How DevOps Teams Get Automation Backwards
Information Week
NOVEMBER 16, 2020
Will automation speed up your processes, or will you end up with a brittle system that will demand constant attention and frequent, time-consuming fixes?

Information Week
NOVEMBER 16, 2020
Will automation speed up your processes, or will you end up with a brittle system that will demand constant attention and frequent, time-consuming fixes?

CTOvision
NOVEMBER 18, 2020
Zoom on Monday released new features designed to remove and report “Zoombombers,” or uninvited attendees who break into and disrupt meetings. The features are available on the Zoom desktop clients […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Forrester IT
NOVEMBER 18, 2020
It’s not that I’m not a gamer. I enjoy board games and card games: Trivial Pursuit, Settlers Of Catan, SET, Hive. I’m up to level 3056 in Two Dots. As a kid, I played Super Mario Land on my brother’s GameBoy and Sonic The Hedgehog on the family Sega Genesis. But I’ve never been one […].

Association of Information Technology Professional
NOVEMBER 18, 2020
CompTIA PenTest+ is now approved by the U.S. Department of Defense (DoD) 8570 for three cybersecurity job categories.

Advertiser: ZoomInfo
Sales and marketing leaders have reached a tipping point when it comes to using intent data — and they’re not looking back. More than half of all B2B marketers are already using intent data to increase sales, and Gartner predicts this figure will grow to 70 percent. The reason is clear: intent can provide you with massive amounts of data that reveal sales opportunities earlier than ever before.

Information Week
NOVEMBER 17, 2020
Across industries, big data has joined traditional, structured data as a mission-critical element. Here's some advice for CIOs and big data leaders on how to get started.

CTOvision
NOVEMBER 18, 2020
Bring Your Own Device (BYOD) used to be an emerging trend in the workplace, one that allowed professionals a bit more flexibility and comfort by using their personal computers and […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Association of Information Technology Professional
NOVEMBER 18, 2020
Learn about the cybersecurity industry for beginners and how you can further your cybersecurity career with IT certifications like CompTIA Security+.

Information Week
NOVEMBER 18, 2020
CIOs will have a host of cloud options to choose from in 2021 as the cloud business evolves, according to a new Forrester Research report.

CTOvision
NOVEMBER 18, 2020
AT&T, the third largest mobile operator in the United States in terms of subscribers, has deployed a next-gen open dis-aggregated IP edge routing platform with support from Broadcom, Cisco, and […].

Forrester IT
NOVEMBER 17, 2020
2020’s Remote Work Is The Exception No Business Wanted The sudden arrival of the COVID-19 pandemic has thrust every organization into a patchwork of unplanned workforce responses. Companies have had to quickly get as many of their personnel into a safe and productive work situation as possible, with most of them working remotely at least […].

Advertiser: GEP
For years, you and your team have fought an uphill battle. Supply disruptions. Cost pressures. ESG compliance. You name it, and you’ve had to navigate it. In 2025, many challenges will persist, but procurement and supply chain teams have a powerful tool with rapidly advancing capabilities to tackle them — artificial intelligence (AI). The GEP Outlook 2025 report examines the disruptive transformation AI is driving in procurement and supply chains, alongside other key trends and the macroeconomic

Association of Information Technology Professional
NOVEMBER 19, 2020
CompTIA’s IT Industry Outlook 2021, with the theme “Rebuilding for the Future,” provides 10 trends in technology for the year ahead. For those in the business of technology, here are four ways to leverage the insights from CompTIA's latest research.
Tech Republic Security
NOVEMBER 18, 2020
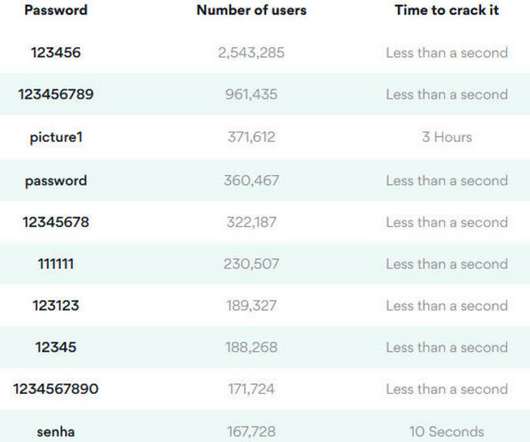
People are still using very simple passwords, with many of them similar to the ones they used in 2019, according to NordPass.

CTOvision
NOVEMBER 17, 2020
We enjoyed these insights from friend John Trauth of Bricata: The goal was to increase network visibility and eliminate the blind spots that exist in every company. My vision was […].

Forrester IT
NOVEMBER 20, 2020
Improving the competencies of their people is a priority for many functional leaders, but too many take shortsighted approaches that are unlikely to achieve the desired results. Jeff Lash explains the mistakes many companies make and four Forrester tips on how to make upskilling more impactful.

