deploy Zoom Application using SCCM | ConfigMgr appeared first on How to Manage Devices by Anoop C Nair.

Forrester IT
FEBRUARY 15, 2021
The COVID-19 pandemic has catalyzed the need for change in customer service organizations – changes in the ways we work, we hire new talent, we invest in new technology, and in the way we practice risk management. We are all aware of the operational holes that were exposed when contact centers moved agents home in […].

Network World
FEBRUARY 16, 2021
Palo Alto had a busy week. First, it rolled out a number of new features for its Prisma cloud-based security package, and then it announced plans to buy cloud security vendor Bridgecrew for about $156 million in cash. Palo Alto's Prisma is a cloud-based security package that includes access control, advanced threat protection, user behavior monitoring and other services that promise to protect enterprise applications and resources.

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.

CTOvision
FEBRUARY 18, 2021
Read Jude Lopez explain why he is bullish on Ethereum and Chainlink compared to Bitcoin on AMB Crypto: The past week saw Bitcoin’s price surge by over 18 percent, with […].

Tech Republic Cloud
FEBRUARY 17, 2021
As companies prepare to make remote working permanent, cultural change will play a crucial role in building new, successful work environments.

Forrester IT
FEBRUARY 17, 2021
How many buyers really use the website? This was a question asked in a recent conversation with a consulting services client. It was asked in response to a critique of the website. My analysis showed how difficult it was for a buyer to understand digital business transformation services from the firm’s website. It’s perhaps not […].

Tech Republic Security
FEBRUARY 17, 2021
Machine learning is helpful to many organizations in the tech industry, but it can have a downside. Tom Merritt lists five things to know about adversarial attacks.

Speaker: Miriam Connaughton and Donald Knight
As organizations scale, keeping employees connected, engaged, and productive can seem like a monumental task. But what if AI could help you do all of this and more? AI has the power to help, but the key is implementing it in a way that enhances, rather than replaces, human connection. Join us for an exploration into how industry trailblazers are using AI to transform employee experience at scale while addressing both the potential and the pitfalls.

CTOvision
FEBRUARY 15, 2021
Wickr announced the general availability of “Global Federation”, a feature that will allow enterprise and government entities to securely communicate using end-to-end encryption (E2EE) with individual users and mission-critical partners […].

Tech Republic Cloud
FEBRUARY 17, 2021
Expect big growth for cloud financial-management--FinOps--as the enterprise speeds its cloud expansion, while struggling to contain and optimize cloud spend, according to new research.
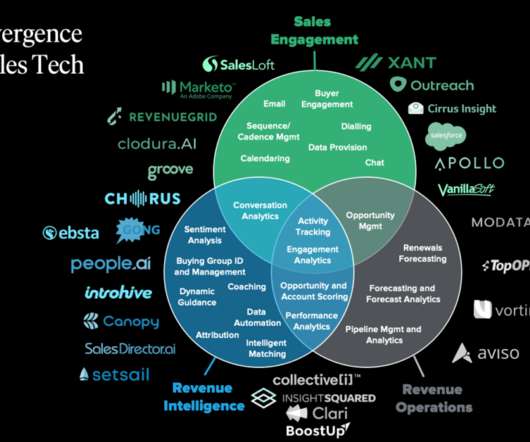
Forrester IT
FEBRUARY 18, 2021
How do sales leaders, sales operations, and sales enablement practitioners navigate their way through an increasingly crowded technology space?

Tech Republic Security
FEBRUARY 19, 2021
Hackers are now sending messages that hide fake links in the HTTP prefix, bypassing email filters, says security firm GreatHorn.

Speaker: Christophe Louvion, Chief Product & Technology Officer of NRC Health and Tony Karrer, CTO at Aggregage
Christophe Louvion, Chief Product & Technology Officer of NRC Health, is here to take us through how he guided his company's recent experience of getting from concept to launch and sales of products within 90 days. In this exclusive webinar, Christophe will cover key aspects of his journey, including: LLM Development & Quick Wins 🤖 Understand how LLMs differ from traditional software, identifying opportunities for rapid development and deployment.

CTOvision
FEBRUARY 18, 2021
The attack on the water treatment facility located in Oldsmar, Florida, disclosed last week highlights security shortages in the water utility sector and the rest of the U.S. critical infrastructure […].

Information Week
FEBRUARY 16, 2021
As younger generations infiltrate the workplace, we'll see companies deploy technology to fill the skills gap, train remote workers and drive real-life applications.
Forrester IT
FEBRUARY 19, 2021
Since April 2020, we have estimated how the retail economies of 30 major US metropolitan areas are recovering from COVID-19. By aggregating 11 metrics (across retail sales, local economic indicators, and virus spread), our model predicts that these metropolitan areas will face differing levels of COVID-19 disruption. For these metrics, we looked at US metropolitan-, […].
Tech Republic Security
FEBRUARY 17, 2021
Information protection makes sure that only people with permissions see data in Power BI, while retaining the ability to share top-level trends, balancing productivity and security.

Advertisement
There’s no getting around it: selecting the right foundational data-layer components is crucial for long-term application success. That’s why we developed this white paper to give you insights into four key open-source technologies – Apache Cassandra®, Apache Kafka®, Apache Spark™, and OpenSearch® – and how to leverage them for lasting success. Discover everything you’ll want to know about scalable, data-layer technologies: Learn when to choose these technologies and when to avoid them Explore h

CTOvision
FEBRUARY 19, 2021
Just 6 days ago we were pointing out the rise of Bitcoin, which at the time was at number 9 on the list of top global assets. It has now […].

Tech Republic Cloud
FEBRUARY 18, 2021
One company has created a solution to merge the diverse cloud and analytics tools organizations juggle. Here's hoping there will be more unity to come.

Information Week
FEBRUARY 18, 2021
Customers flocked to digital channels and faced life-changing events in 2020. Here's how enterprise companies are changing their CRM practices for a new normal.

Tech Republic Security
FEBRUARY 16, 2021
Analysts from Trend Micro rate DDoS attacks and electronic jamming as some of the highest cybersecurity risks for connected cars.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.
Let's personalize your content