Speaker: Carolyn Clark and Miriam Connaughton
Forget predictions, let’s focus on priorities for the year and explore how to supercharge your employee experience. Join Miriam Connaughton and Carolyn Clark as they discuss key HR trends for 2025—and how to turn them into actionable strategies for your organization. In this dynamic webinar, our esteemed speakers will share expert insights and practical tips to help your employee experience adapt and thrive.

Association of Information Technology Professional
NOVEMBER 16, 2020
A recent CompTIA research study revealed the cybersecurity skills IT pros need to build their knowledge base and careers.
Tech Republic Security
NOVEMBER 20, 2020
IBM, Honeywell, and Intel are just three companies leading the way in building quantum machines as well as the algorithms and controls to run them. Learn about possible business use cases for quantum.

CTOvision
NOVEMBER 18, 2020
Wasabi, the hot cloud storage company, today announced a new partnership with DataCore Software, the authority on software-defined storage (SDS), to provide customers with a fast, practical, and cost-effective solution […].

Forrester IT
NOVEMBER 18, 2020
2020 has been a year of unprecedented political, social, economic, and healthcare disruption — and 2021 shows no signs of these trends slowing down. How should European consumer marketing leaders prepare for the coming year? They must get ready for a digital ecosystem with fewer third-party cookies and device identifiers, all while navigating an unpredictable […].

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Anoop
NOVEMBER 20, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. What are the most loved acronyms of SCCM ConfigMgr MEMCM MECM MEM? Let’s hear the favorite acronyms of ConfigMgr from the community. I’m always troubled to stick with one acronym for ConfigMgr because the community still use SCCM as the search word. Poll Results of 2018 Let’s check the voting initiated (Facebook Group with more […].

Tech Republic Security
NOVEMBER 16, 2020
Implementing appropriate data privacy is critical for company operations and success. Learn some of the challenges and solutions recommended to do the job right.

CTOvision
NOVEMBER 17, 2020
Ping Identity, the intelligent identity solution for the enterprise, today announced the launch of a Consumer Data Right (CDR) Integration Kit enabling Australian banks and fintech company data holders to […].

Forrester IT
NOVEMBER 18, 2020
Every year, more firms reach out to me to explain how they’re delivering their own brand of “digital transformation” to clients. When last I checked, I’m tracking over 170 vendors. Needless to say, some of these firms are much more adept at delivering effective transformation services than others. The simple truth is, almost every vendor […].

Advertiser: ZoomInfo
In this exploration, we're diving into predictions about the future of sales. We're talking about a complete shake-up powered by automation and artificial intelligence (AI). These aren't just fancy tools — they're real game-changers. Automation and AI are here to redefine every interaction, making them smarter, faster, and more meaningful. From personalized customer journeys to streamlined sales processes, the goal is to make every moment count, enhancing both efficiency and connection.

Information Week
NOVEMBER 19, 2020
While it may be counterintuitive to make sweeping changes to enterprise software strategies amid a pandemic, the payoff could be substantial in the long run.

Tech Republic Security
NOVEMBER 16, 2020
These hackers are finding security bugs--and getting paid for it. That's changing the dynamics of cybersecurity.

CTOvision
NOVEMBER 16, 2020
Read Asa Fitch take a look at how Intel Corporation has ended up outsourcing its chip-making business on Wall Street Journal: The Silicon Valley pioneer long held it had to […].

Forrester IT
NOVEMBER 19, 2020
Bad puns in the title of this blog post aside (queue the rolling of the eyes, sigh, and slight smirk), we are pleased to announce that “The Forrester Wave™: Privileged Identity Management (PIM), Q4 2020” is now live. While PIM vendors have been adding new capabilities and improved user experience over the past two years, […].

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

Information Week
NOVEMBER 20, 2020
Focus on the marathon, not the sprint. Here are three best practices for constructing effective, efficient dev teams.

Anoop
NOVEMBER 19, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. In this post, we learn about ConfigMgr Task Sequence OSD Multiple Physical Drives. Let’s try to understand how can we use conditions in the Task sequence to install operating systems via SCCM Task Sequence on a machine having dual drives. The below articles will give you an idea about the scenario which I have faced […].

CTOvision
NOVEMBER 17, 2020
Read how Pindrop helps in the Contact Center security through anomaly detection and fraud prevention on their blog: Fraud costs don’t start in your finance department. They start in your […].

Forrester IT
NOVEMBER 16, 2020
Consider Spending Changes In Five Categories Post-COVID-19 The business effects of the COVID-19 pandemic will be with us for years. However, the consequences of the pandemic are not identical for all companies. Different industries, including insurance, face disparate consumer trends, resource availability, and revenue potential during the pandemic and its aftermath.

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.
Let's personalize your content